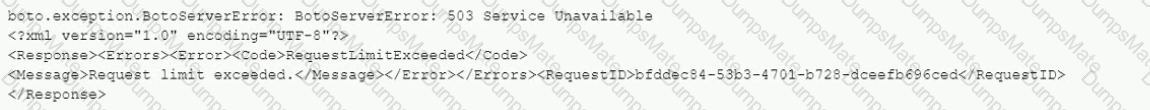
A company has an ecommerce application. To track product reviews, the company's development team uses an Amazon DynamoDB table.
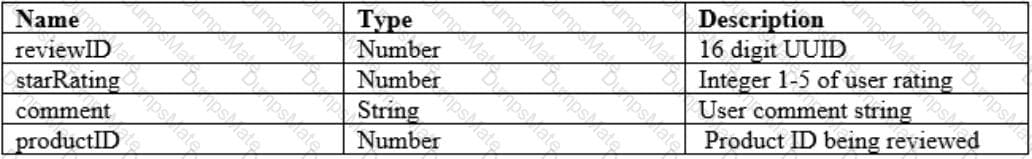
Every record includes the following:
• A Review ID, a 16-digit universally unique identifier (UUID)
• A Product ID and User ID. 16-digit UUIDs that reference other tables
• A Product Rating on a scale of 1—5 - An optional comment from the user
The table partition key is the Review ID. The most performed query against the table is to find the 10 reviews with the highest rating for a given product.
Which index will provide the FASTEST response tor this query?




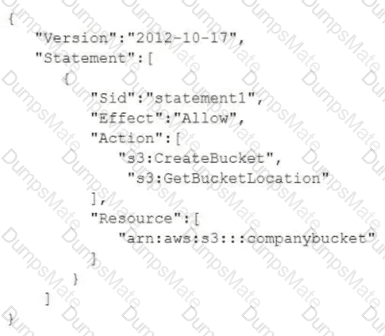 Text
Description automatically generated
Text
Description automatically generated Text, letter
Description automatically generated
Text, letter
Description automatically generated Text
Description automatically generated
Text
Description automatically generated