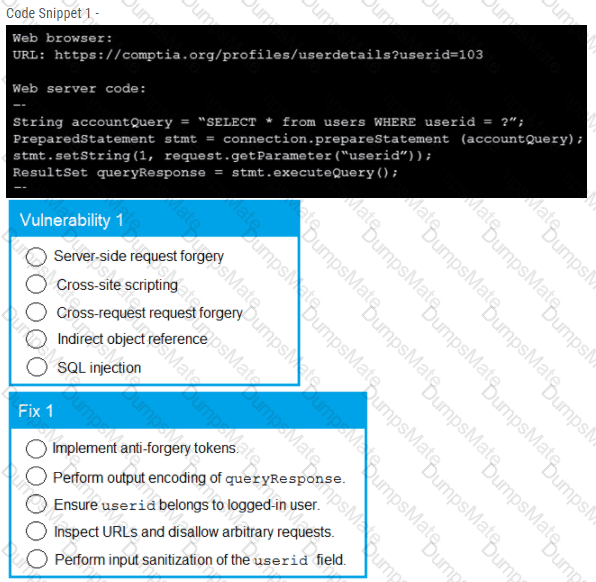
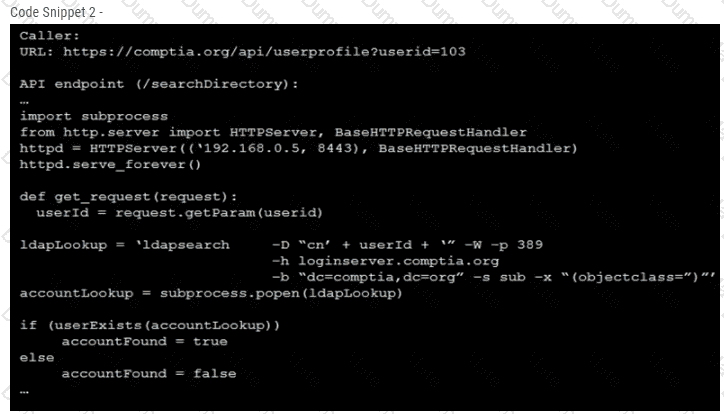
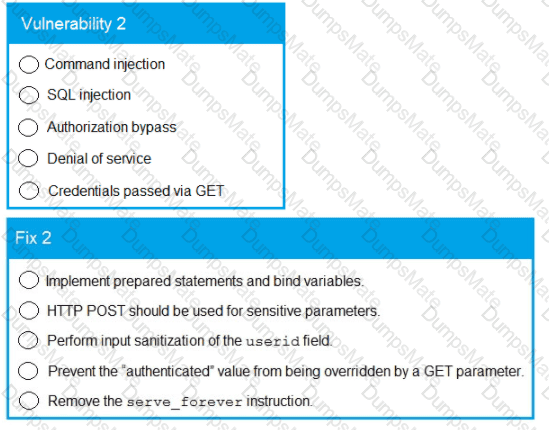
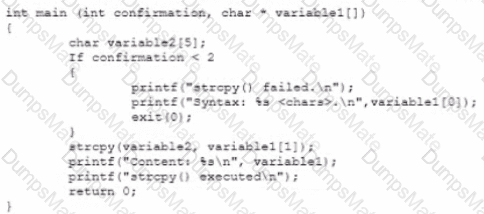
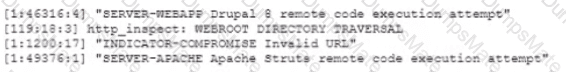
The Chief Information Officer (CIO) asks the systems administrator to improve email security at the company based on the following requirements:
1. Do not use two-factor authentication.
2. Protect the contents of a user's mailbox.
3. Be able to sign emails digitally.
4. Protect internal users from spoofing.
5. Secure communications in transit.
6. Use a hierarchically validated certifier for key exchange.
7. Do not use additional plug-in.
8. Have minimal impact to the end-user experience.
Which of the following, when used together, should the systems administrator implement to BEST meet the objectives? (Select TWO).