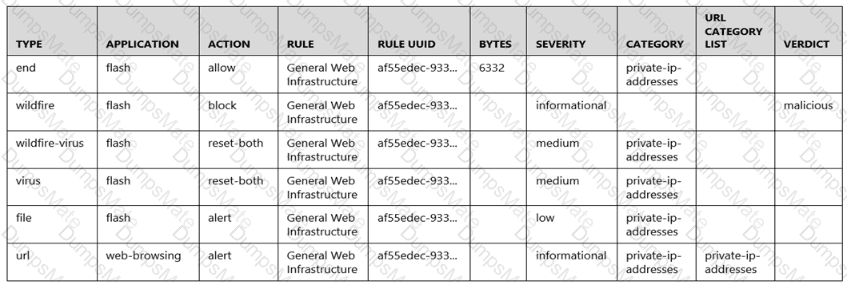
Advanced WildFire analyzes both the webpage linked by the URL and any files (like PE files) that are downloaded as a result of clicking that link. This includes checking the linked webpage for malicious content and sending any downloaded files for further analysis to determine their behavior and potential malicious intent.
The PCNSA Study Guide outlines that WildFire inspects and analyzes both content downloaded and webpages involved when integrated into the organization's security profile. This dual-layered approach ensures comprehensive protection against threats from both the webpage and its payloads.
Step-by-Step Explanation
Link Clicked and File Download Triggered:
When the user clicks the link, their action initiates the download of a file, in this case, a Portable Executable (PE) file.
URL Inspection by WildFire:
The URL is immediately inspected for potential threats. This involves analyzing the webpage associated with the link to detect:
Known malicious indicators.
Suspicious elements like embedded scripts, links, or calls to external resources.
Forwarding the PE File for Analysis:
The PE file downloaded as a result of clicking the link is sent to the WildFire cloud or on-premises appliance for detailed behavior-based analysis.
Dynamic and Static Analysis:
Static Analysis: WildFire examines the PE file's attributes without executing it, looking for:
Suspicious code patterns.
Known malicious signatures.
Anomalous PE header details (e.g., timestamp irregularities, unexpected sections).
Dynamic Analysis: The file is executed in a controlled virtual environment to observe:
Behavioral anomalies, like privilege escalation attempts.
Network communication, such as connections to Command and Control (C2) servers.
File system modifications or registry changes indicative of malicious intent.
Threat Verdict:
Based on its findings, WildFire classifies the URL and PE file into one of the following categories:
Benign.
Grayware.
Malware.
Phishing.
Automated Response:
If either the webpage or the PE file is deemed malicious, the firewall takes predefined actions:
Blocking access to the webpage.
Quarantining or blocking the downloaded file.
Generating a detailed alert or log entry for administrators.
Signature Update:
WildFire automatically creates a signature for the detected threat and distributes it globally. This ensures that other systems in the WildFire network are protected against the same threat.
Advanced WildFire Configuration and Behavior
Forwarding File Types:
The WildFire analysis profile must be configured to forward relevant file types. In this case:
PE files are commonly forwarded by default since they are a known vector for malware.
Administrators can define custom forwarding rules based on file type and traffic.
Integration with the Security Profile:
WildFire integrates with other security profiles (e.g., Antivirus, Anti-Spyware, URL Filtering).
URL Filtering ensures that the link itself is categorized and blocked if malicious.
WildFire's output informs and updates the threat prevention database dynamically.
Why the Answer is B?
WildFire performs dual analysis:
The linked webpage is checked for malicious scripts or phishing attempts.
The PE file downloaded is analyzed for malware through both static and dynamic methods.
This layered analysis ensures robust protection against modern threats, which often combine malicious webpages with harmful payloads.
Document References:
PCNSA Study Guide: Domain 4, Section 4.1.5 ("WildFire Analysis") explains the WildFire analysis process in detail, emphasizing its role in inspecting files and URLs for malicious behavior.
Palo Alto Networks WildFire Admin Guide:
This guide details file forwarding configurations, supported file types, and the global signature distribution process.
PAN-OS Admin Guide:
Sections on Security Profiles and URL Filtering elaborate on how WildFire integrates with other threat prevention mechanisms.