You have three Microsoft Entra tenants named Tenant 1. Tenant2. and Tenant3.
You have three Azure subscriptions named Sub1, Sub2, and Sub3. Each tenant is associated with multiple Azure subscriptions.
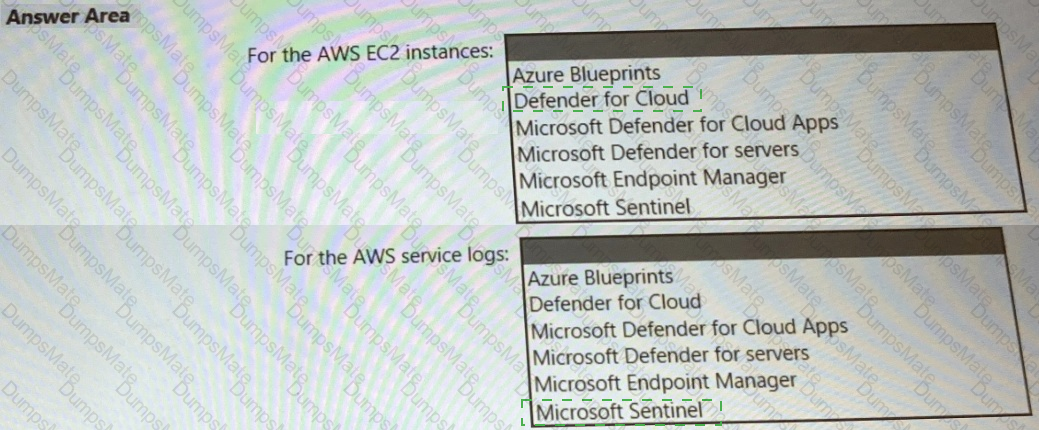
Each subscription contains a single Microsoft Sentinel workspace as shown in the following table.
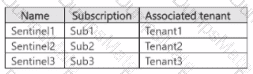
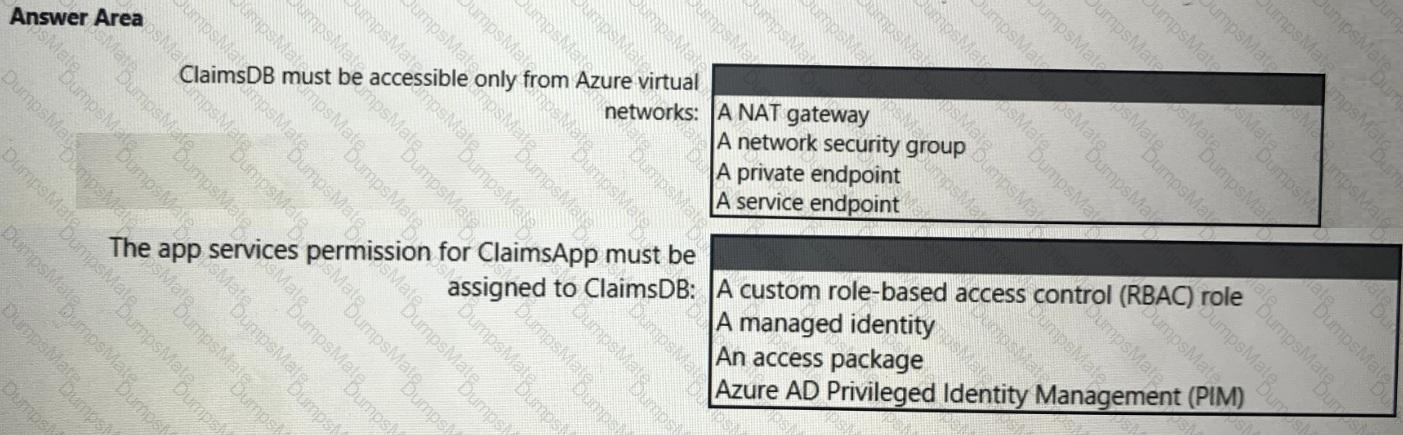
You need to recommend a solution that meets the following requirements:
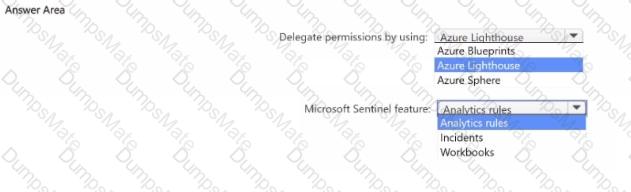
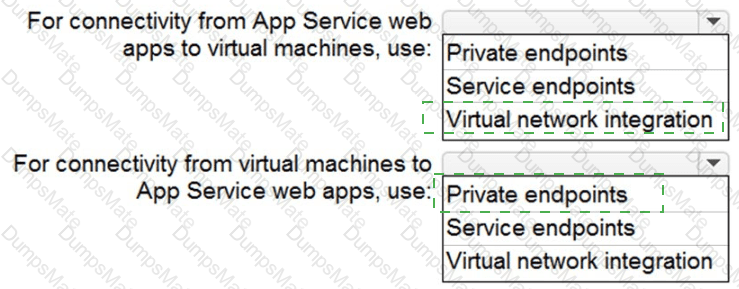
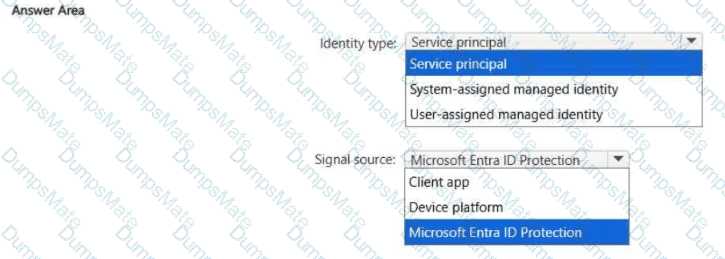
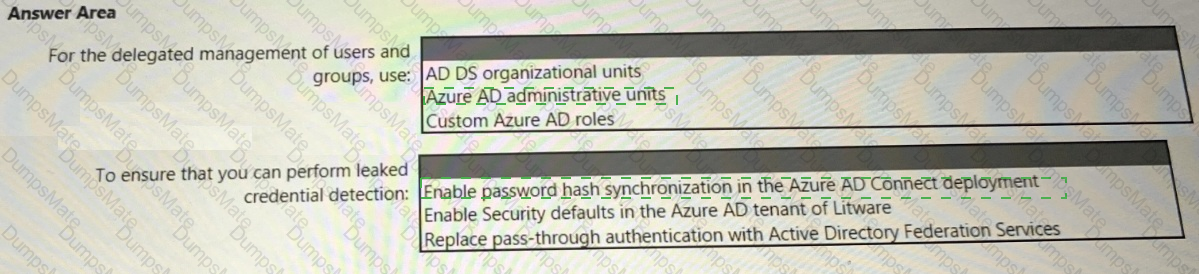
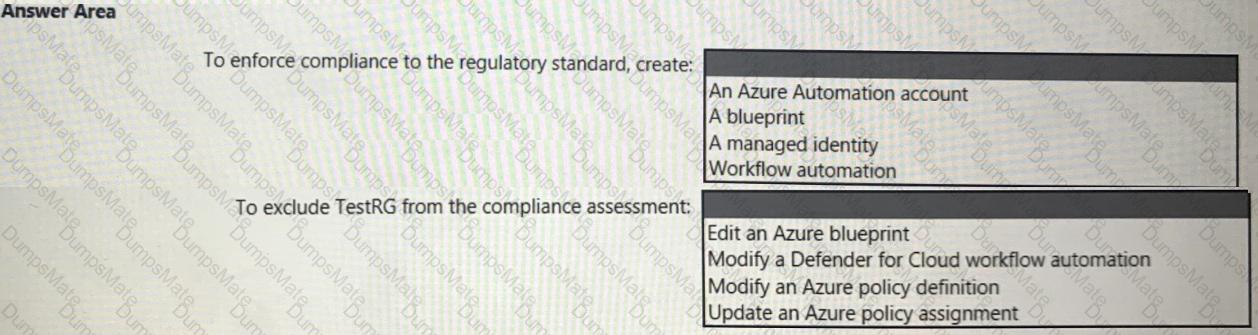
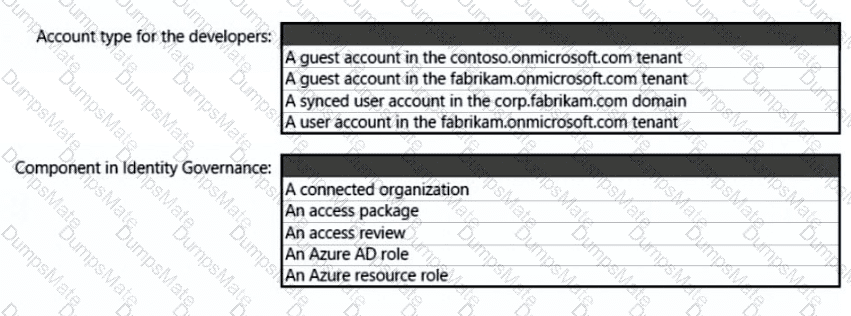
• Ensures that the users in Tenant1 can manage the resources in Sub2 and Sub3 without having to switch subscriptions or sign in to a different tenant
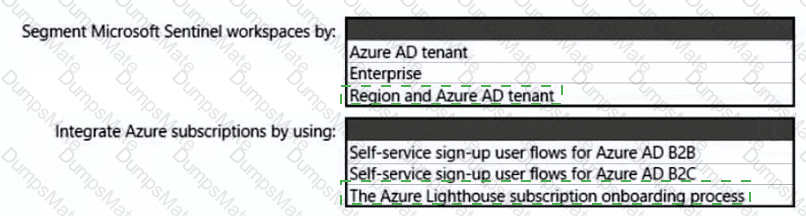
• Implements multiple workspace view for Sentinel2 and Sentinel3
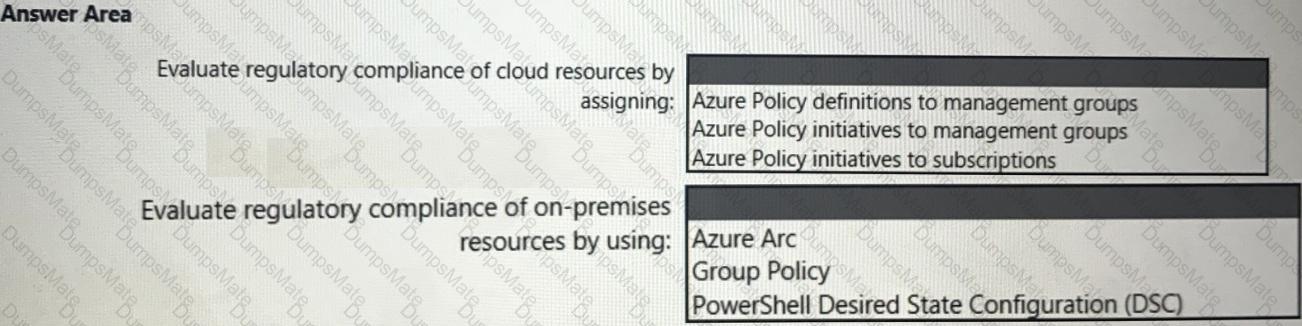
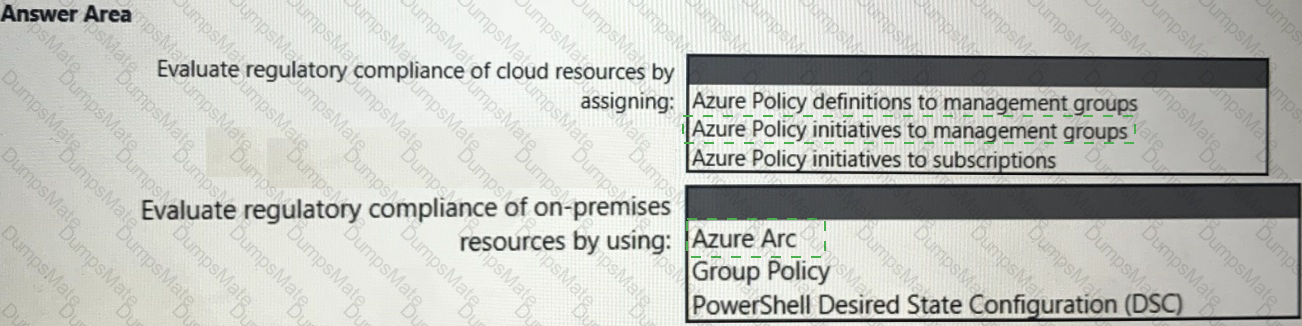
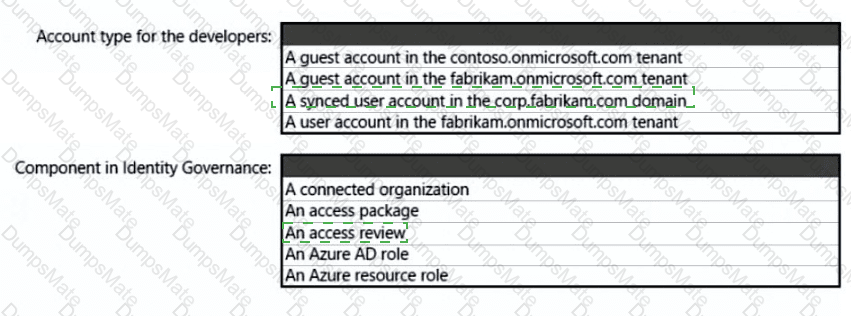
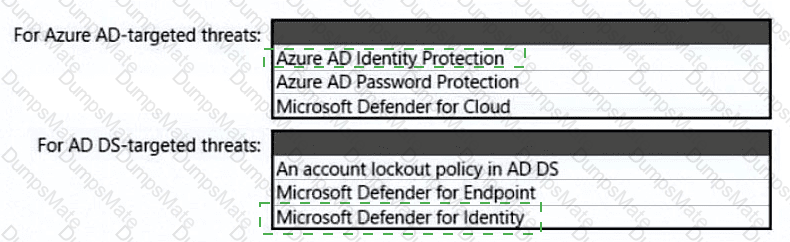
What should you use to delegate permissions, and which Microsoft Sentinel feature will users be able to manage in multiple workspace view? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.