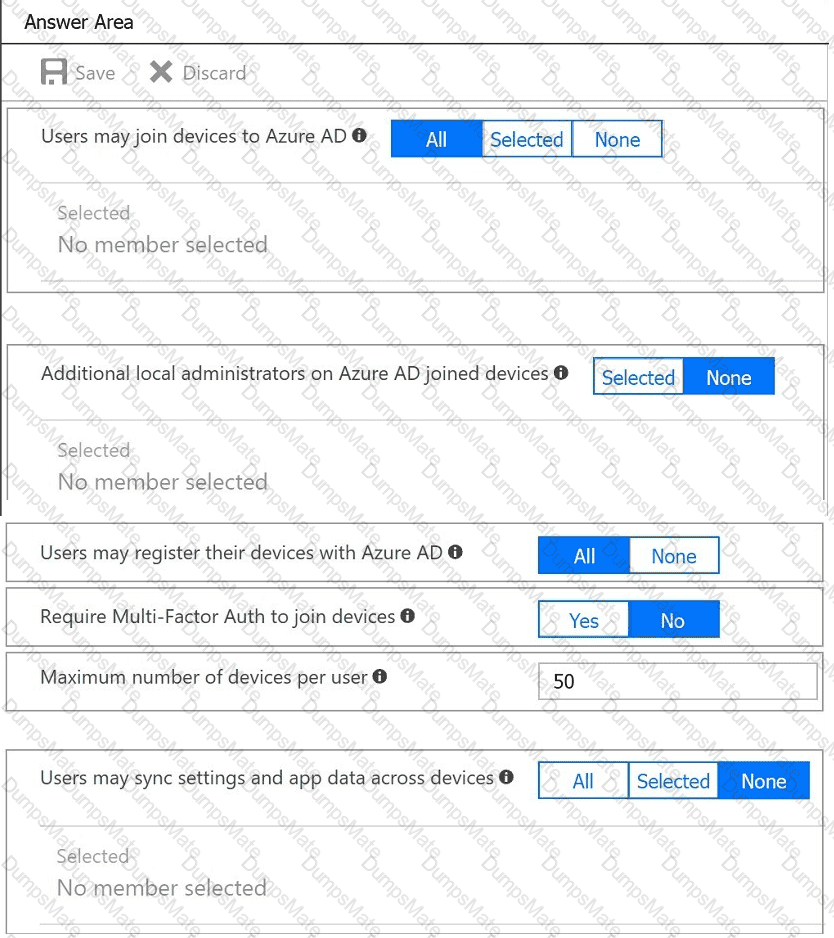
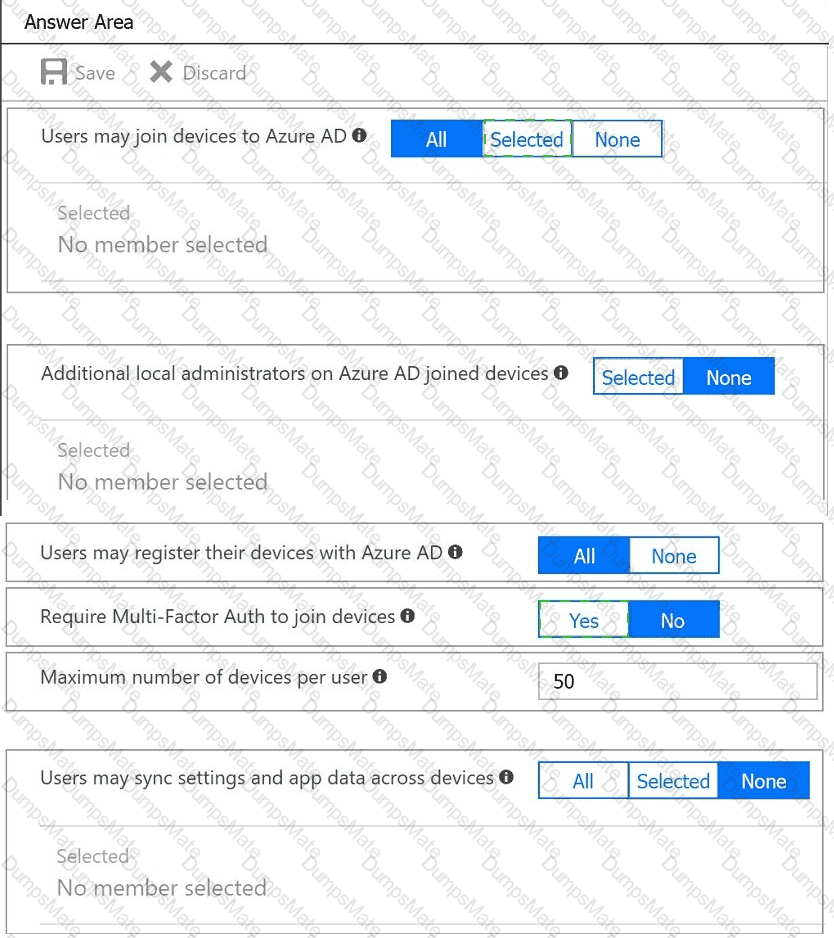
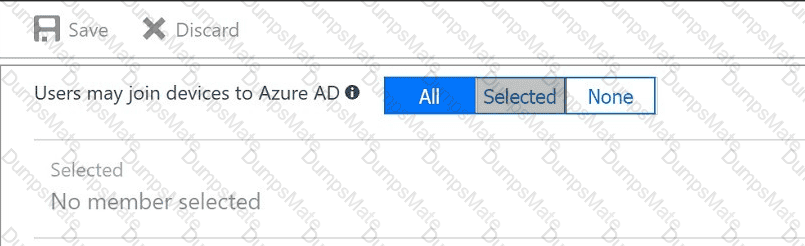
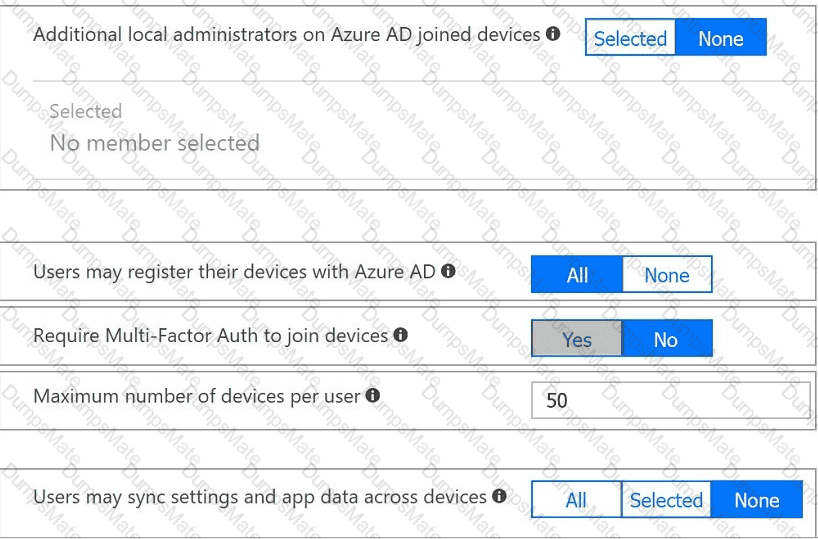
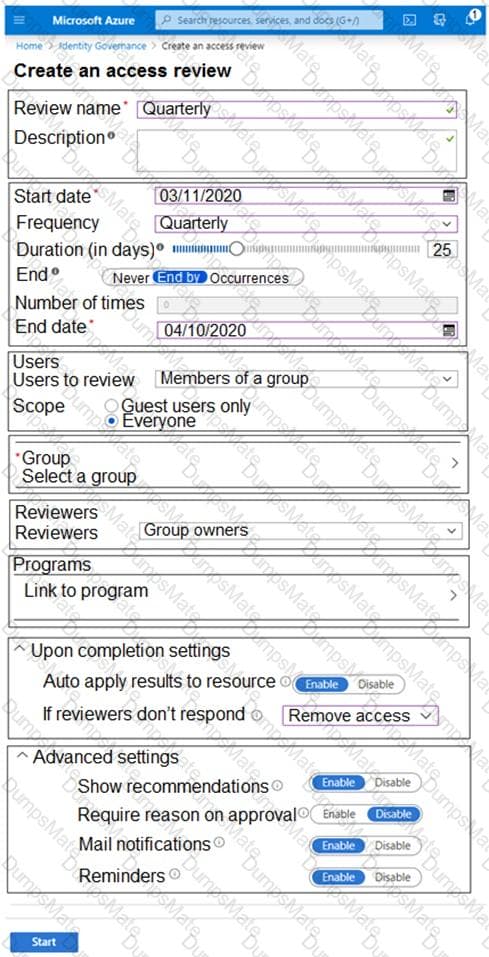
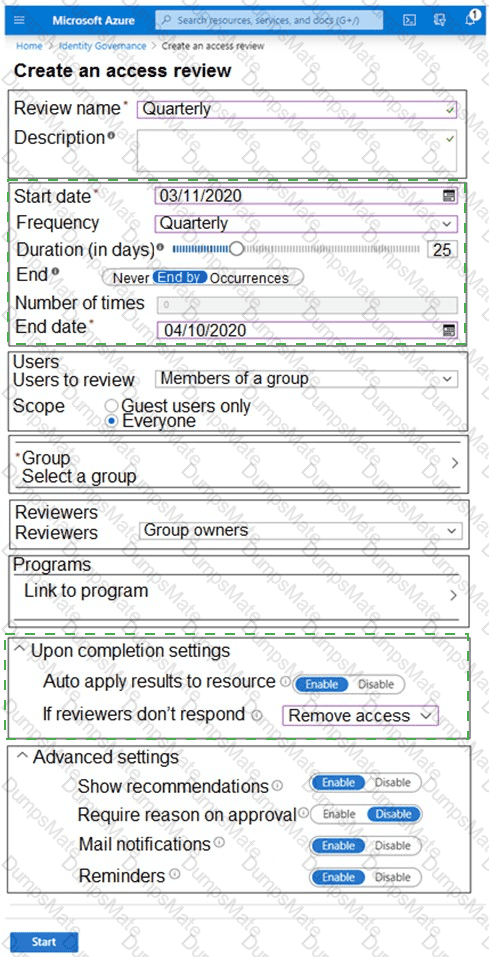
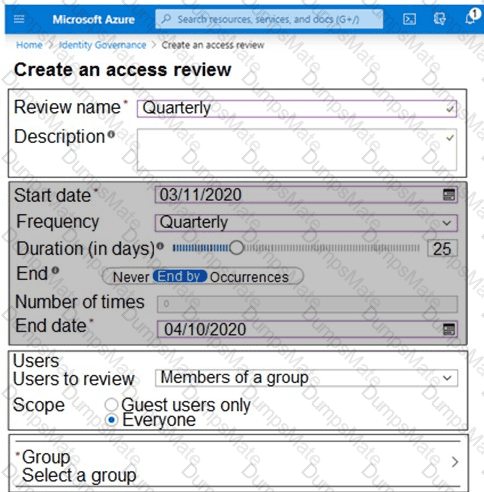
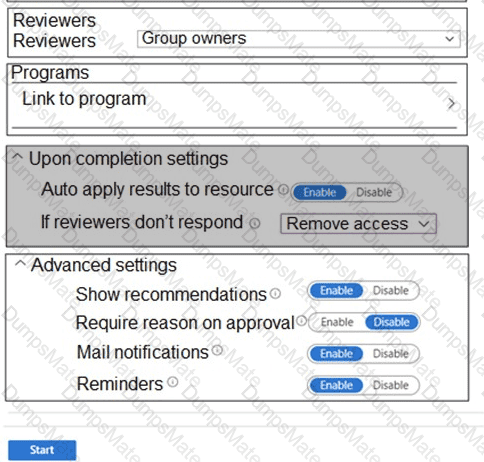
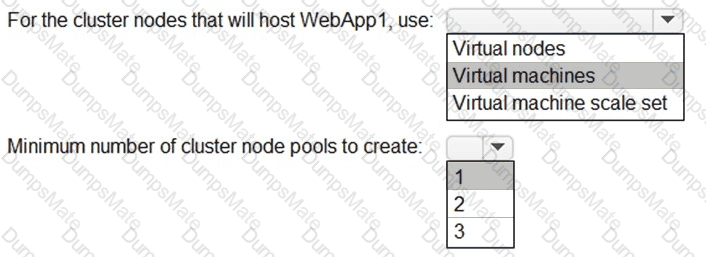
You plan to implement an access review to meet thefollowing requirements:
- The access review must be enforced until otherwise configured.
- Each user or group that has access to the Azure environment must be in the scope of the access review.
- The access review must be completed within two weeks.
- A lack of response must not cause changes in the operational environment.
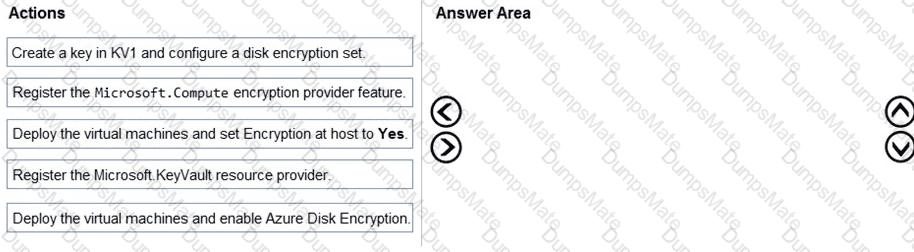
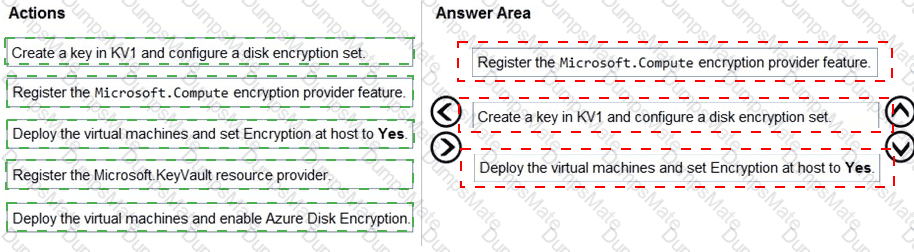
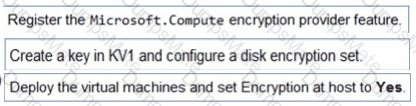
An administrator creates the access review shown in the answer area.
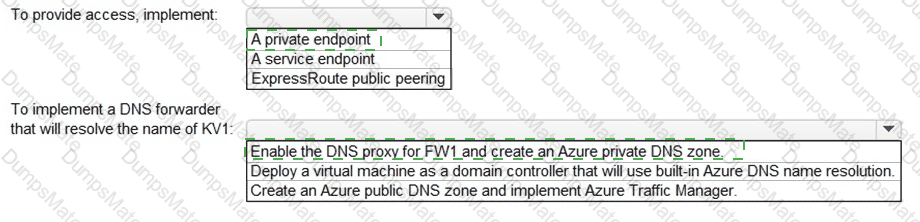
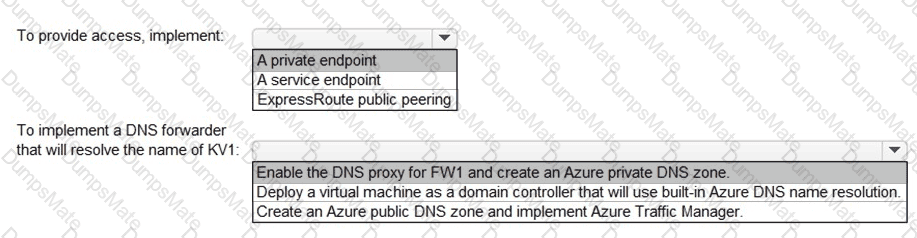
Which two sections of the access review should you modify to meet the requirements? To answer, select the appropriate sections in the answer area.
NOTE:Each correct selection is worth one point.




 Text
Description automatically generated
Text
Description automatically generated
 Table
Description automatically generated
Table
Description automatically generated
 Graphical user interface, text, application
Description automatically generated
Graphical user interface, text, application
Description automatically generated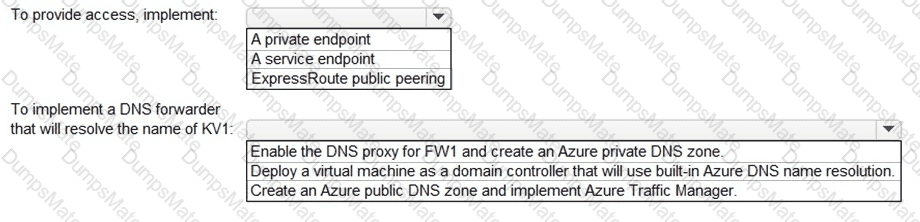
 Graphical user interface, text, application
Description automatically generated
Graphical user interface, text, application
Description automatically generated