DMARC (Domain-based Message Authentication, Reporting & Conformance) is an email authentication protocol that helps prevent email spoofing and phishing. It builds on SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to provide a mechanism for email senders and receivers to improve and monitor the protection of the domain from fraudulent email.
Understanding DMARC:
SPF: Defines which IP addresses are allowed to send emails on behalf of a domain.
DKIM: Provides a way to check that an email claiming to come from a specific domain was indeed authorized by the owner of that domain.
DMARC: Uses SPF and DKIM to determine the authenticity of an email and specifies what action to take if the email fails the authentication checks.
Implementing DMARC:
Create a DMARC policy in your DNS records. This policy can specify to reject, quarantine, or take no action on emails that fail SPF or DKIM checks.
Example DMARC record: v=DMARC1; p=reject; rua=mailto:dmarc-reports@yourdomain.com;
Benefits of DMARC:
Helps to prevent email spoofing and phishing attacks.
Provides visibility into email sources through reports.
Enhances domain reputation by ensuring only legitimate emails are sent from the domain.
DMARC Record Components:
v: Version of DMARC.
p: Policy for handling emails that fail the DMARC check (none, quarantine, reject).
rua: Reporting URI of aggregate reports.
ruf: Reporting URI of forensic reports.
pct: Percentage of messages subjected to filtering.
Real-World Example:
A company sets up a DMARC policy with p=reject to ensure that any emails failing SPF or DKIM checks are rejected outright, significantly reducing the risk of phishing attacks using their domain.
References from Pentesting Literature:
In "Penetration Testing - A Hands-on Introduction to Hacking," DMARC is mentioned as part of email security protocols to prevent phishing.
HTB write-ups often highlight the importance of DMARC in securing email communications and preventing spoofing attacks.
Step-by-Step ExplanationReferences:
Penetration Testing - A Hands-on Introduction to Hacking
HTB Official Writeups
======




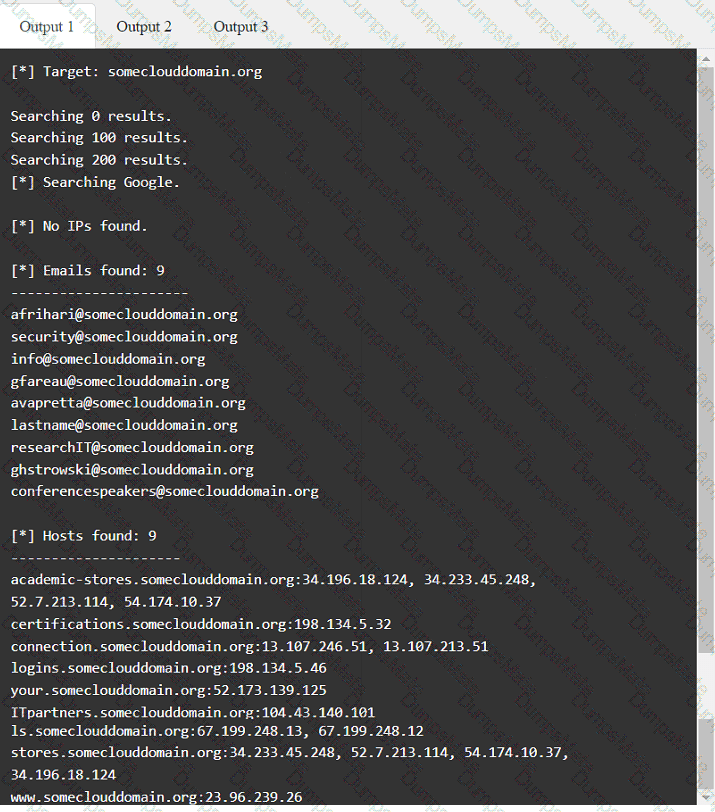
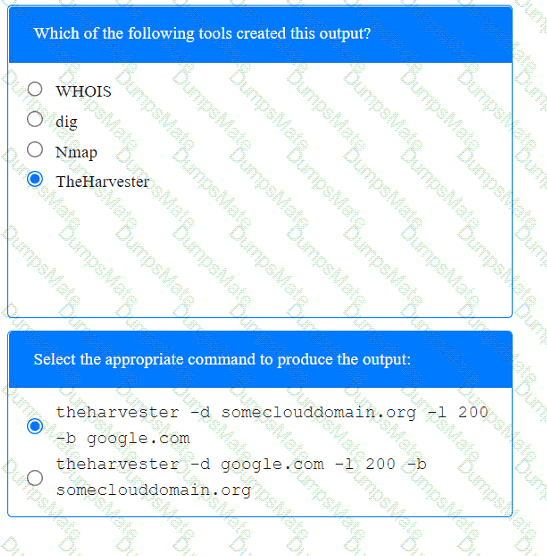
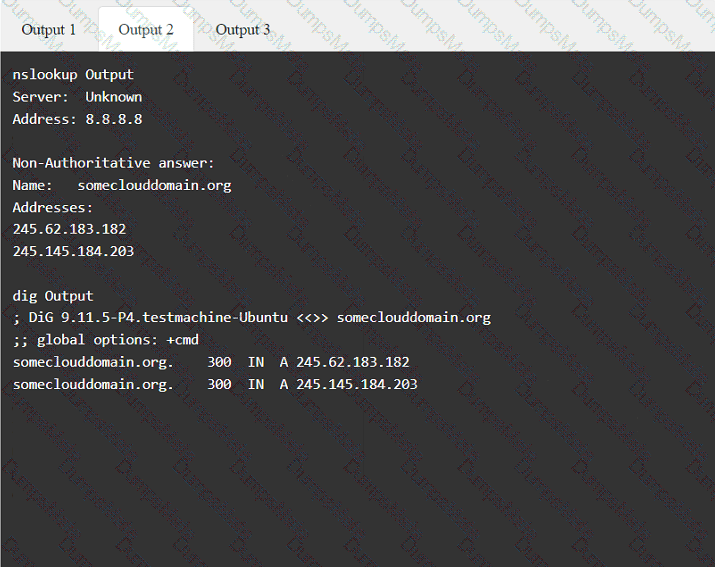
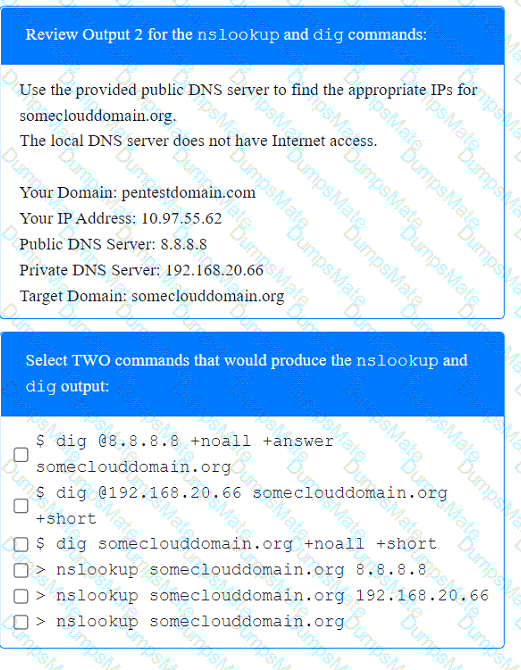
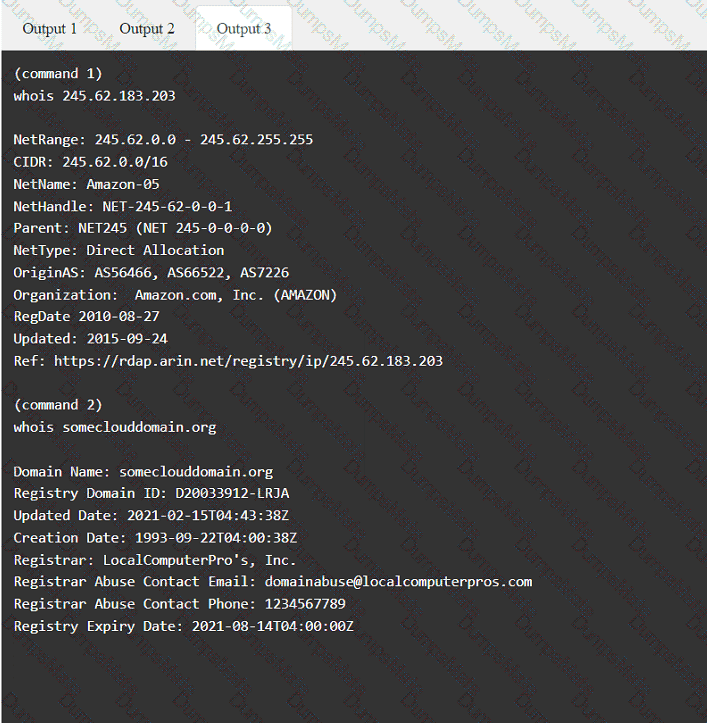
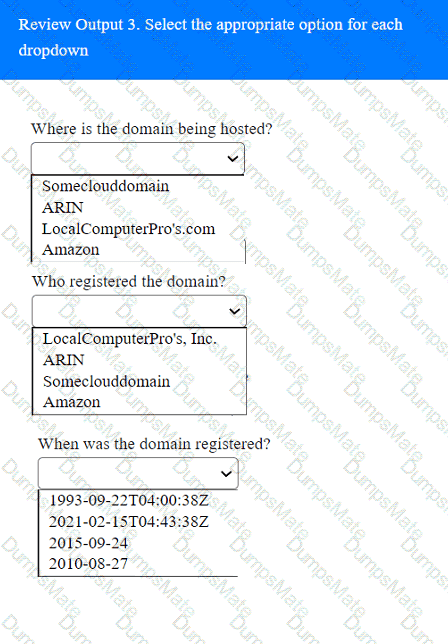
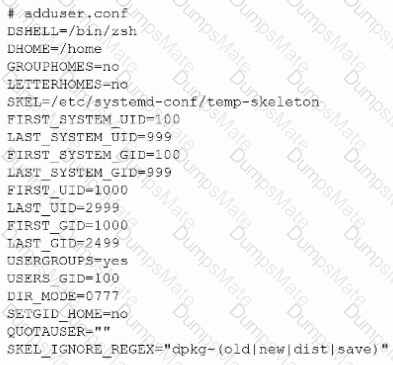
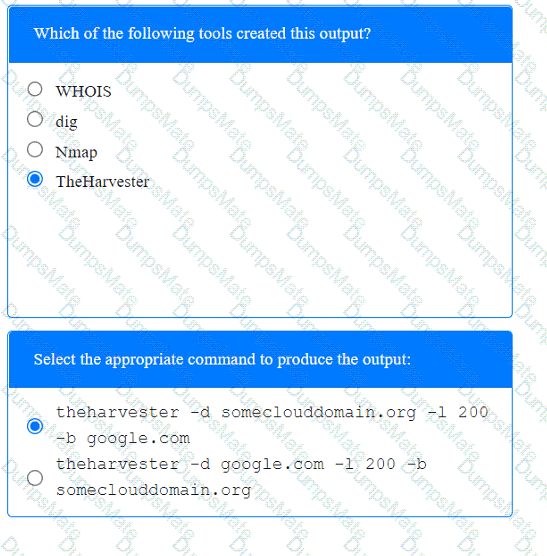 A screenshot of a computer Description automatically generated
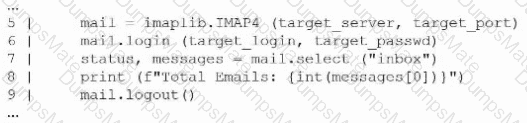
A screenshot of a computer Description automatically generated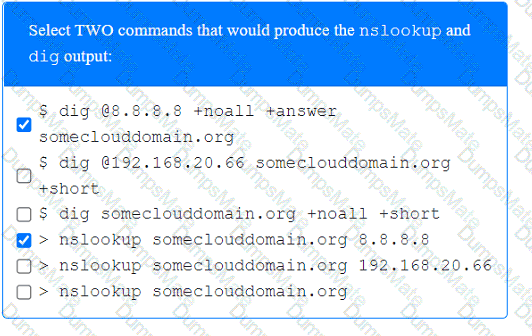 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated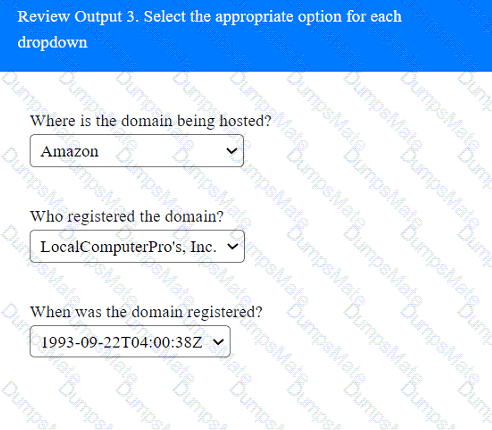 A screenshot of a computer Description automatically generated
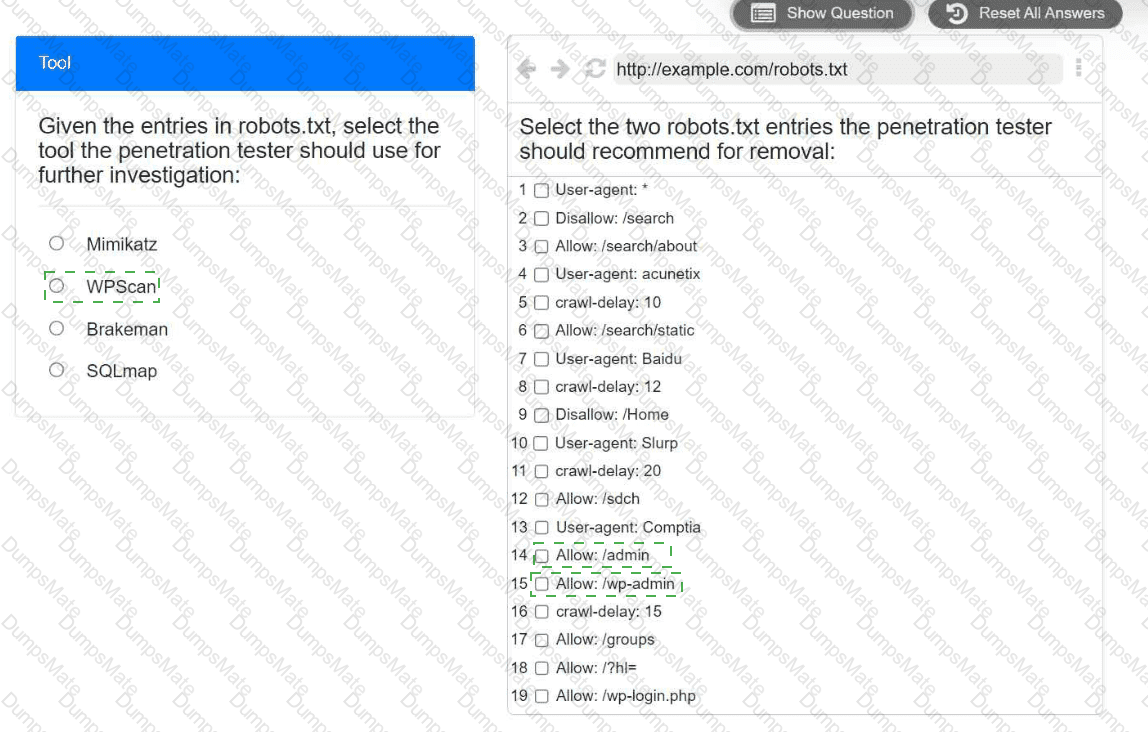
A screenshot of a computer Description automatically generated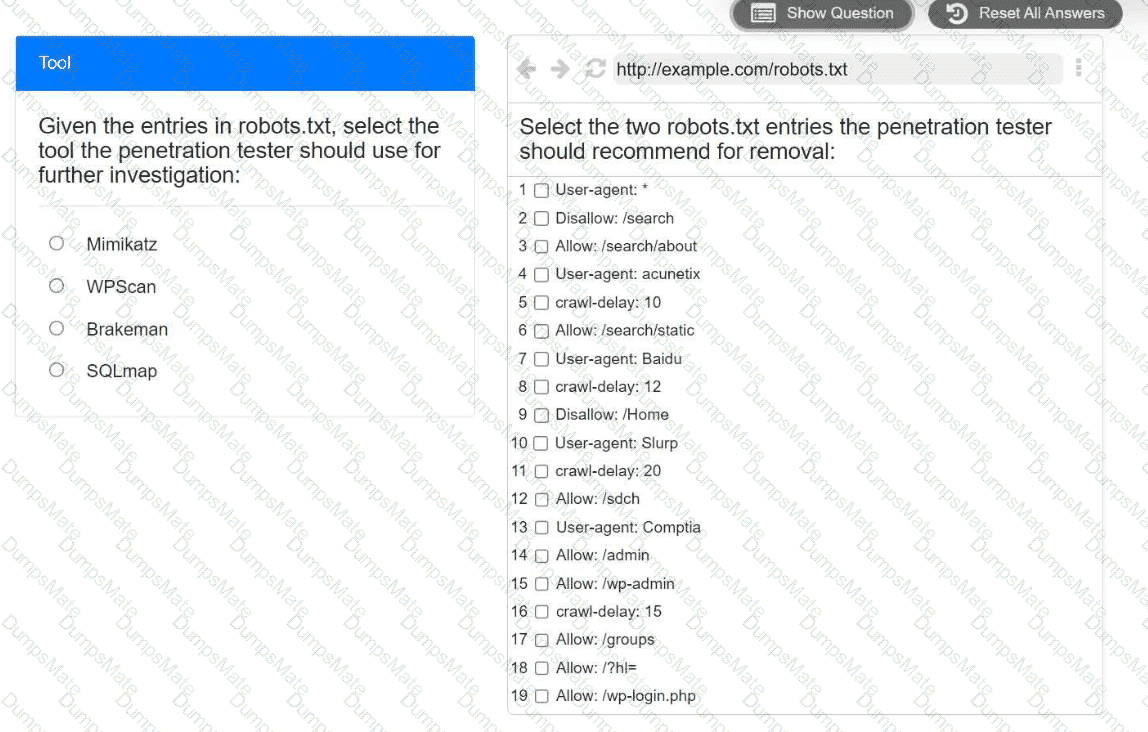
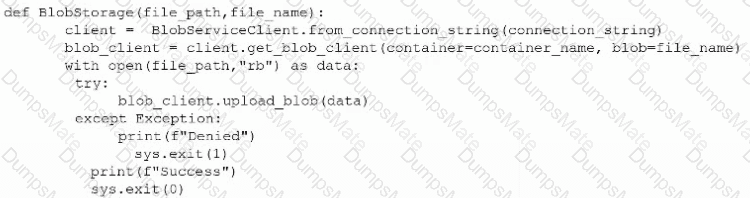
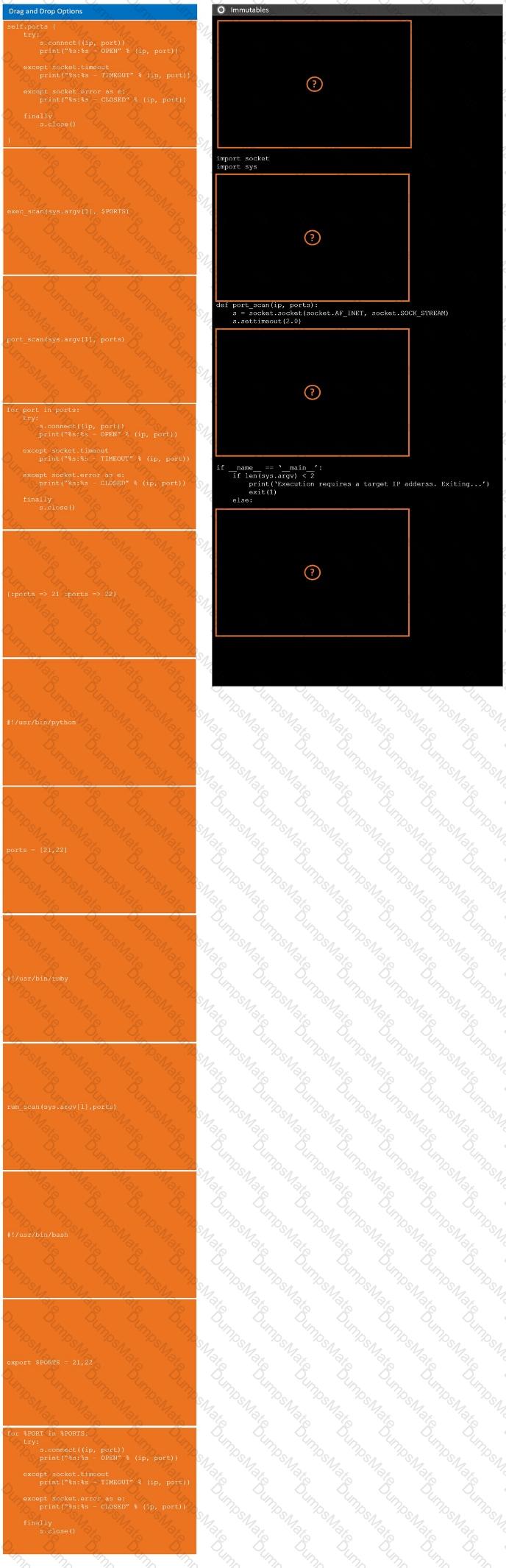
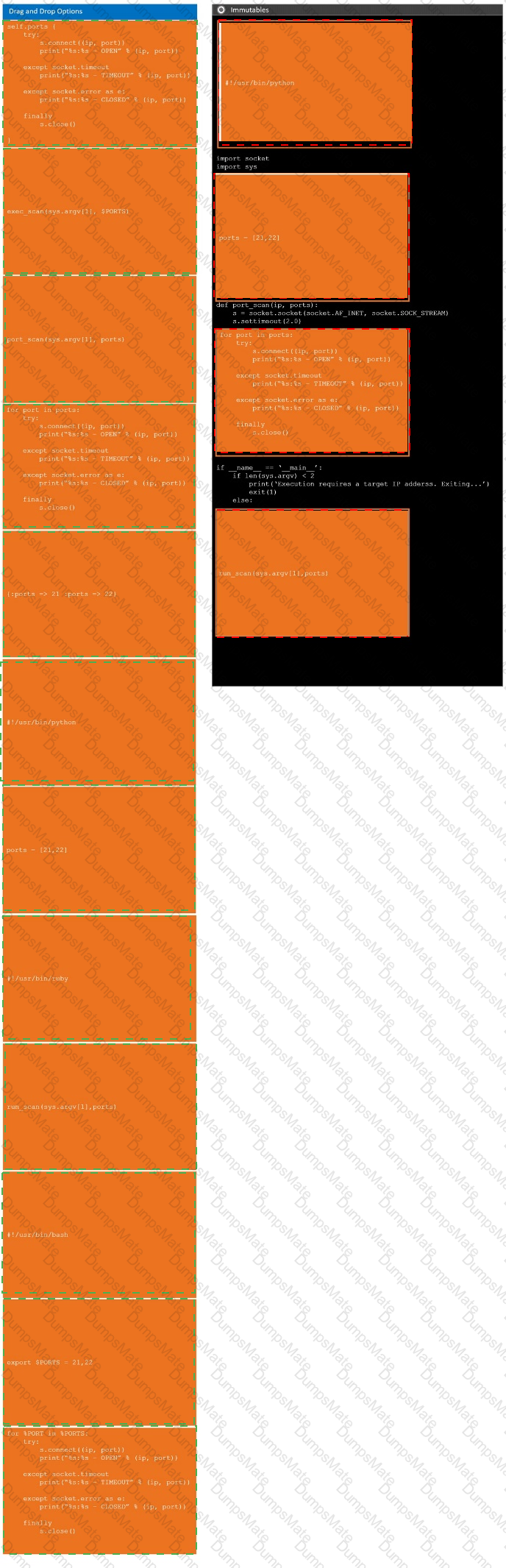
 A computer screen shot of a computer Description automatically generated
A computer screen shot of a computer Description automatically generated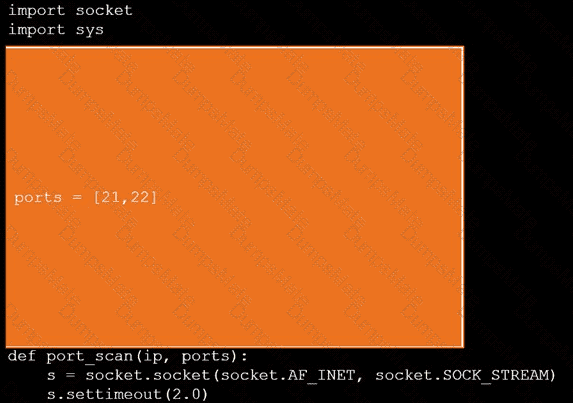 A screen shot of a computer Description automatically generated
A screen shot of a computer Description automatically generated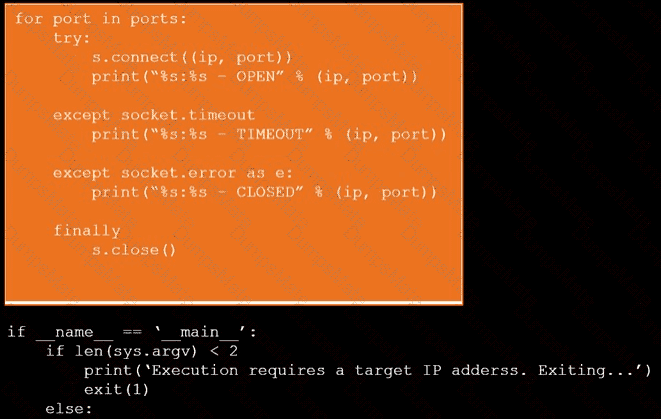 A computer screen with white text Description automatically generated
A computer screen with white text Description automatically generated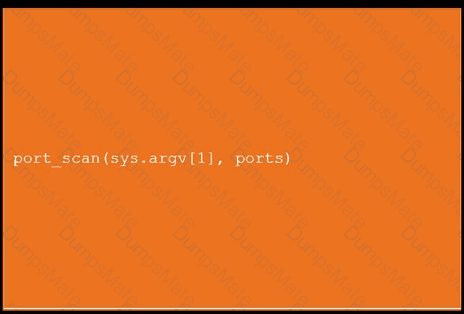 An orange screen with white text Description automatically generated
An orange screen with white text Description automatically generated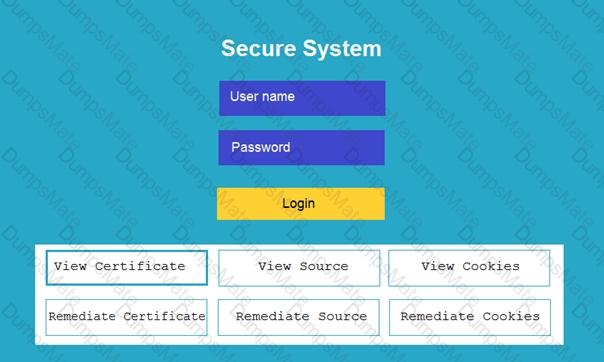
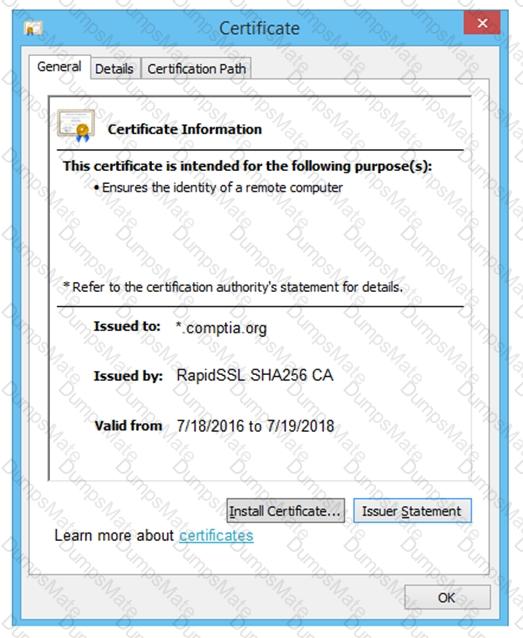

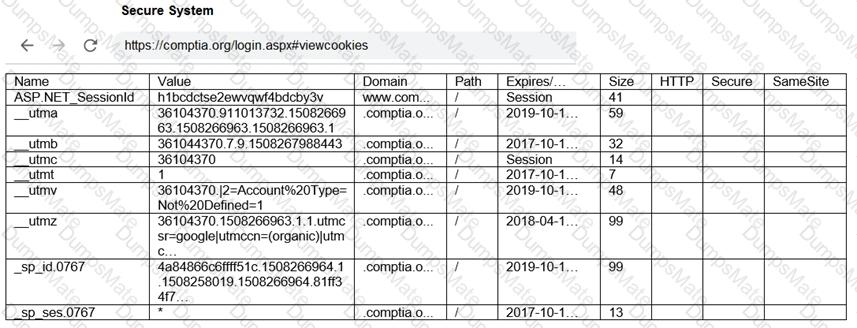
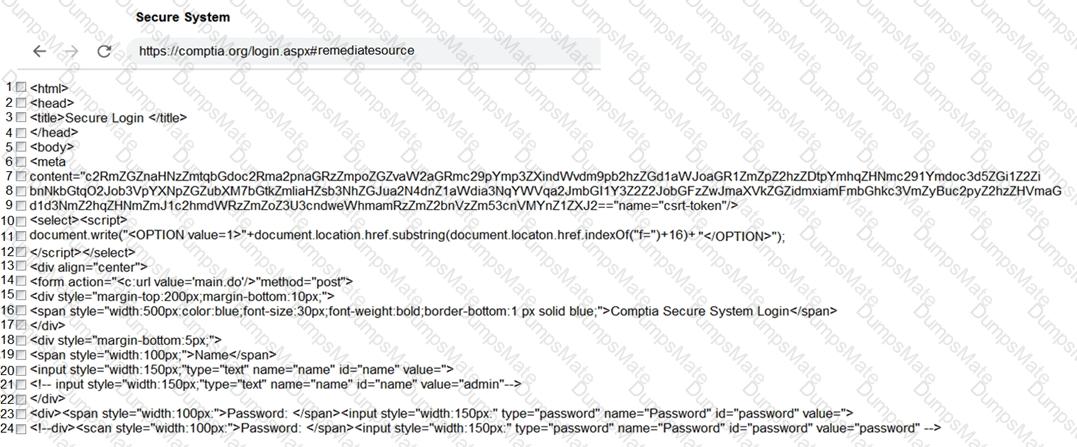
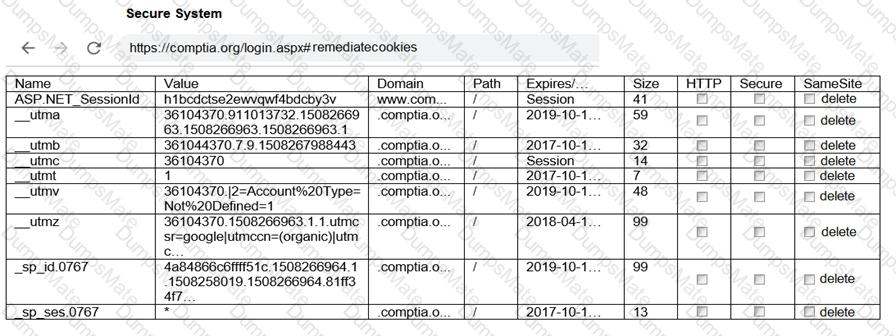
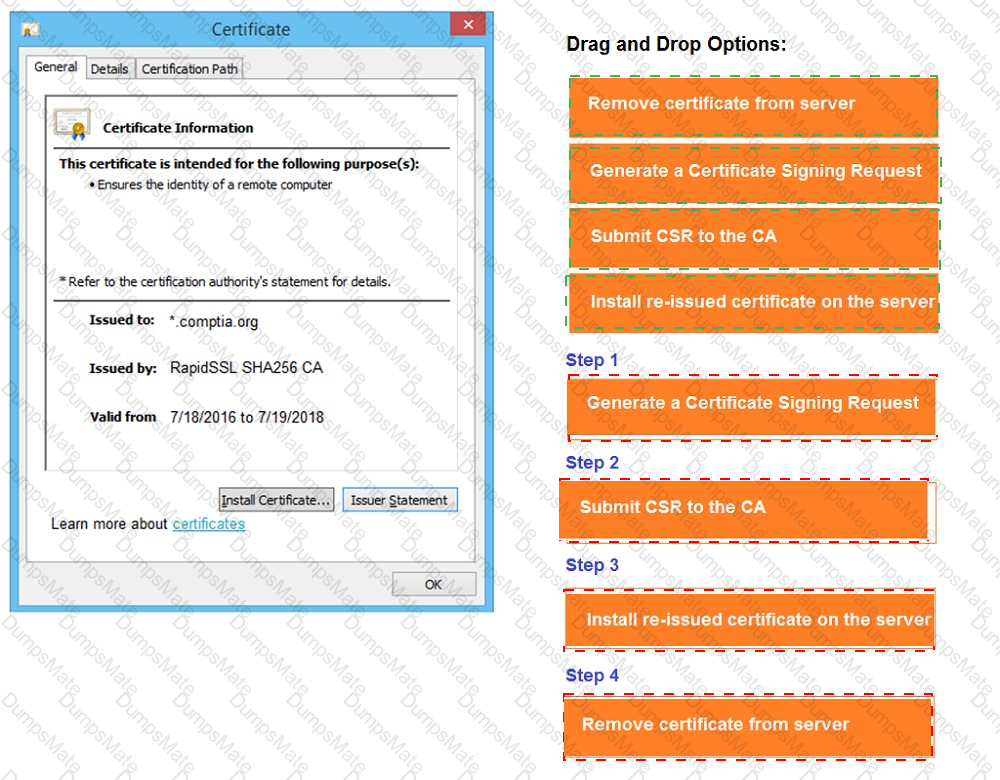
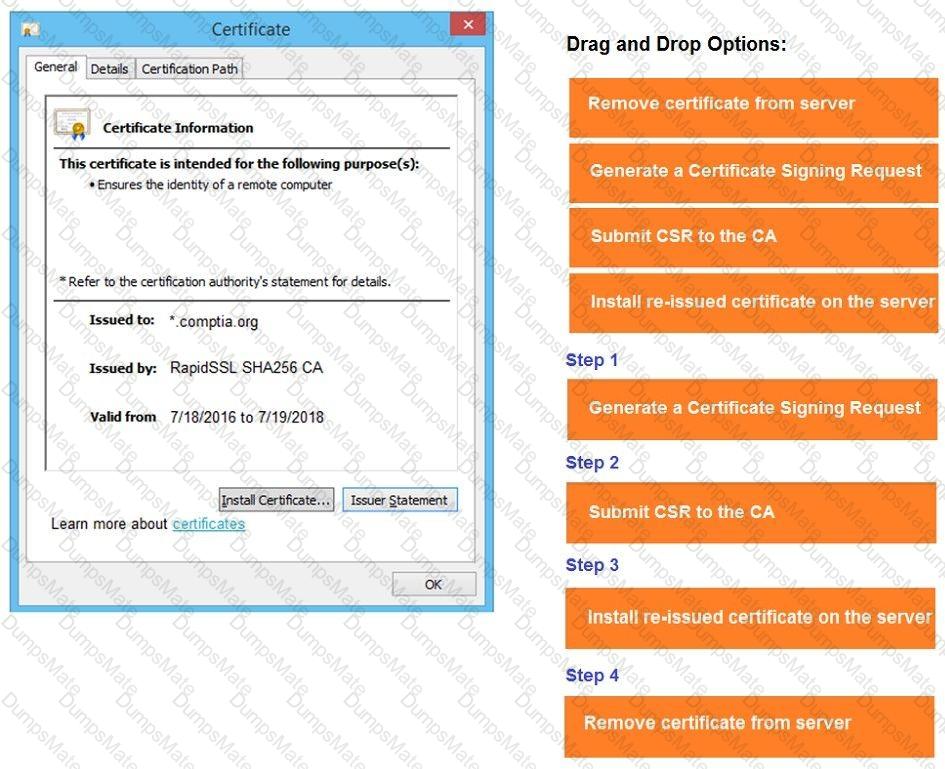 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated
