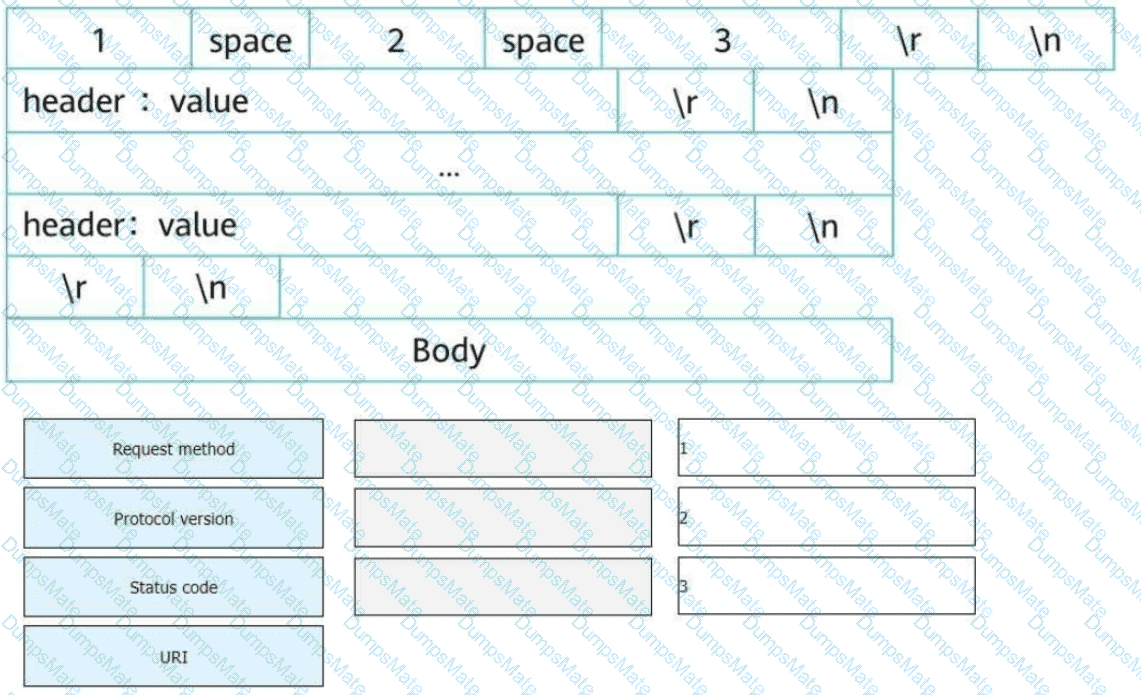
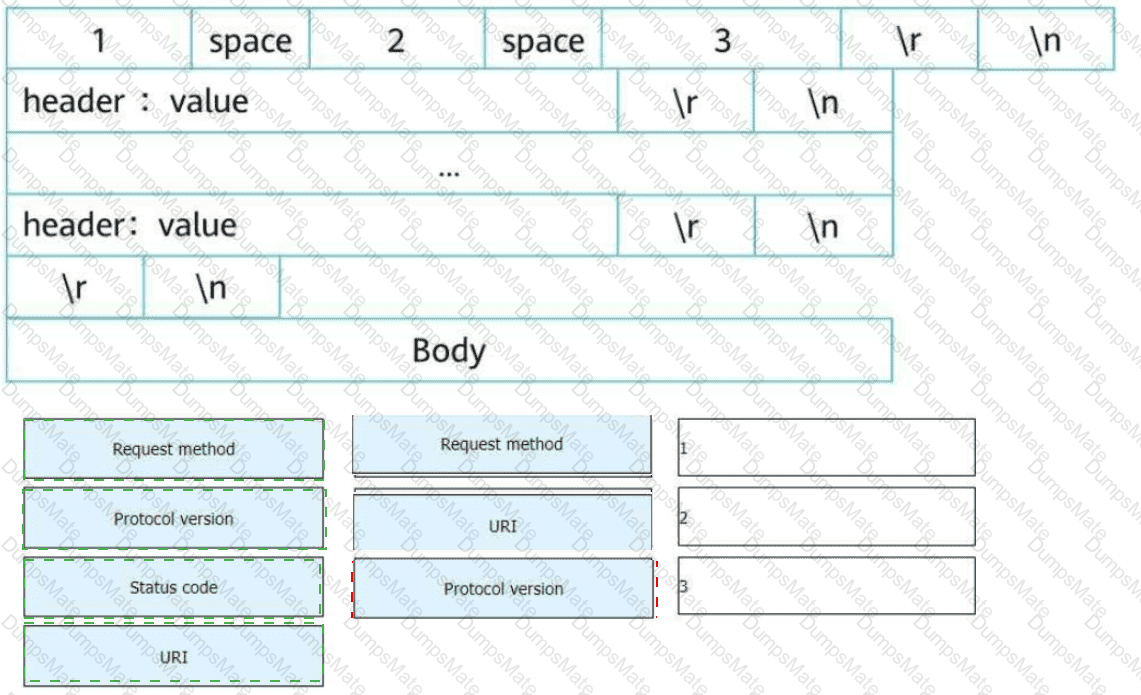
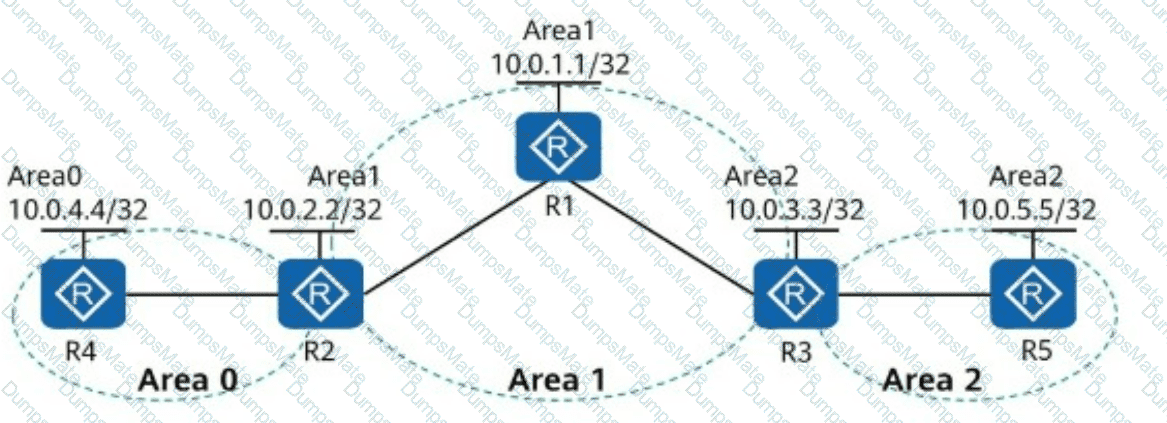
Understanding OSPF Multi-Area Routing
????OSPF (Open Shortest Path First) is a link-state routing protocolthat uses ahierarchical area designfor scalability.
????OSPF Areas in the Diagram:
Area 0 (Backbone Area):ContainsR4 (Loopback 10.0.4.4/32).
Area 1:ContainsR1 (Loopback 10.0.1.1/32) and R2 (Loopback 10.0.2.2/32).
Area 2:ContainsR3 (Loopback 10.0.3.3/32) and R5 (Loopback 10.0.5.5/32).
R1 and R2 connect Area 1 to Area 0.
R1 and R3 connect Area 1 to Area 2.
How OSPF Advertises Routes Across Areas
✅Intra-area communication (within the same area) is always possible.
✅Inter-area communication is possible if the ABR (Area Border Router) correctly advertises routes.
✅OSPF does NOT automatically advertise routes from one non-backbone area (e.g., Area 2) to another (e.g., Area 0) unless explicitly allowed.
Analysis of the Answer Choices:
❌A. 10.0.3.3 and 10.0.5.5 (Incorrect)
Both R3 (10.0.3.3) and R5 (10.0.5.5) are inArea 2.
R3 and R5 can communicate directly, but OSPF rules require an Area Border Router (ABR) to share routing information between areas.
Since no information is provided about inter-area route redistribution, we cannot confirm that R3 and R5 can reach each other.
❌B. 10.0.2.2 and 10.0.5.5 (Incorrect)
R2 (10.0.2.2) is in Area 1, and R5 (10.0.5.5) is in Area 2.
R2 does NOT have direct OSPF reachability into Area 2.
✅C. 10.0.2.2 and 10.0.3.3 (Correct)
R2 (10.0.2.2) is in Area 1, and R3 (10.0.3.3) is in Area 2.
R1 connects both Area 1 and Area 2, meaning R2 and R3 can communicate via R1.
R1 is the ABR (Area Border Router) between Area 1 and Area 2, so it will advertise routes from R3 to R2 and vice versa.
❌D. 10.0.4.4 and 10.0.2.2 (Incorrect)
R4 (10.0.4.4) is in Area 0 (Backbone), and R2 (10.0.2.2) is in Area 1.
R2 does NOT connect directly to Area 0, soR2 does not learn routes from Area 0 unless R1 explicitly redistributes them.
No explicit information about route redistribution is provided.
Final Answer: C (10.0.2.2 and 10.0.3.3)
✅Reference:Huawei HCIE-Datacom Guide – OSPF Multi-Area Routing & ABR Role
Real-World Application:
Enterprise WAN Networks:Multi-area OSPF is used toscale large enterprise networkswhile maintainingfast convergence.
Service Provider Networks:ABRs control route distribution, preventingunnecessary flooding of routing updates across areas.




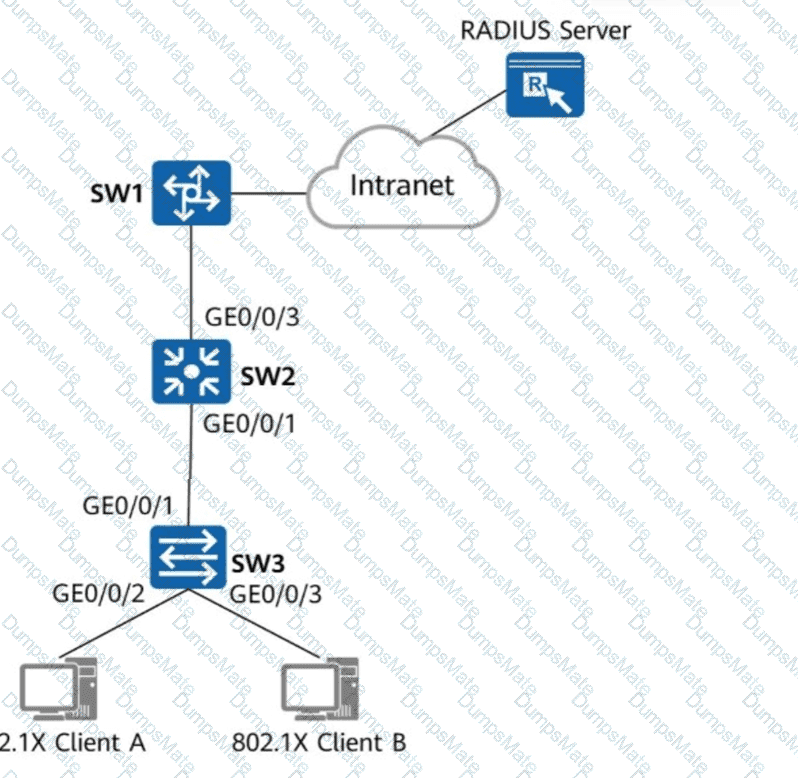
 A screenshot of a computer AI-generated content may be incorrect.
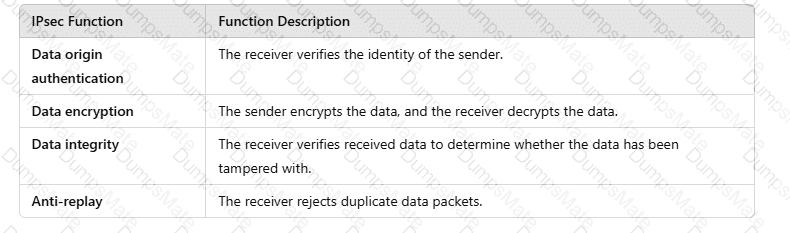
A screenshot of a computer AI-generated content may be incorrect.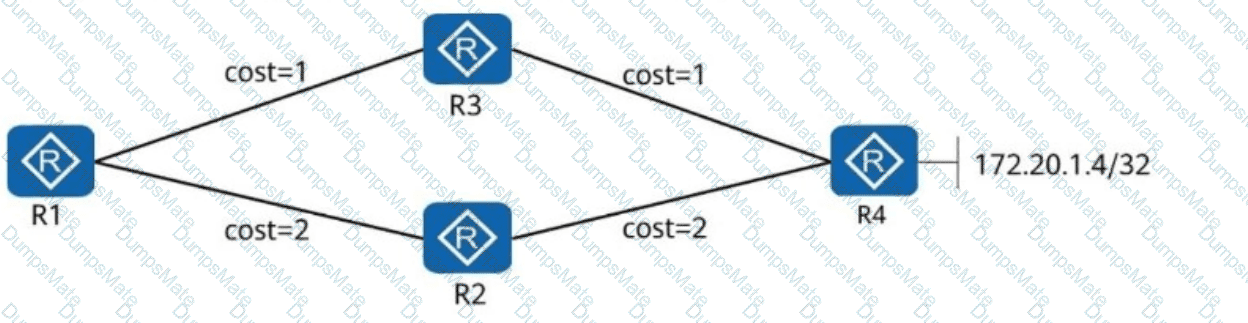

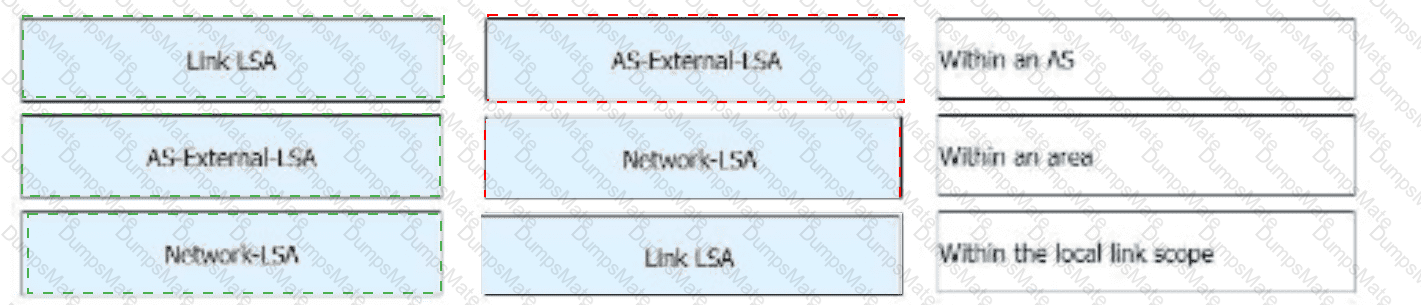
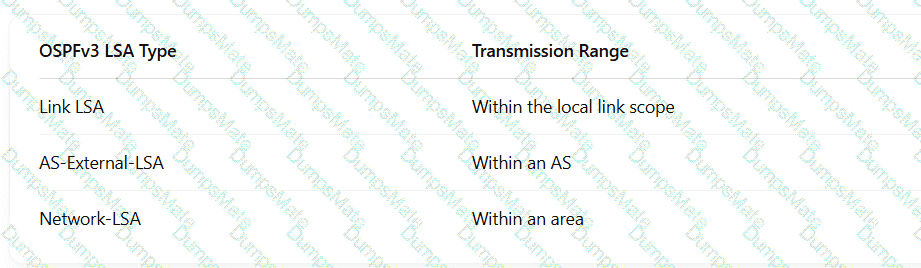 A screenshot of a computer AI-generated content may be incorrect.
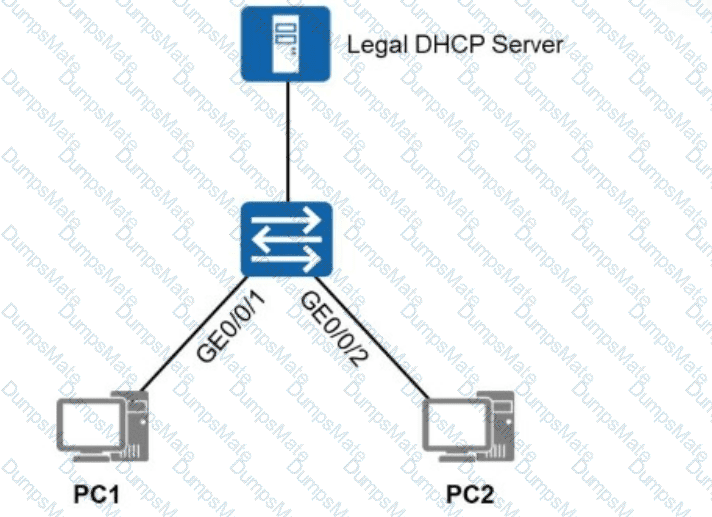
A screenshot of a computer AI-generated content may be incorrect.