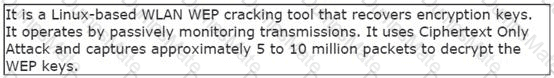
Rick works as the Network Administrator of a Windows 2000 network. The network consists of 30 domain controllers, 65 member servers, and 5000 workstations. All the computers on the network use Windows 2000 Advanced Server, Windows 2000 Server, and Windows 2000 Professional operating systems. The Windows 2000 Advanced Server computers are running the Cluster Service. The network uses TCP/IP as its only protocol. Once a week Rick works from home. But rest of the weekdays, he has to travel. Rick wants to be able to remotely administer each Windows 2000 server on his network with the following considerations:
• He must be able to establish a VPN connection to the Windows 2000 Server computers on the network from his home, so that the data remain encrypted and encapsulated during data transfer.
• While traveling , he must be able to connect to the network from a laptop computer via remote access connection, so that he can perform any task on the main Windows 2000 domain controller.
• While traveling, he must be able to edit the registry of the Windows 2000 Server computer.
• During the migration process to Windows 2000, he depleted all the financial resources for licensing. Therefore, he must not be required to add additional licenses to the network.
Rick takes the following actions:
• He implements the VPN connection on the proper server, the laptop computer, and the home computer.
• He configures the VPN connection to use the IPSec protocol in Encapsulating Security Payload (ESP) Tunnel Mode.
• He implements Windows 2000 Terminal Services using the Remote Administration mode on the Windows 2000 servers.
• He installs and configures Routing and Remote Access properly.
Which of the following goals will be accomplished by these actions?
Each correct answer represents a complete solution. Choose all that apply.