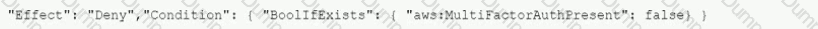Explanation: You can use IAM CloudTrail to get a history of IAM API calls and related events for your account. This history includes calls made with the IAM Management Console, IAM Command Line Interface, IAM SDKs, and other IAM services.
Options A,B and D are invalid because you need to ensure that you use the services of CloudTrail, IAM Config, IAM Credential Reports
For more information on Cloudtrail, please visit the below URL:
http://docs.IAM.amazon.com/IAMcloudtrail/latest/userguide/cloudtrail-user-guide.html
IAM Config is a service that enables you to assess, audit and evaluate the configurations of your IAM resources. Config continuously monitors and records your IAM resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations. With Config, you can review changes in configurations and relationships between IAM resources, dive into detailed resource configuration histories, and determine your overall compliance against the configurations specified in your internal guidelines. This enables you to simplify compliance auditing, security analysis, char management and operational troubleshooting.
For more information on the config service, please visit the below URL
https://IAM.amazon.com/config/
You can generate and download a credential report that lists all users in your account and the status of their various credentials, including passwords, access keys, and MFA devices. You can get a credential report from the IAM Management Console, the IAM SDKs and Command Line Tools, or the IAM API.
For more information on Credentials Report, please visit the below URL:
http://docs.IAM.amazon.com/IAM/latest/UserGuide/id credentials_getting-report.html
The correct answer is: CloudTrail, IAM Config, IAM Credential Reports Submit your Feedback/Queries to our Experts



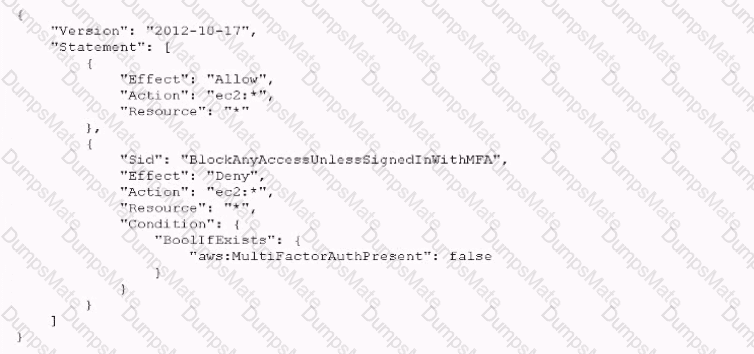

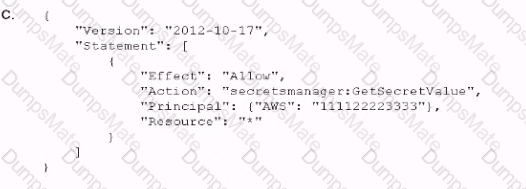
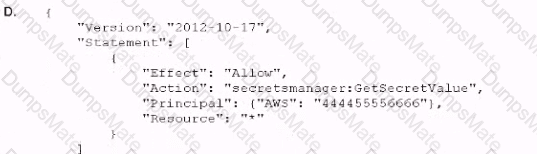
 C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg



 C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg
 C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg
 C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg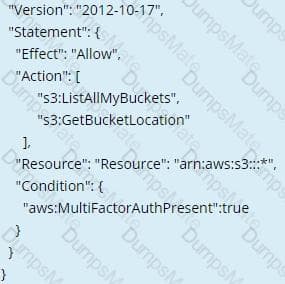 C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg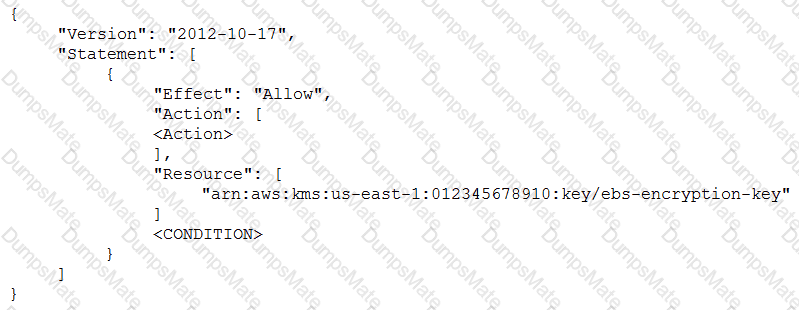
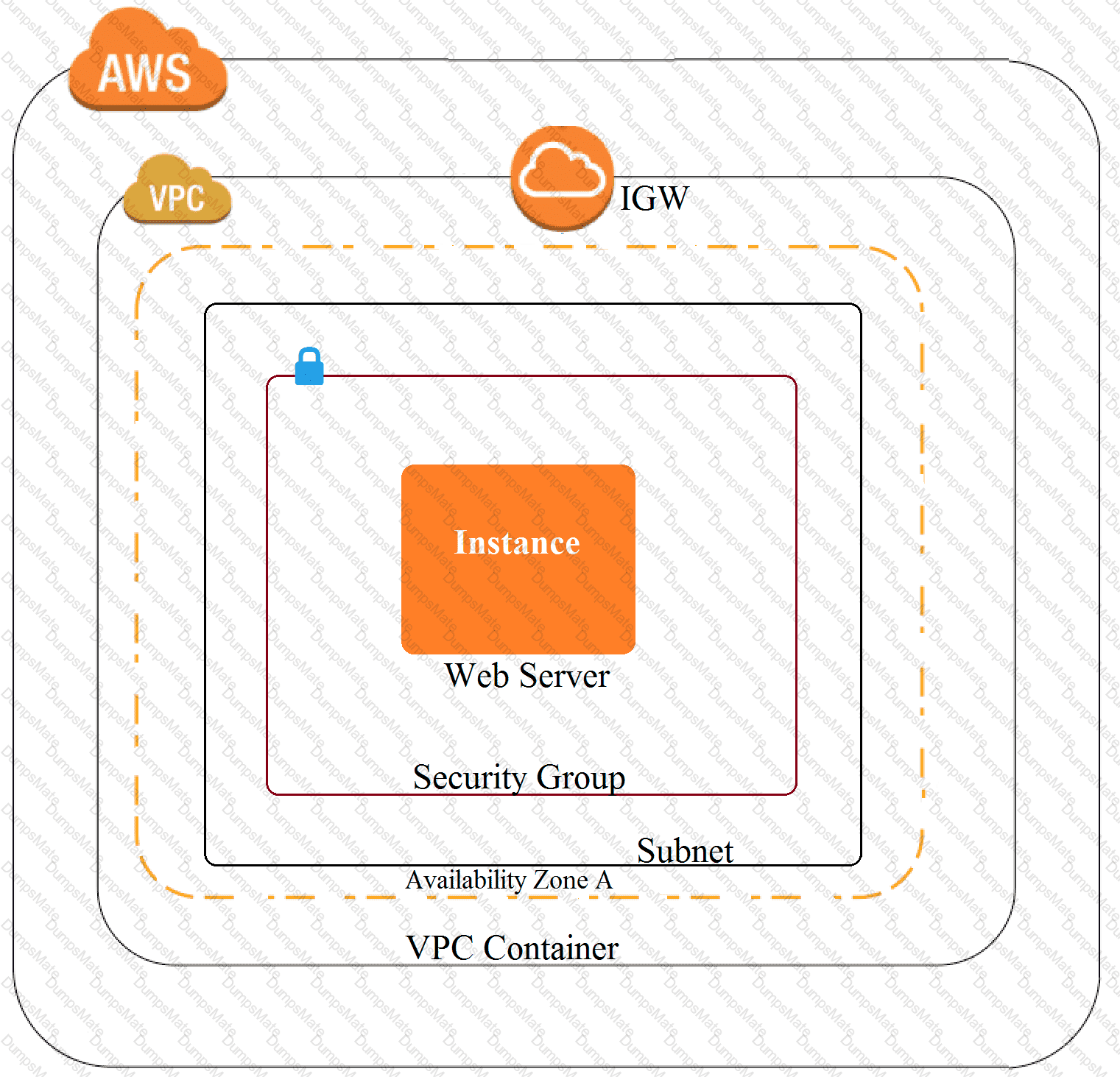


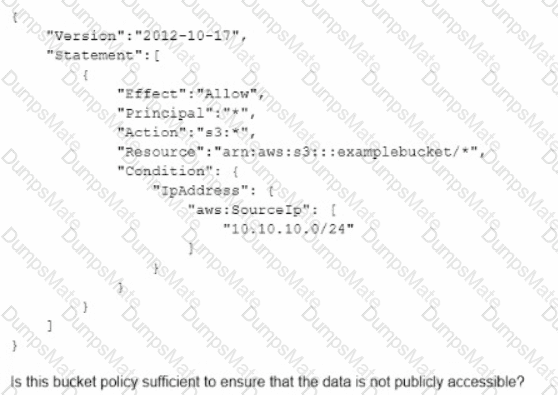
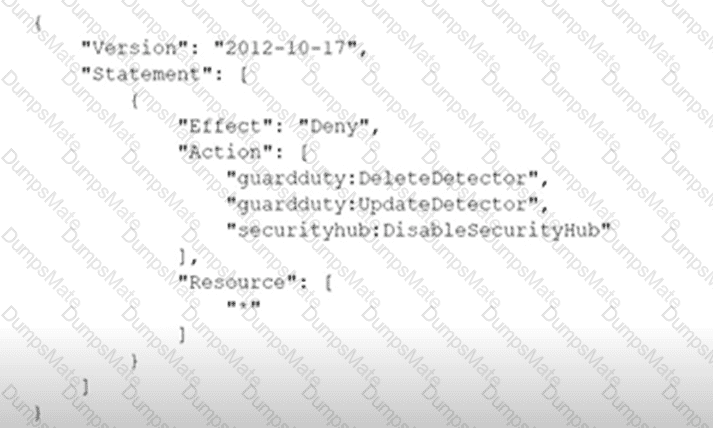

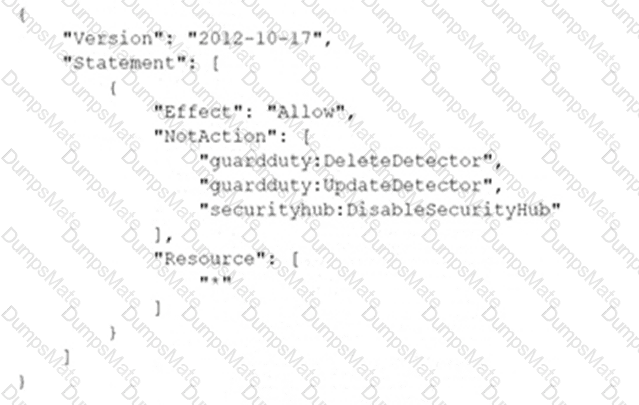
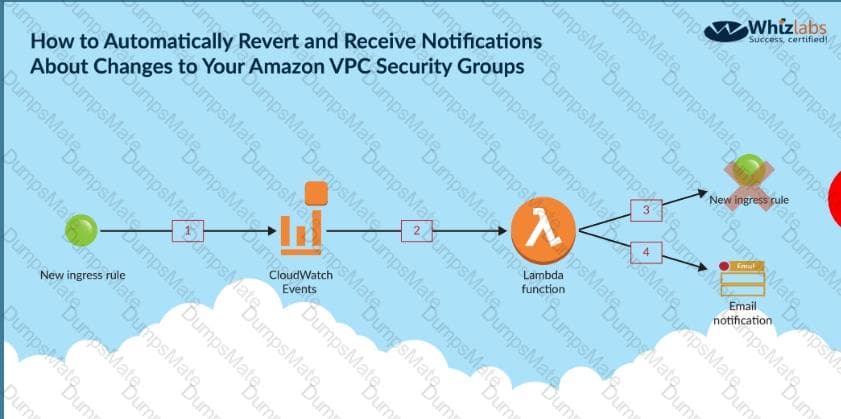 C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg