Introduction to Security Zones:
Security zones are logical segments within a network designed to enforce security policies and control access. They help in segregating and securing different parts of the network.
Types of Security Zones:
Trusted Zone: This is the most secure zone, typically used for internal corporate networks where only trusted users have access.
Extranet: This zone allows controlled access to external partners, vendors, or customers.
VPN (Virtual Private Network): While VPNs are used to create secure connections over the internet, they are not a security zone themselves.
Public Zone: This zone is the least secure and is typically used for public-facing services accessible by anyone.
Trusted Zone Implementation:
The trusted zone is configured to include internal corporate users and resources. Access controls, firewalls, and other security measures ensure that only authorized personnel can access this zone.
Internal network segments, such as the finance department, HR, and other critical functions, are usually placed in the trusted zone.
Example Configuration:
Firewall Rules: Set up rules to allow traffic only from internal IP addresses.
Access Control Lists (ACLs): Implement ACLs on routers and switches to restrict access based on IP addresses and other criteria.
Segmentation: Use VLANs and subnetting to segment and isolate the trusted zone from other zones.
Explanation of the Options:
A. Extranet: Suitable for external partners, not for internal-only access.
B. Trusted: The correct answer, as it provides controlled access to internal corporate users.
C. VPN: A method for secure remote access, not a security zone itself.
D. Public: Suitable for public access, not for internal corporate users.
Conclusion:
Implementing a trusted zone is the best solution for controlling access within a corporate network. It ensures that only trusted internal users can access sensitive resources, enhancing network security.
[References:, CompTIA Network+ guide detailing security zones and their implementation in a corporate network (see page Ref 9†Basic Configuration Commands)., , , , , , , ]




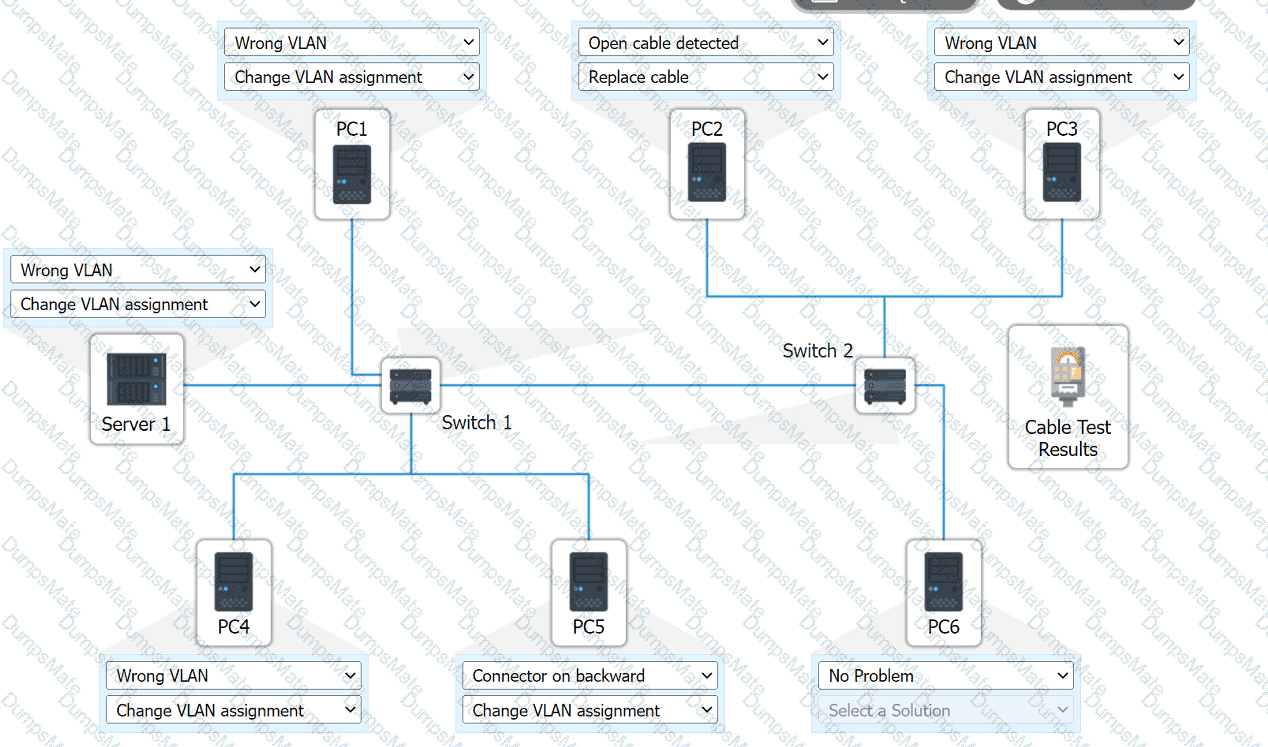 A computer network diagram with many boxes and text AI-generated content may be incorrect.
A computer network diagram with many boxes and text AI-generated content may be incorrect.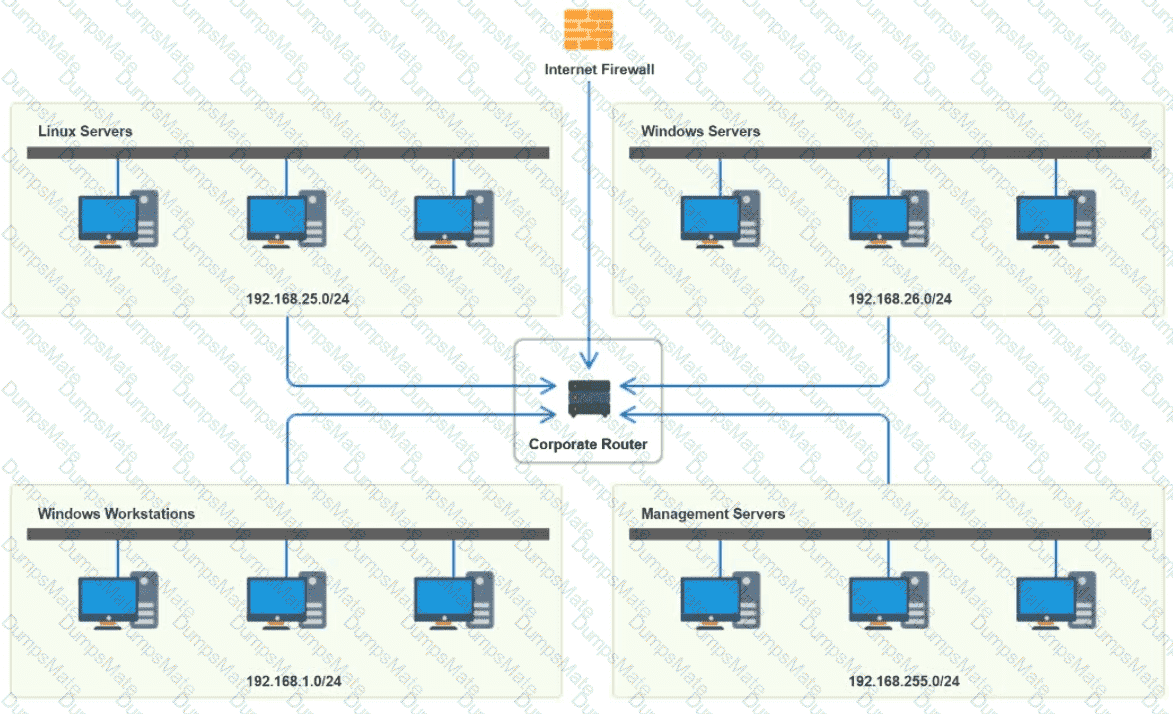
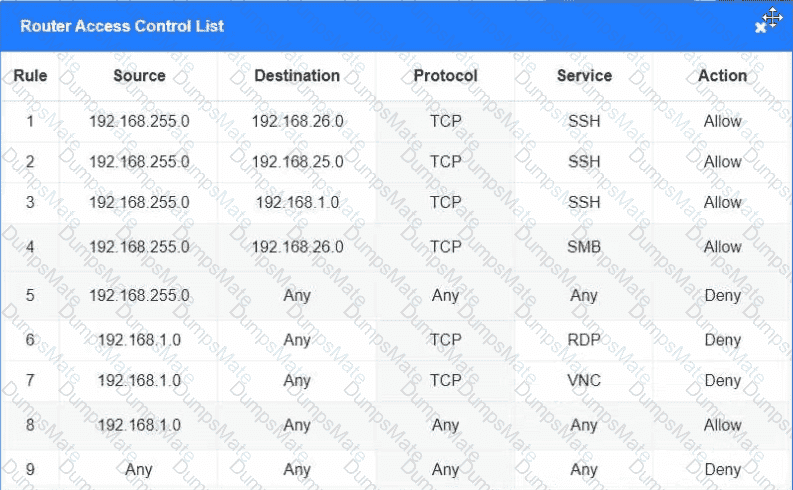 A screenshot of a computer screen AI-generated content may be incorrect.
A screenshot of a computer screen AI-generated content may be incorrect.
