You have been tasked with setting up a wireless network in an office. The network will consist of 3 Access Points and a single switch. The network must meet the following parameters:
 The SSIDs need to be configured as CorpNet with a key of S3cr3t!
The SSIDs need to be configured as CorpNet with a key of S3cr3t!
 The wireless signals should not interfere with each other.
The wireless signals should not interfere with each other.
 The subnet the Access Points and switch are on should only support 30 devices maximum.
The subnet the Access Points and switch are on should only support 30 devices maximum.
 The Access Points should be configured to only support TKIP clients at a maximum speed.
The Access Points should be configured to only support TKIP clients at a maximum speed.
INSTRUCTIONS
Click on the devices to review their information and adjust the settings of the APs to meet the given requirements.
If any time you would like to bring back the initial state of the simulation, please click the Reset All button.
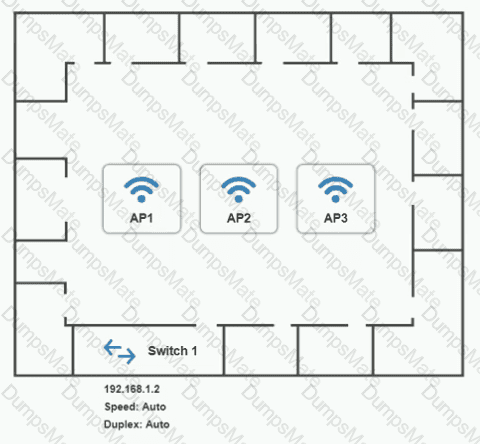
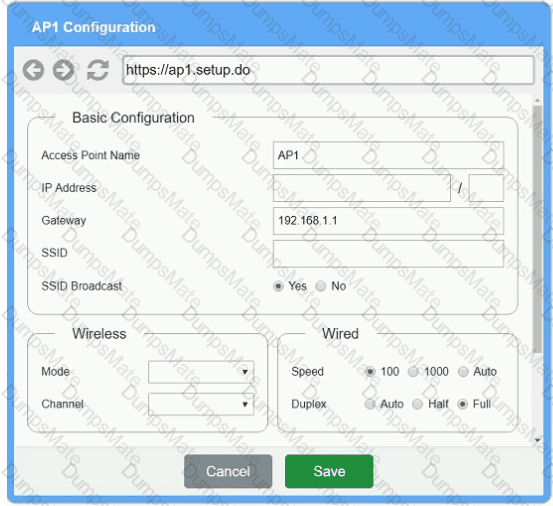
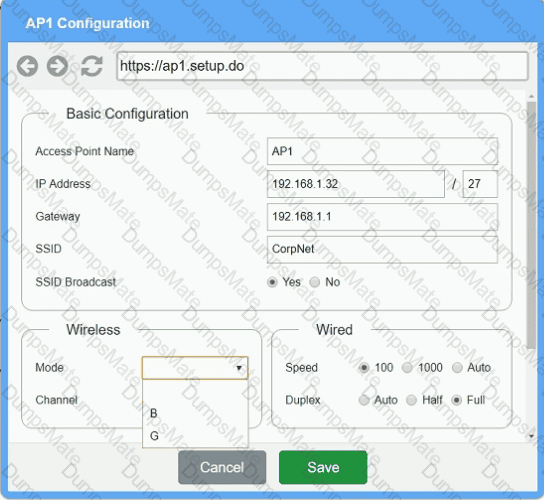
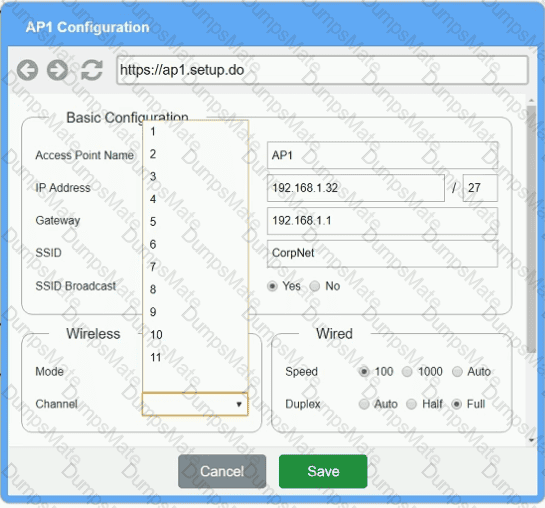
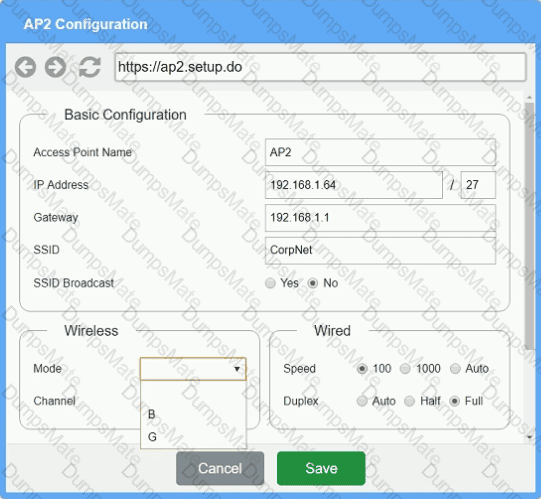
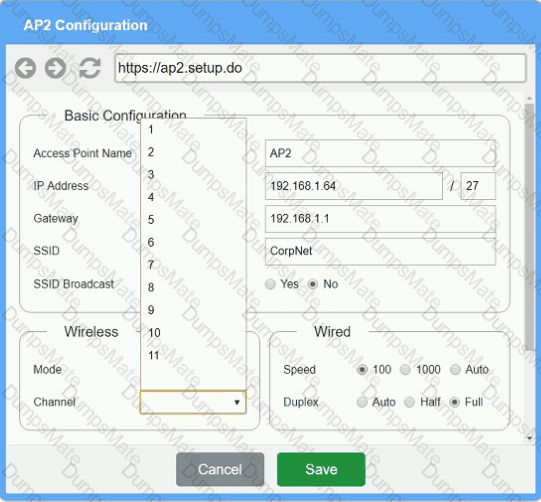
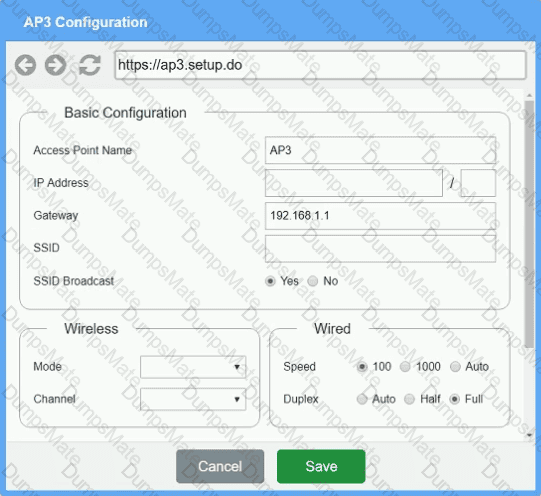
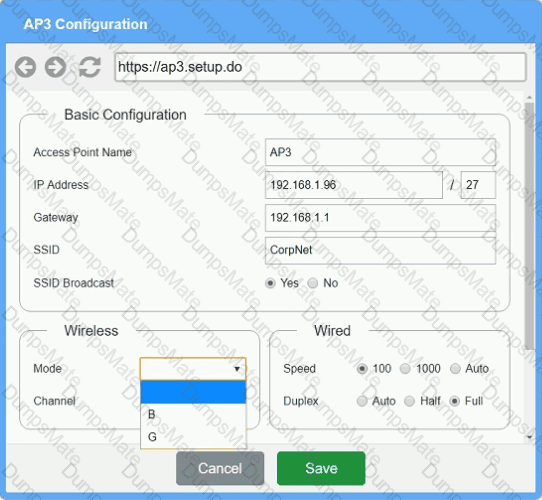
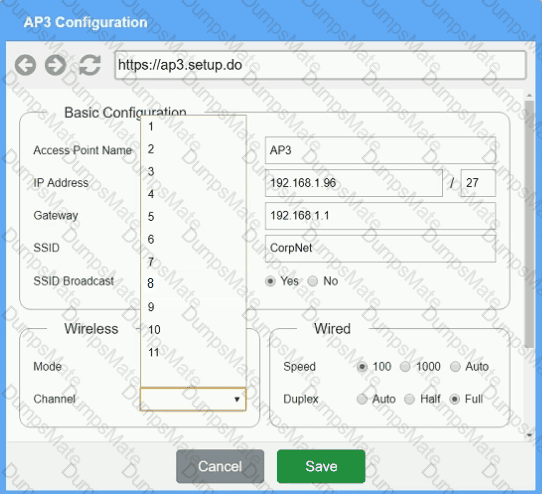



 The SSIDs need to be configured as CorpNet with a key of S3cr3t!
The SSIDs need to be configured as CorpNet with a key of S3cr3t! The wireless signals should not interfere with each other.
The wireless signals should not interfere with each other. The subnet the Access Points and switch are on should only support 30 devices maximum.
The subnet the Access Points and switch are on should only support 30 devices maximum. The Access Points should be configured to only support TKIP clients at a maximum speed.
The Access Points should be configured to only support TKIP clients at a maximum speed.