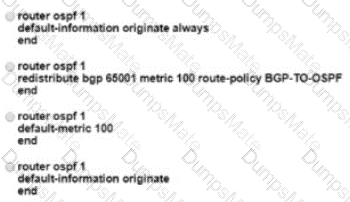
Explanation: Ransomware are malicious software that locks up critical resources of the users.
Ransomware uses well-established public/private key cryptography which leaves
the only way of recovering the files being the payment of the ransom, or restoring
files from backups.
Cisco Advanced Malware Protection (AMP) for Endpoints Malicious Activity
Protection (MAP) engine defends your endpoints by monitoring the system and
identifying processes that exhibit malicious activities when they execute and stops
them from running. Because the MAP engine detects threats by observing the
behavior of the process at run time, it can generically determine if a system is
under attack by a new variant of ransomware or malware that may have eluded
other security products and detection technology, such as legacy signature-based
malware detection. The first release of the MAP engine targets identification,
blocking, and quarantine of ransomware attacks on the endpoint.






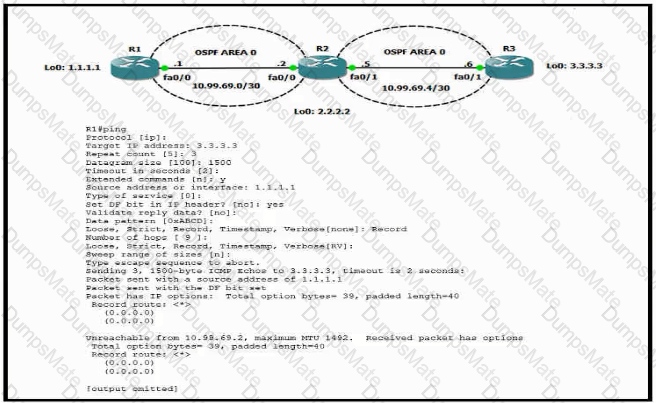


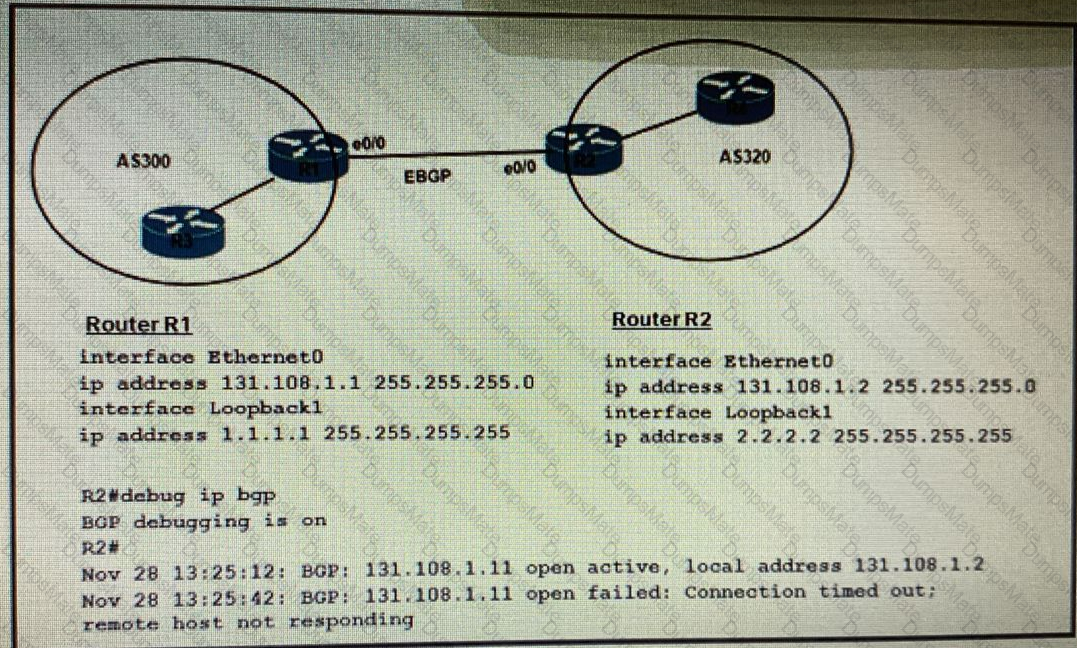
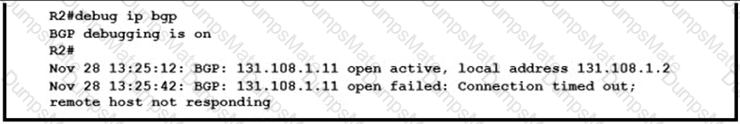
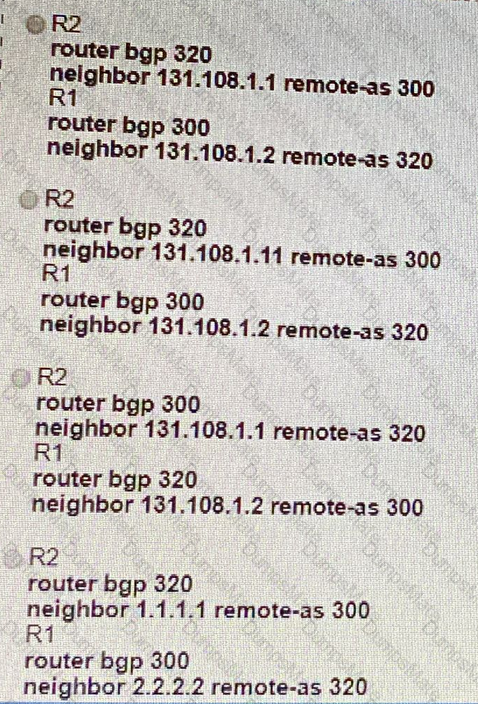




 A picture containing table
Description automatically generated
A picture containing table
Description automatically generated
 Graphical user interface, text, application, email
Description automatically generated
Graphical user interface, text, application, email
Description automatically generated







 Text, letter
Description automatically generated
Text, letter
Description automatically generated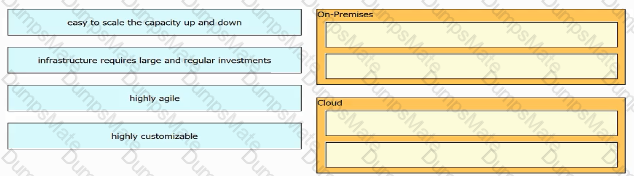
 Graphical user interface, application
Description automatically generated
Graphical user interface, application
Description automatically generated



 Graphical user interface, application
Description automatically generated
Graphical user interface, application
Description automatically generated
 C:\Users\SANJAY~1\AppData\Local\Temp\SNAGHTML492d5ca9.PNG
C:\Users\SANJAY~1\AppData\Local\Temp\SNAGHTML492d5ca9.PNG
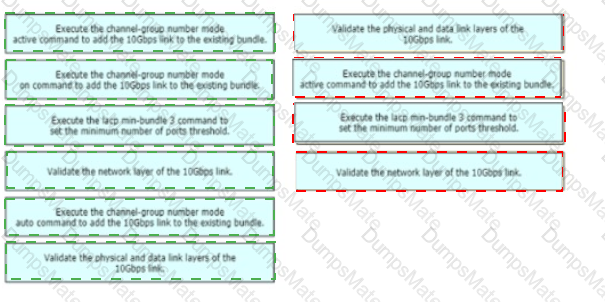
 A picture containing diagram
Description automatically generated
A picture containing diagram
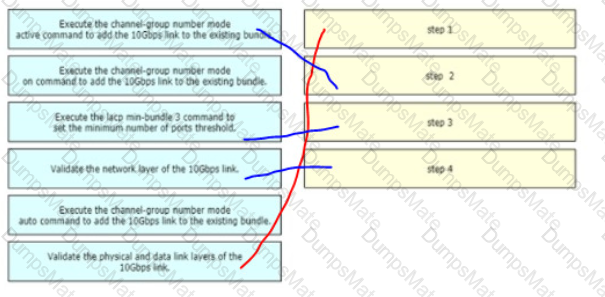
Description automatically generated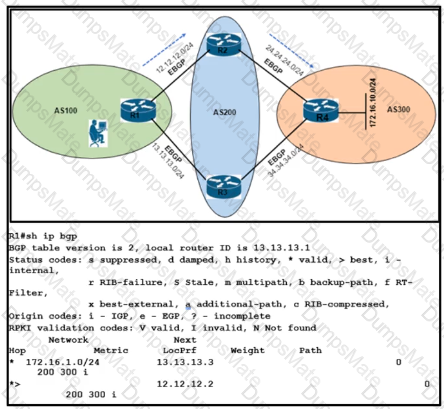
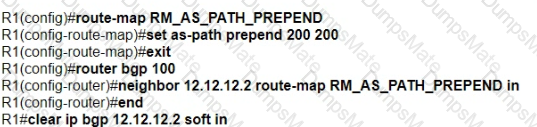
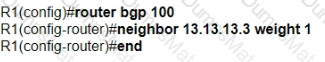
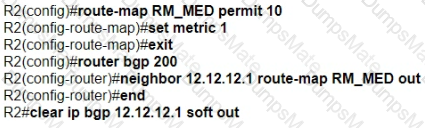
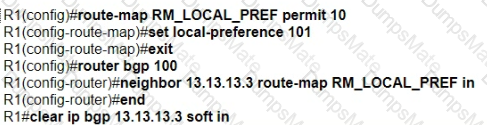

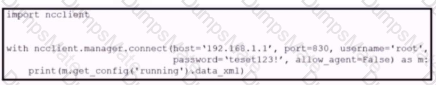






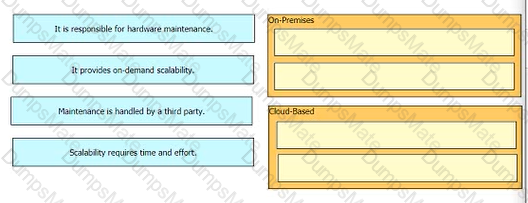
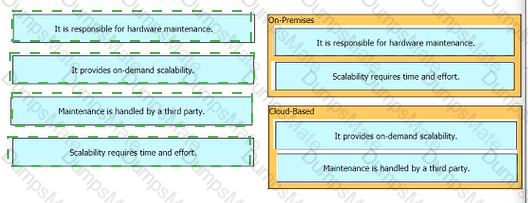

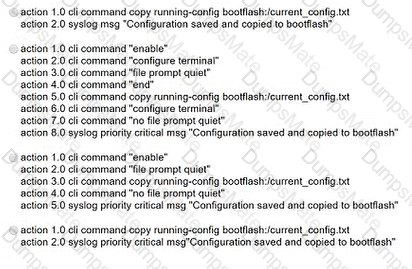
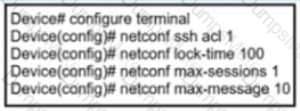

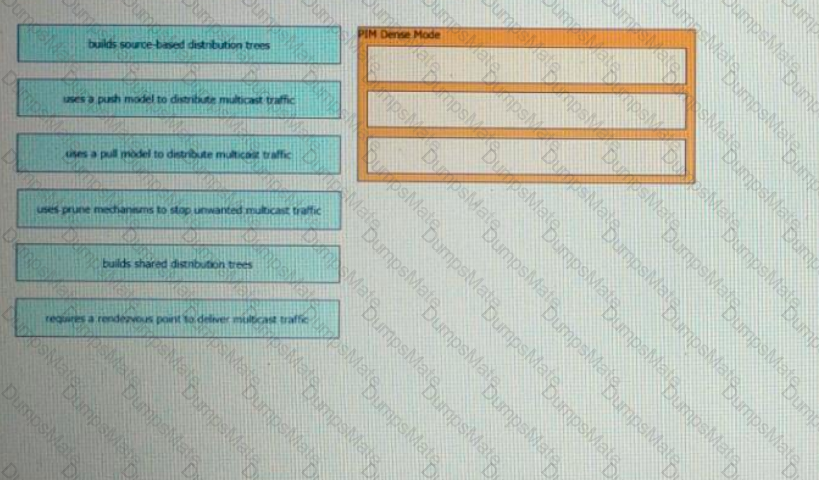
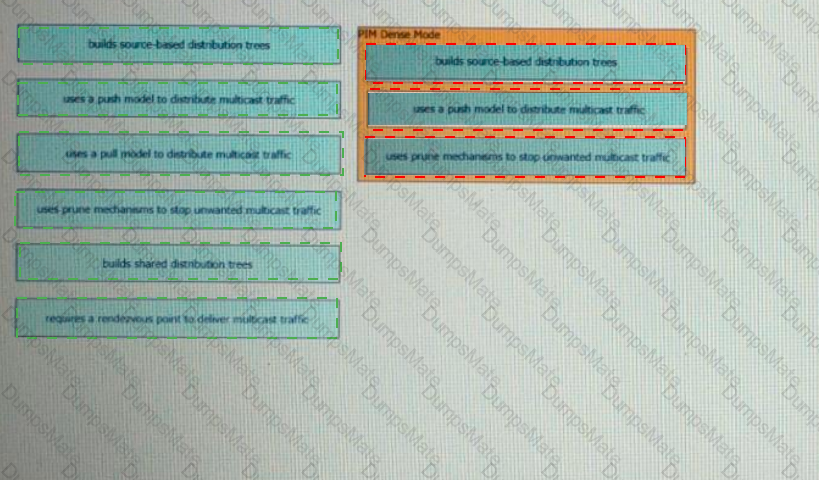
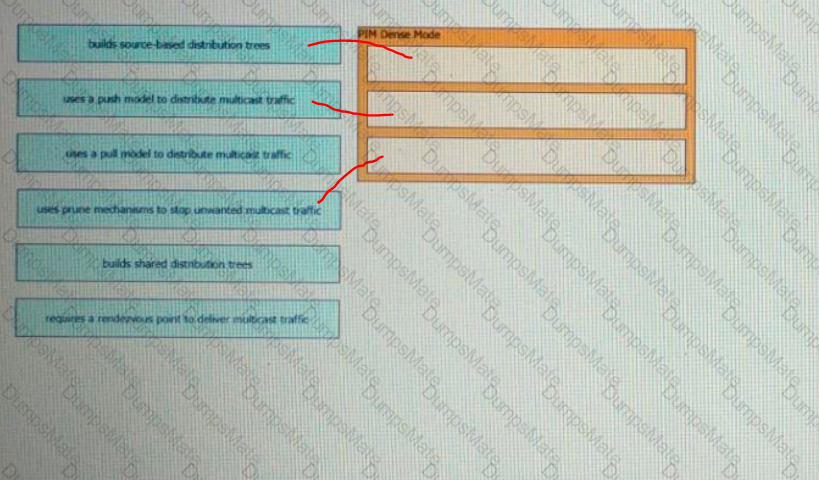 A picture containing diagram
Description automatically generated
A picture containing diagram
Description automatically generated Graphical user interface, text
Description automatically generated
Graphical user interface, text
Description automatically generated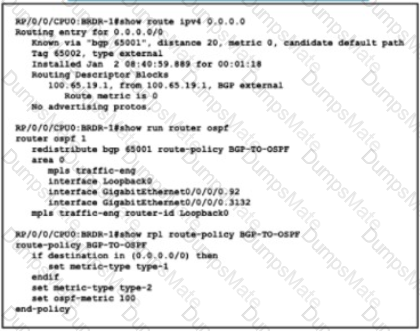
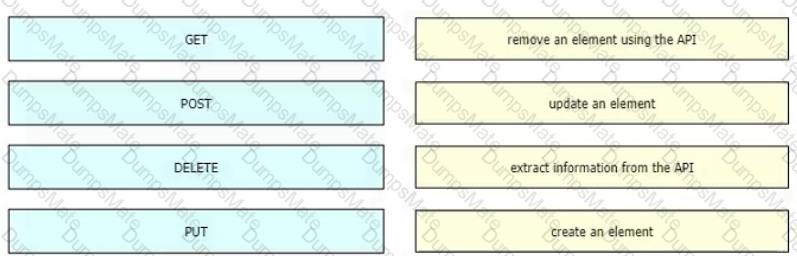
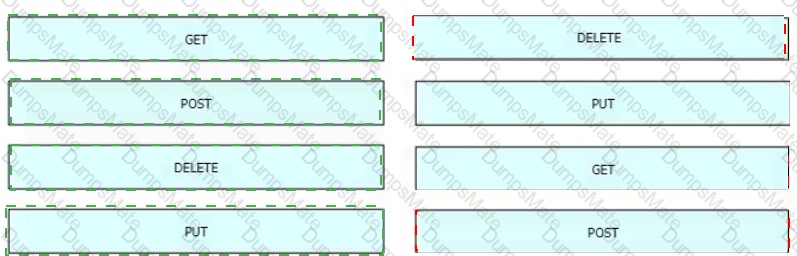
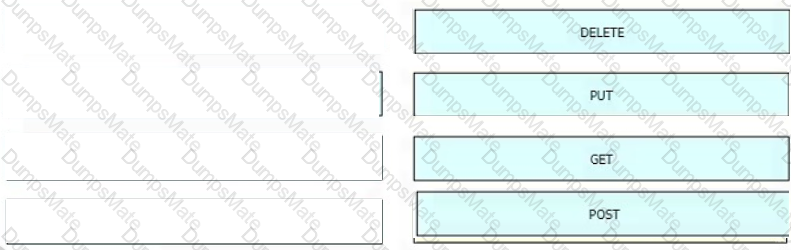 C:\Users\User\AppData\Local\Temp\SNAGHTMLb14103.PNG
C:\Users\User\AppData\Local\Temp\SNAGHTMLb14103.PNG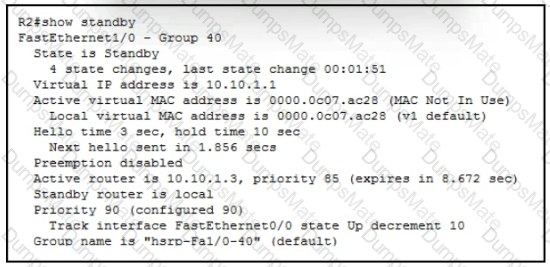
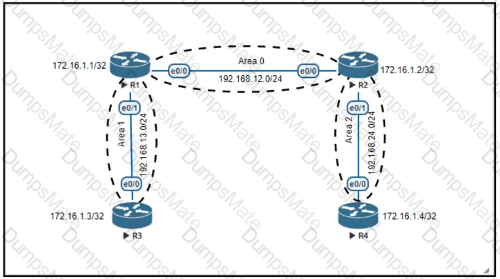

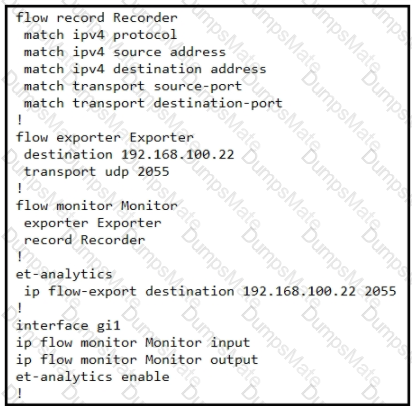

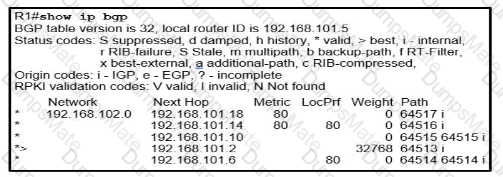
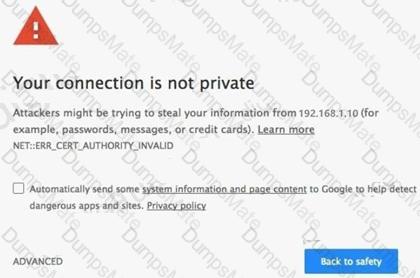
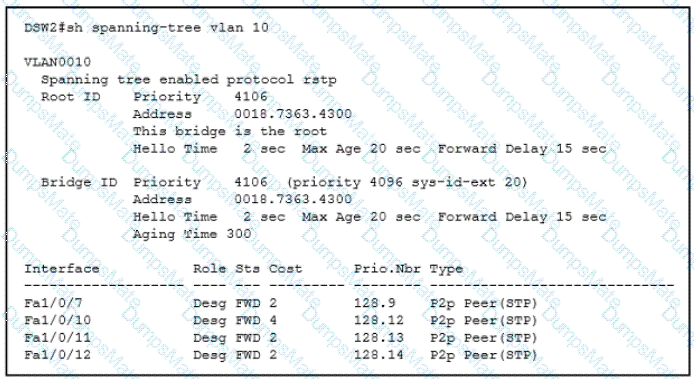
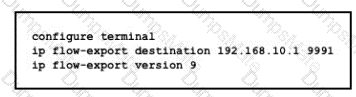


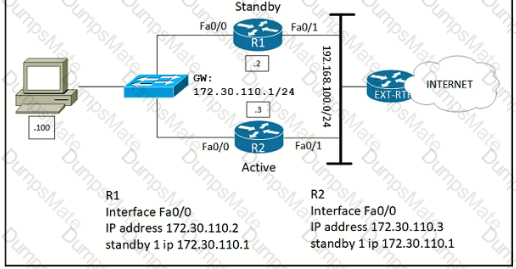
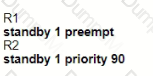
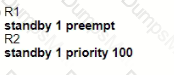

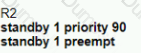


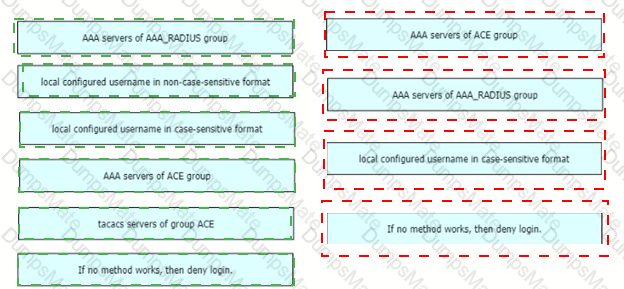

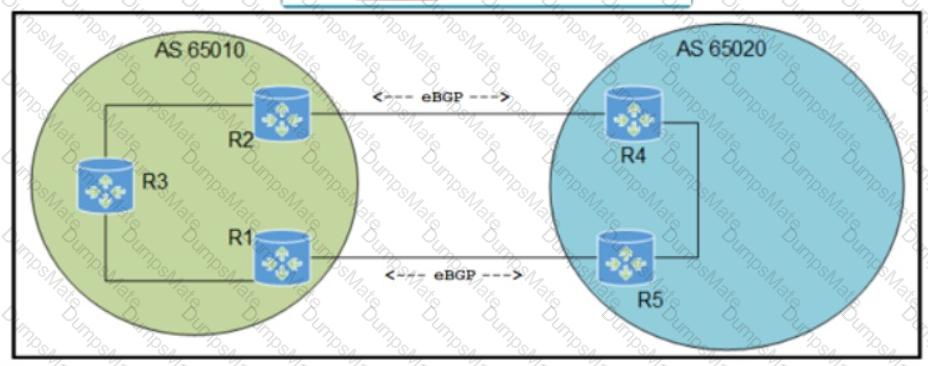
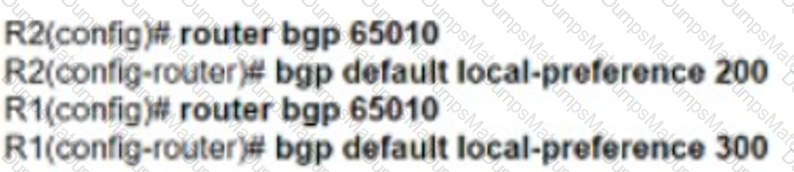
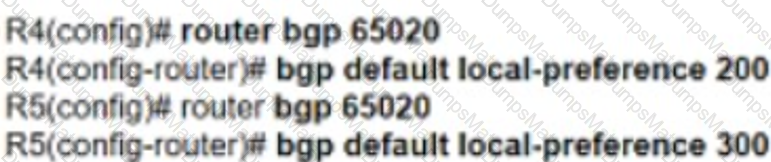
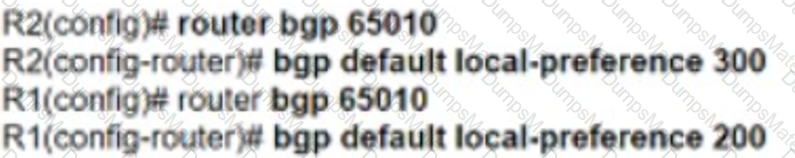
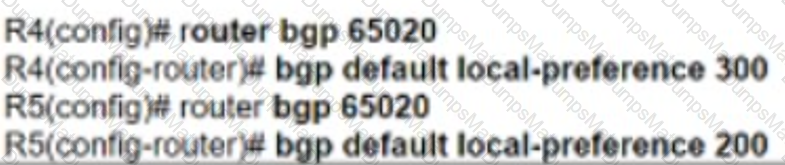
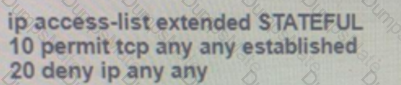
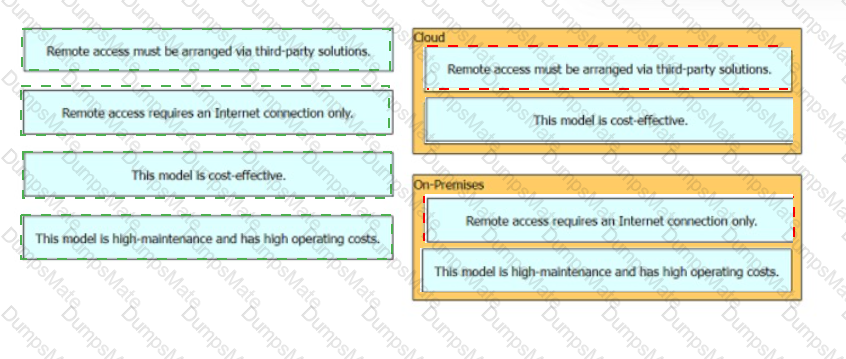
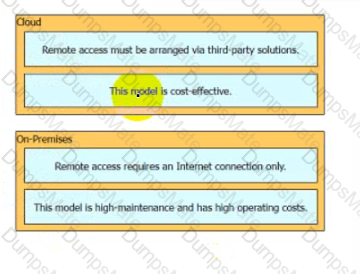 Graphical user interface
Description automatically generated with medium confidence
Graphical user interface
Description automatically generated with medium confidence
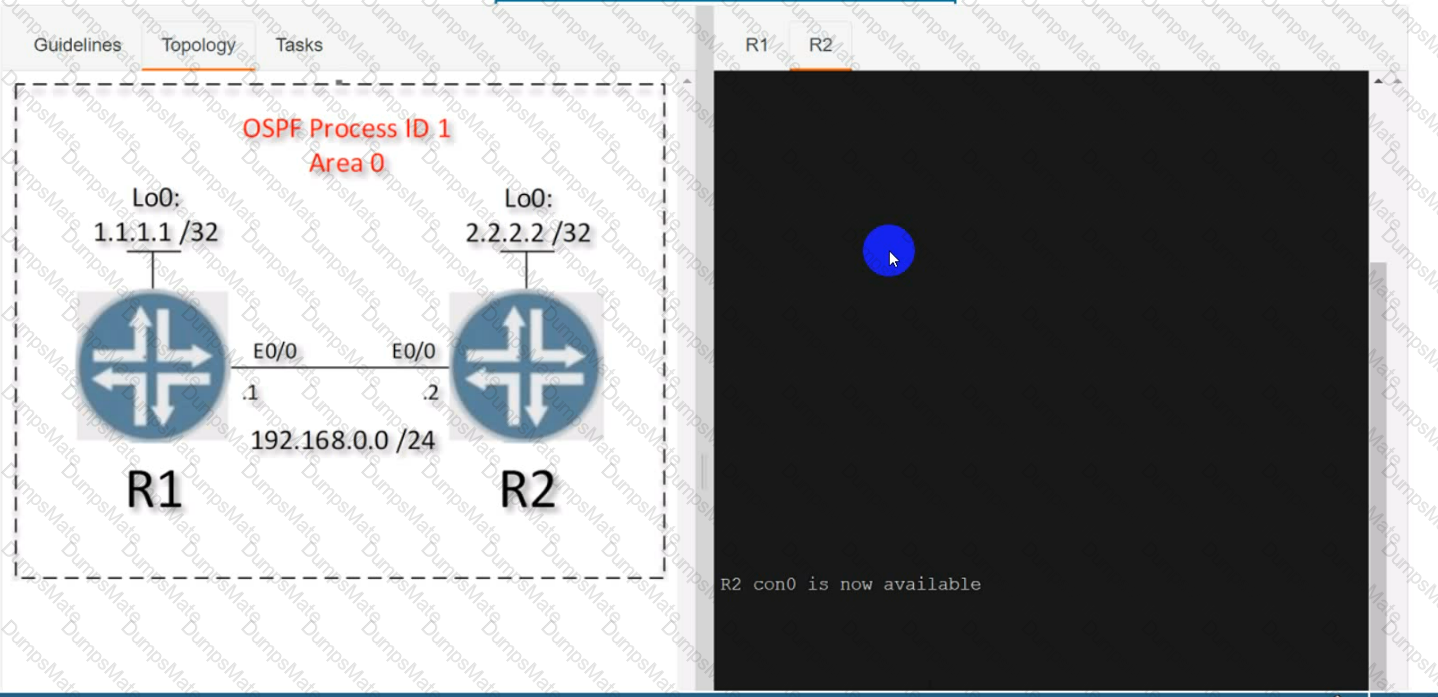
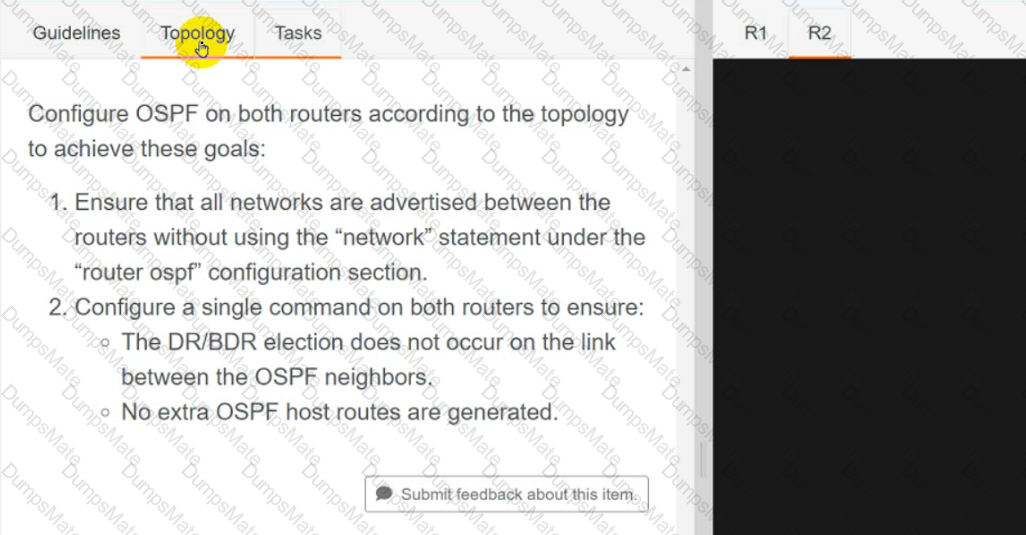
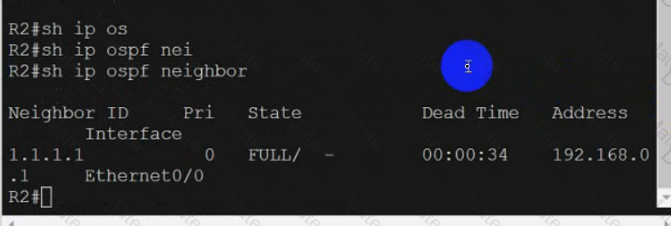
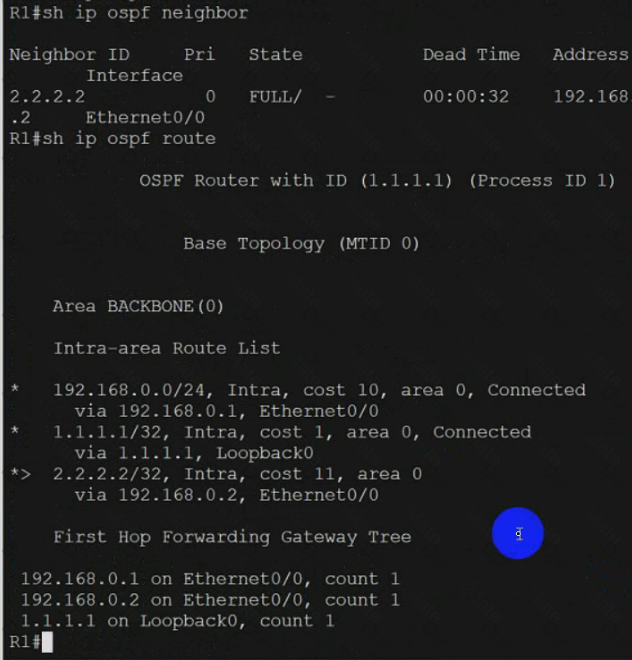
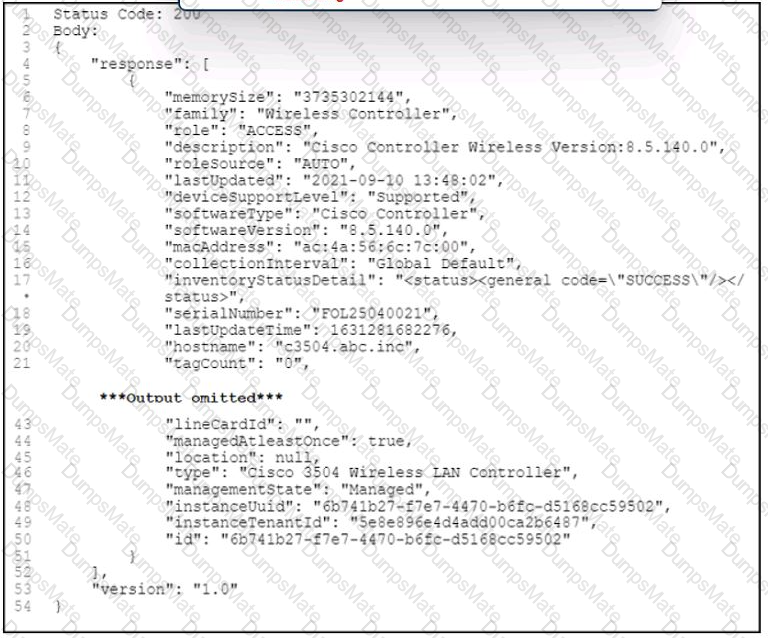
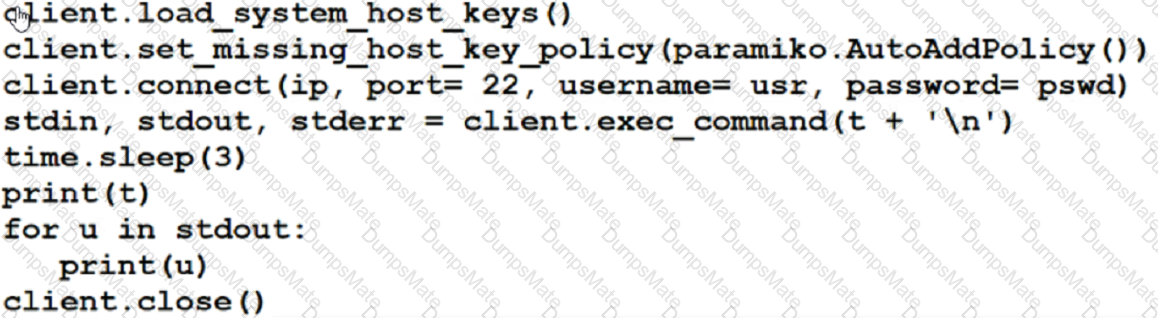
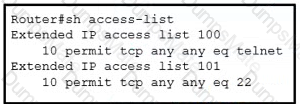


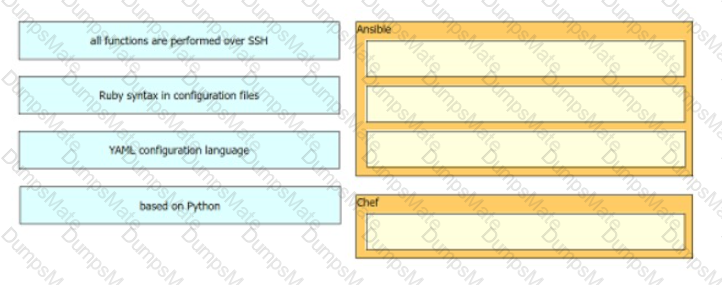
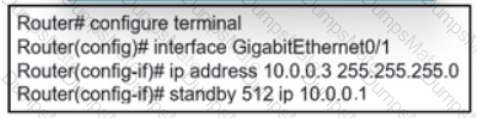
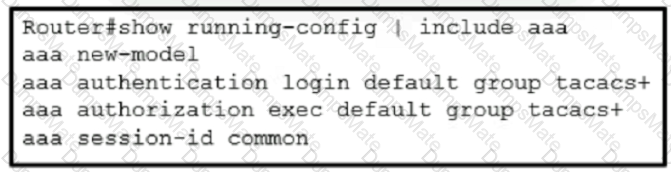
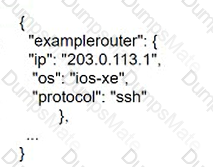
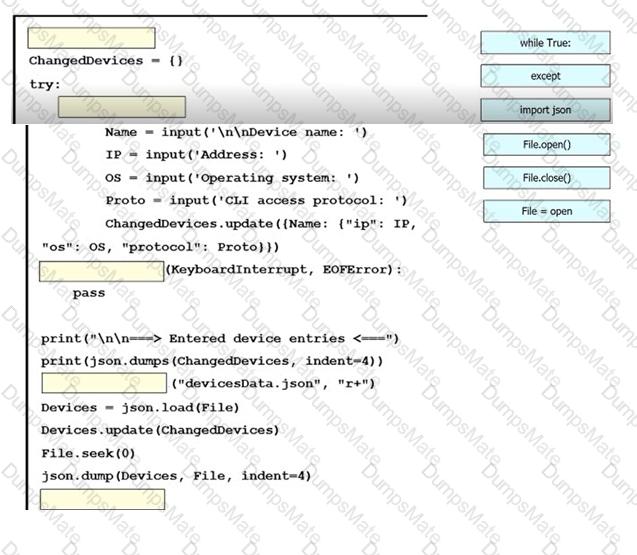
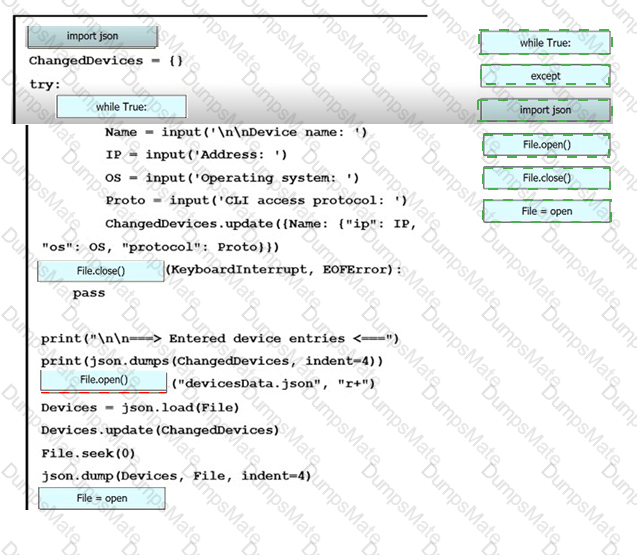
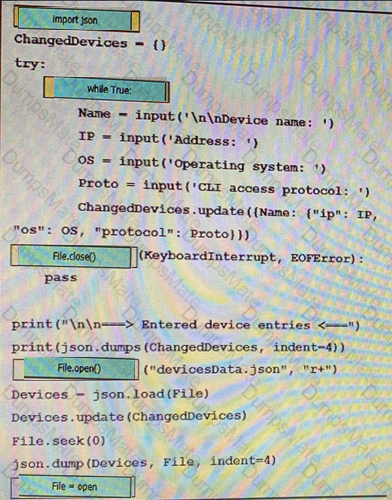 Text, letter
Description automatically generated
Text, letter
Description automatically generated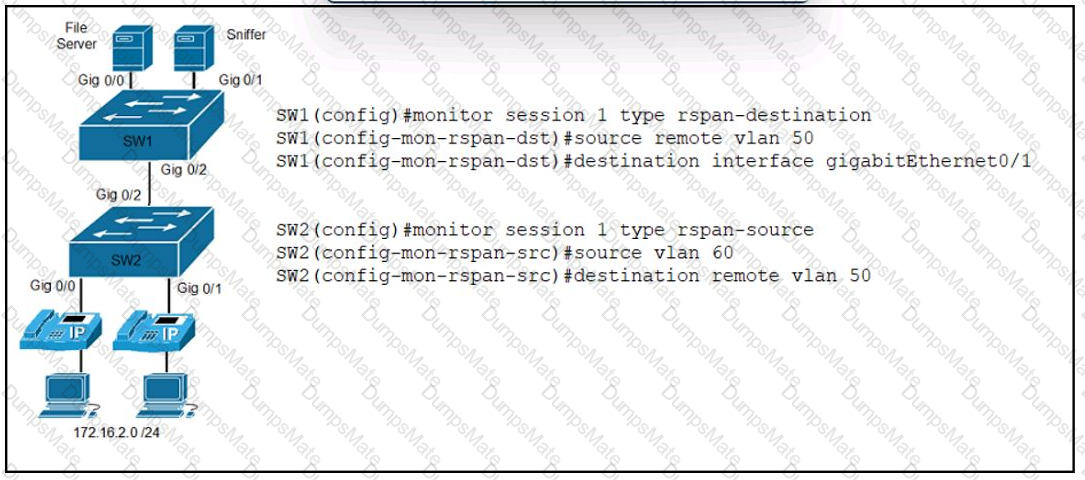
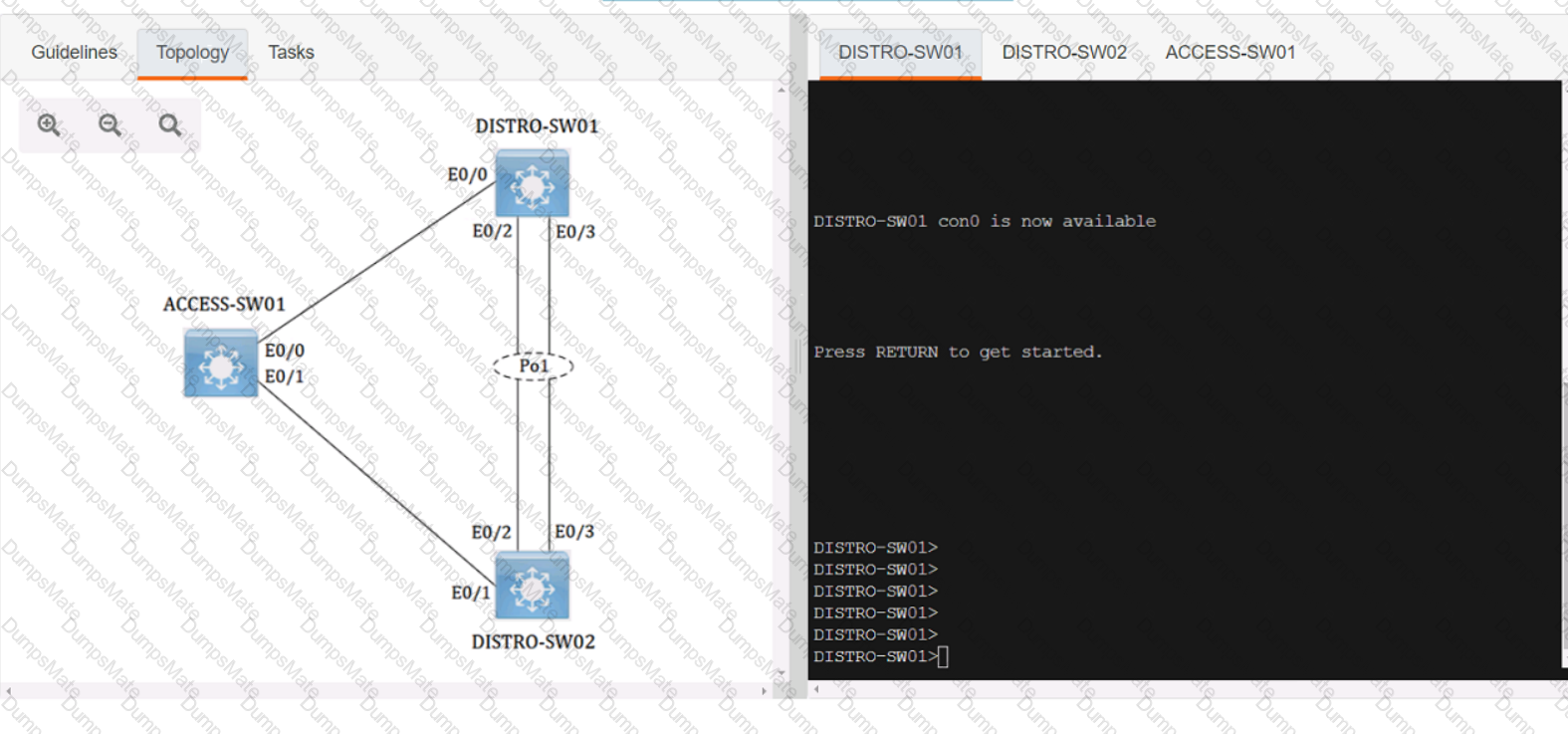
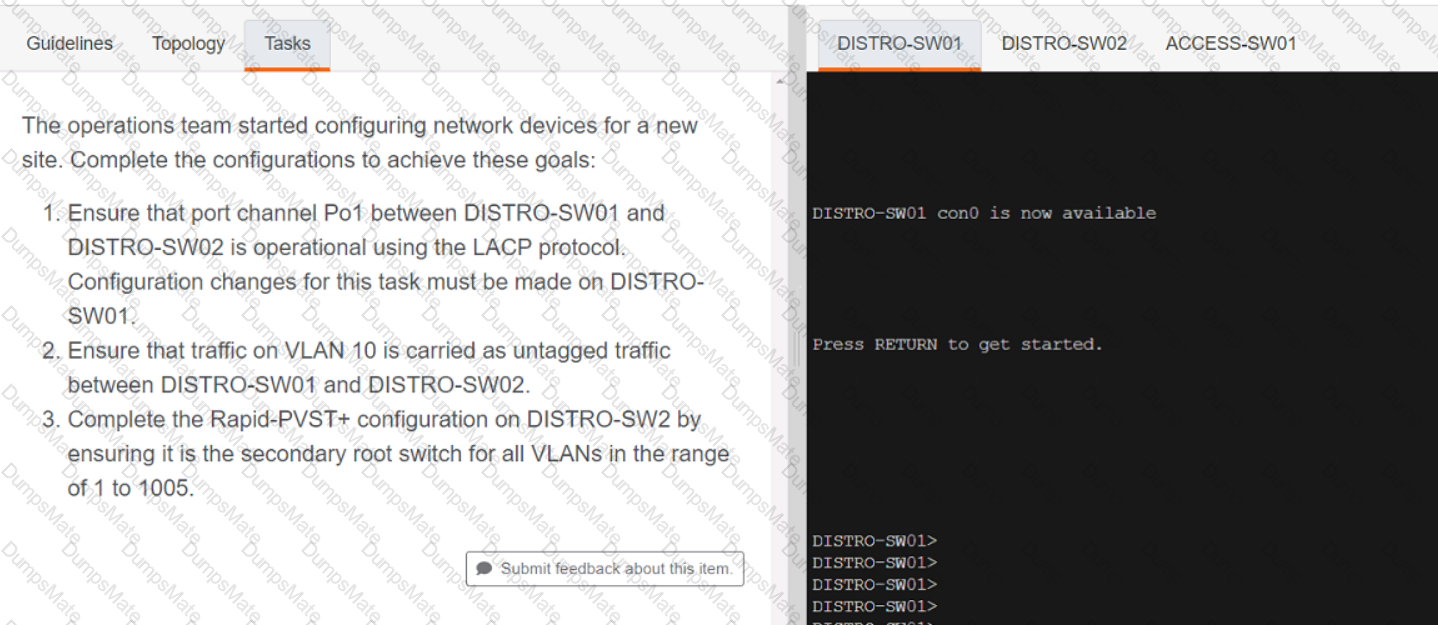
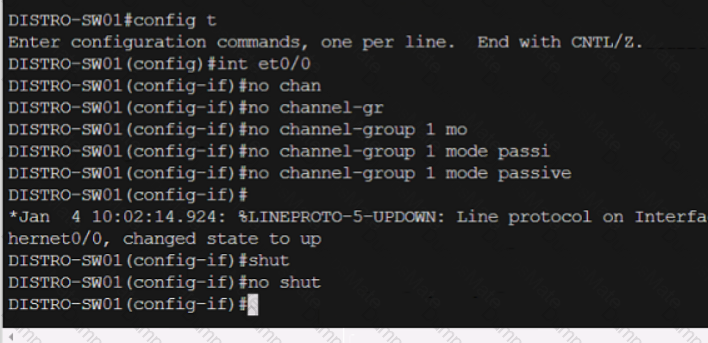
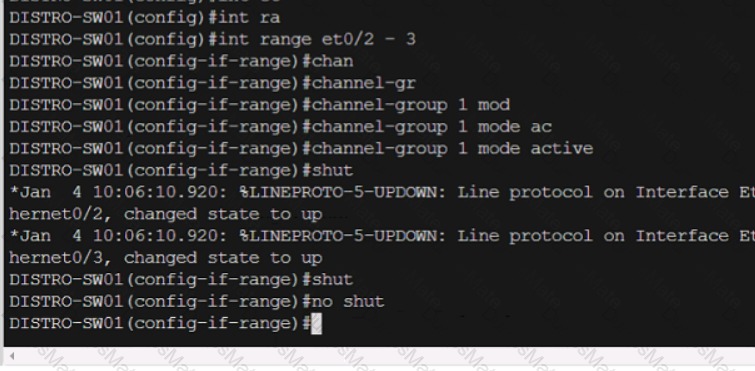





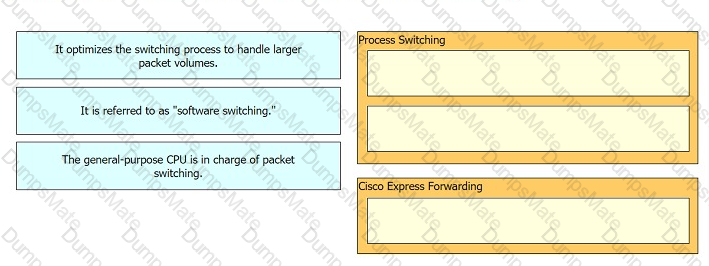
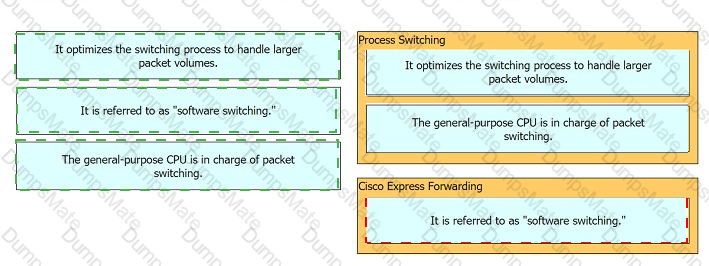
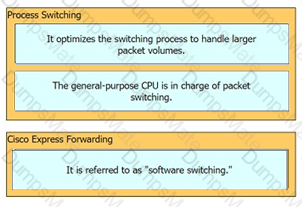 Graphical user interface, text, application
Description automatically generated
Graphical user interface, text, application
Description automatically generated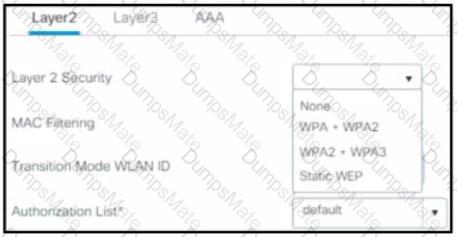
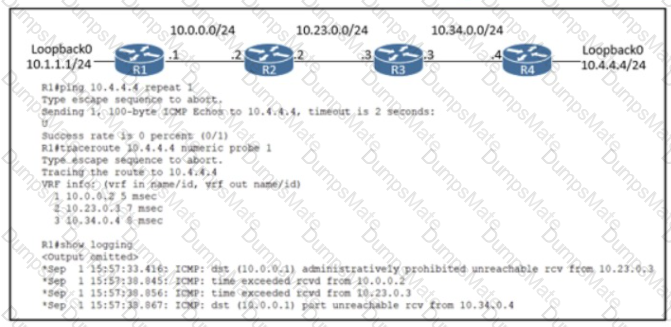
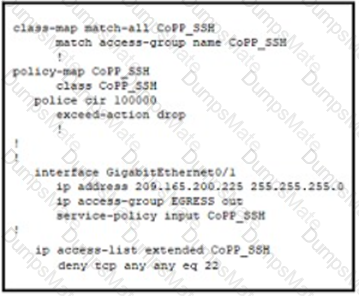
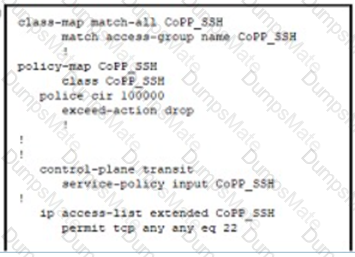
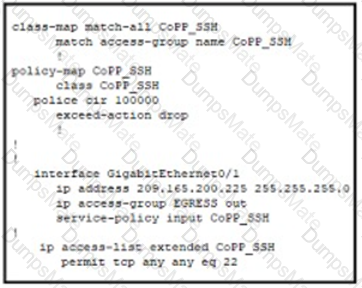










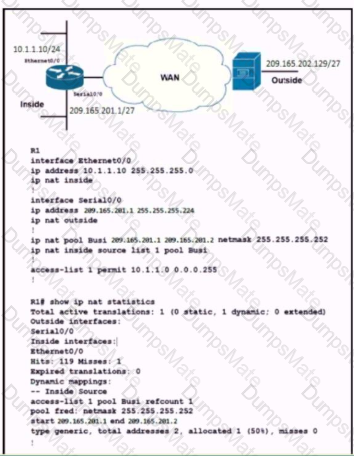
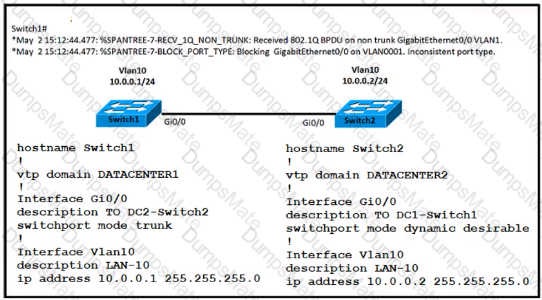
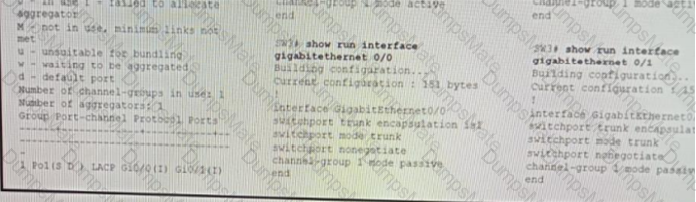

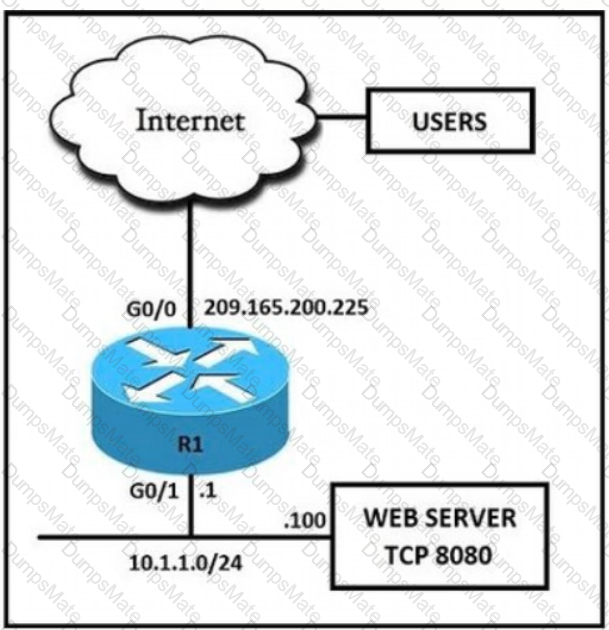





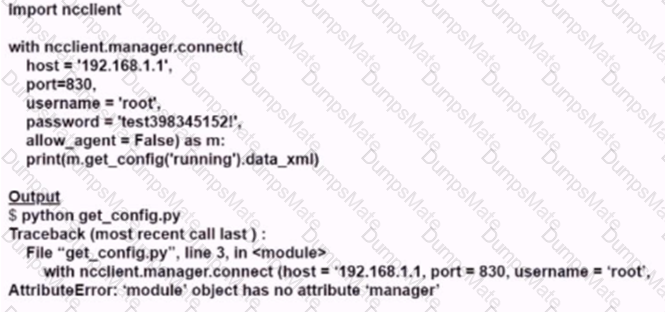
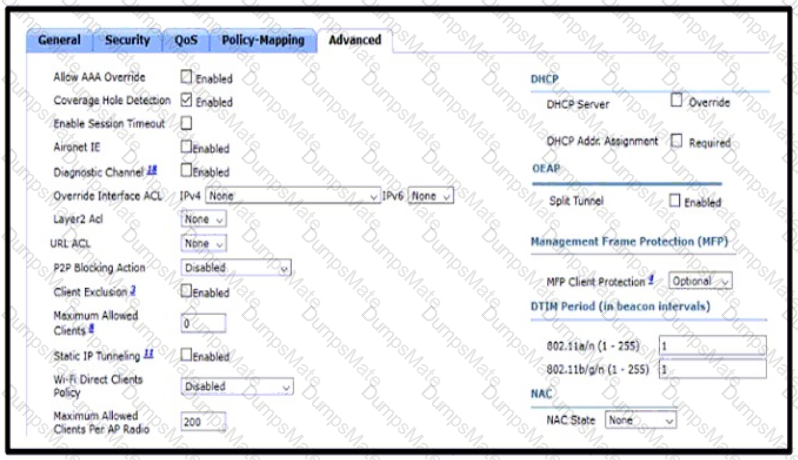
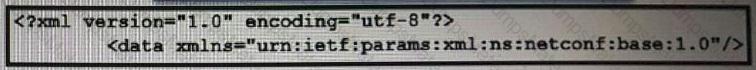
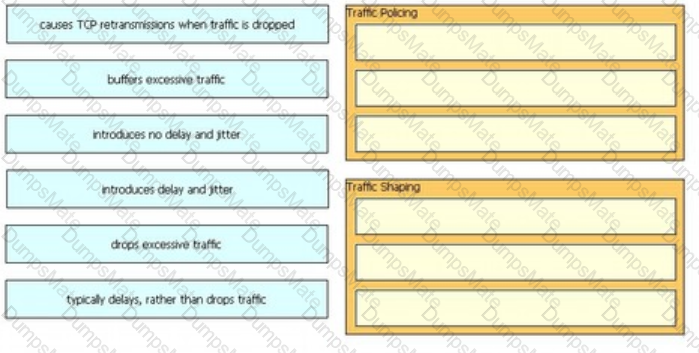
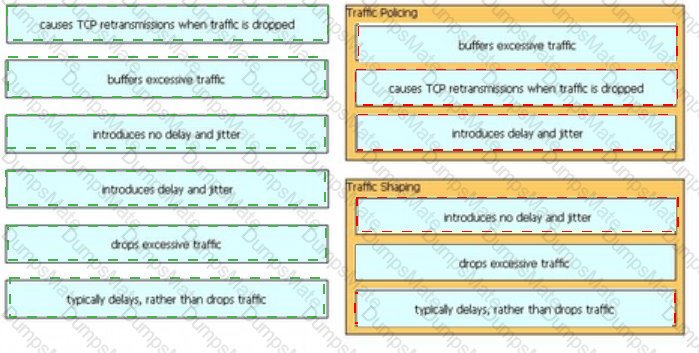
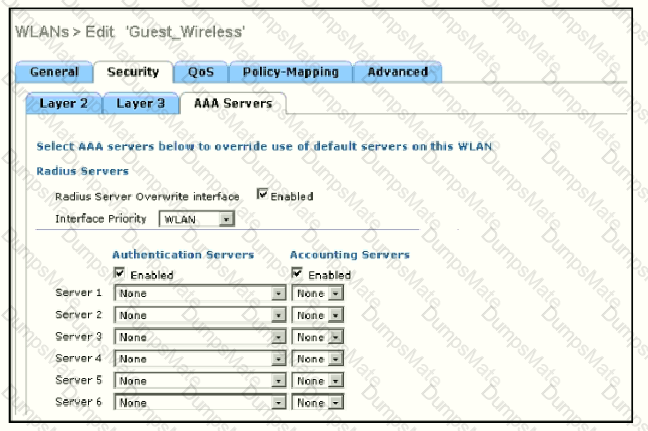
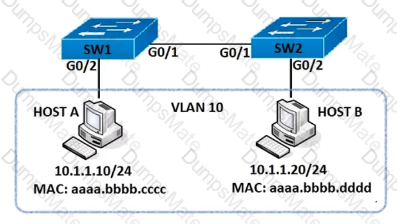
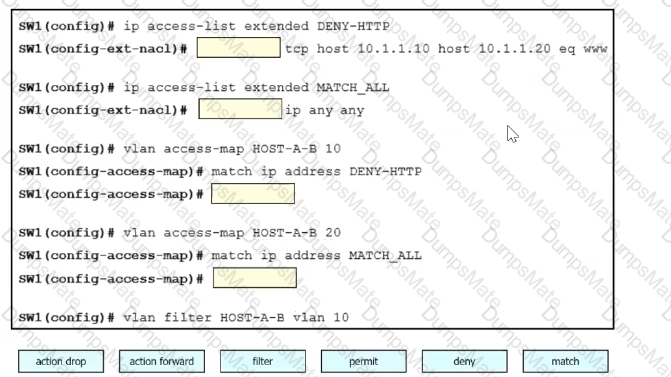
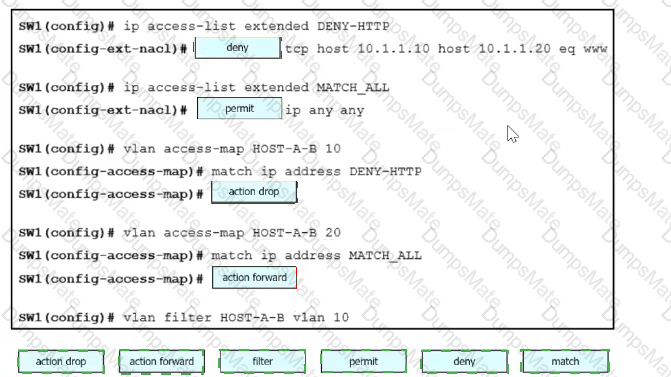
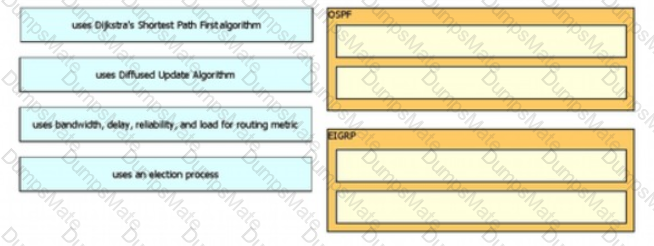
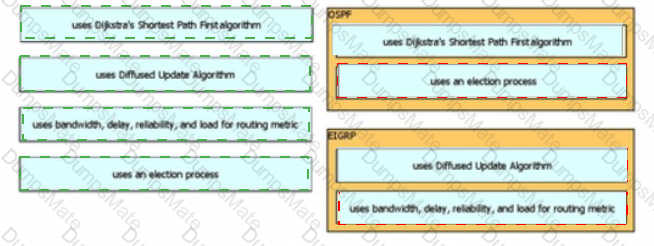
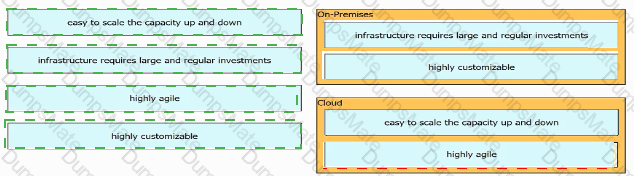
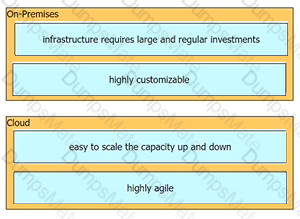
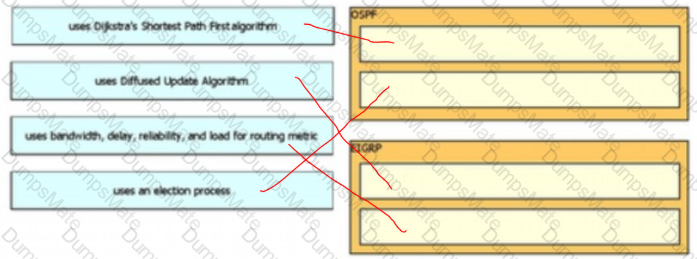 Diagram
Description automatically generated
Diagram
Description automatically generated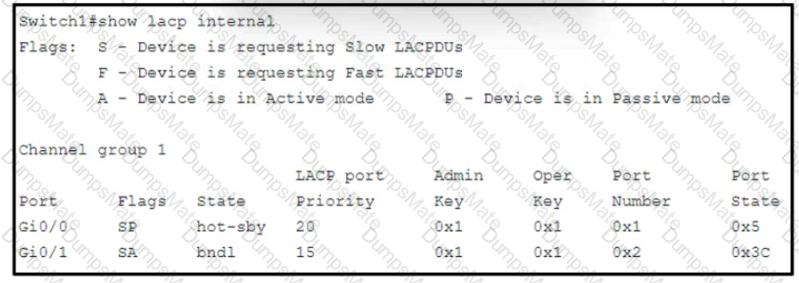




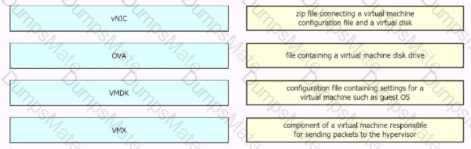
 Diagram, line chart
Description automatically generated
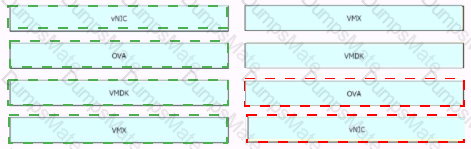
Diagram, line chart
Description automatically generated