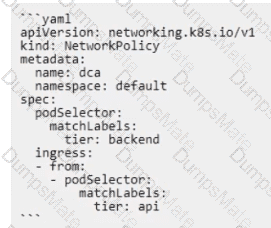
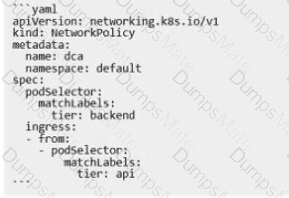
The networking drivers that allow you to enable multi-host network connectivity between containers are bridge, macvlan, ipvlan, and overlay. These drivers create networks that can span multiple Docker hosts, and therefore enable containers on different hosts to communicate with each other. The other drivers, such as host, user-defined, and none, create networks that are either isolated or limited to a single host. Here is a brief overview of each driver and how it supports multi-host networking:
•bridge: The bridge driver creates a network that connects containers on the same host using a Linux bridge. However, it can also be used to create a network that connects containers across multiple hosts using an external key-value store, such as Consul, Etcd, or ZooKeeper. This feature is deprecated and not recommended, as it requires manual configuration and has some limitations. The preferred driver for multi-host networking is overlay1.
•macvlan: The macvlan driver creates a network that assigns a MAC address to each container, making it appear as a physical device on the network. This allows the containers to communicate with other devices on the same network, regardless of the host they are running on. The macvlan driver can also use 802.1q trunking to create sub-interfaces and isolate traffic between different networks2.
•ipvlan: The ipvlan driver creates a network that assigns an IP address to each container, making it appear as a logical device on the network. This allows the containers to communicate with other devices on the same network, regardless of the host they are running on. The ipvlan driver can also use different modes, such as l2, l3, or l3s, to control the routing and isolation of traffic between different networks3.
•overlay: The overlay driver creates a network that connects multiple Docker daemons together using VXLAN tunnels. This allows the containers to communicate across different hosts, even if they are on different networks. The overlay driver also supports encryption, load balancing, and servicediscovery. The overlay driver is the default and recommended driver for multi-host networking, especially for Swarm services4.
[References:, •Use bridge networks, •Use macvlan networks, •Use ipvlan networks, •Use overlay networks, , ]



 Kubernetes
Kubernetes A blue hexagon with a white wheel
Description automatically generated
A blue hexagon with a white wheel
Description automatically generated