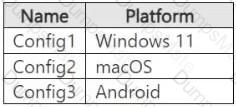
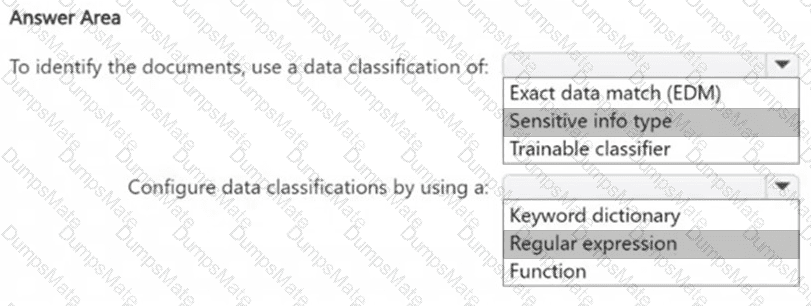
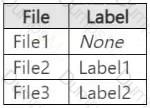
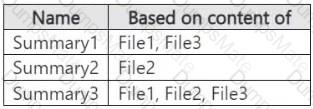
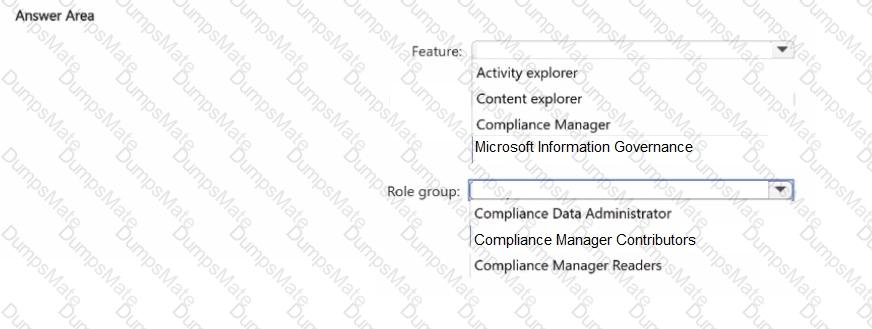
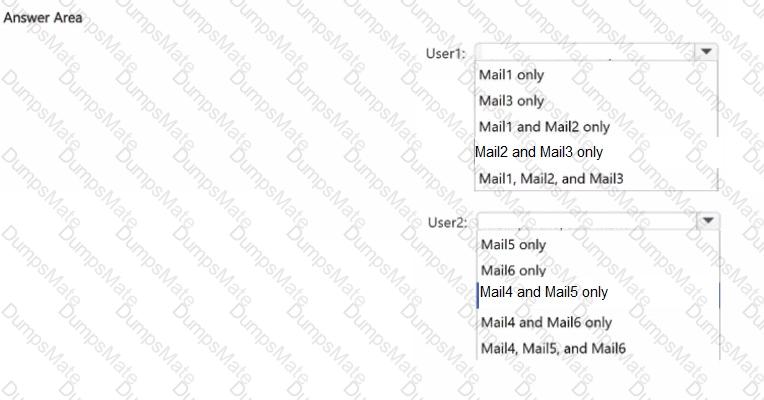
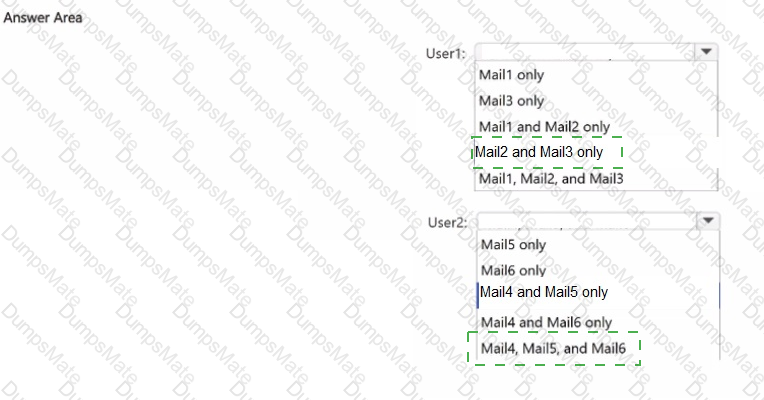
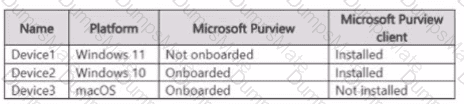
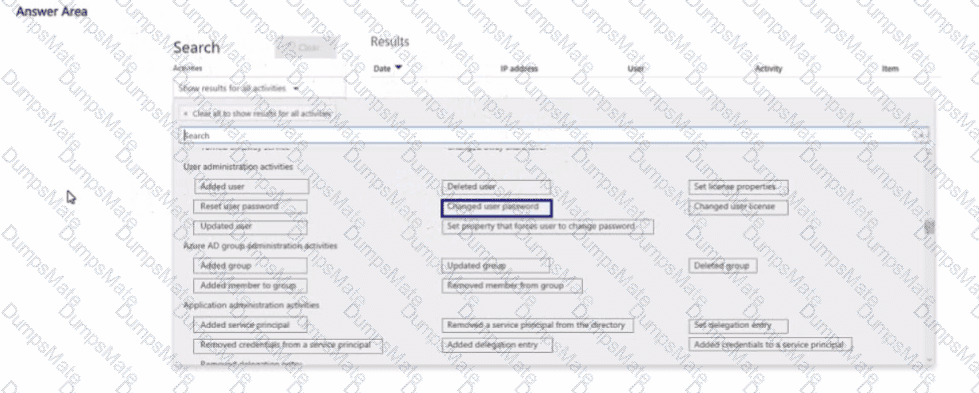
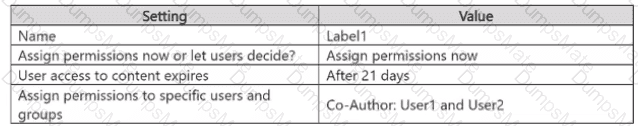
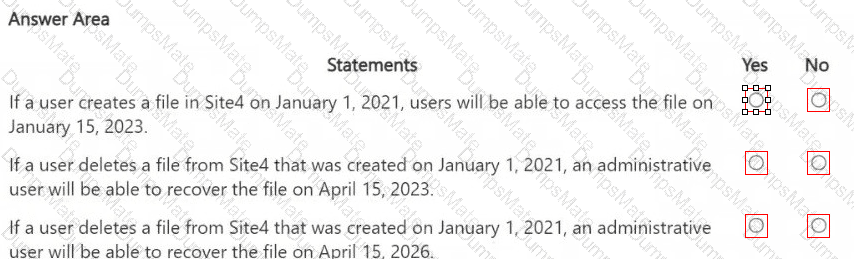
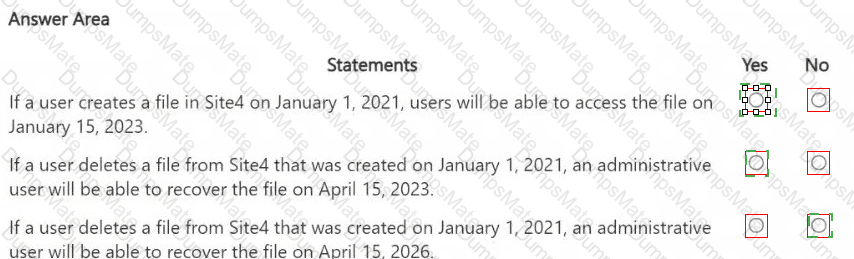
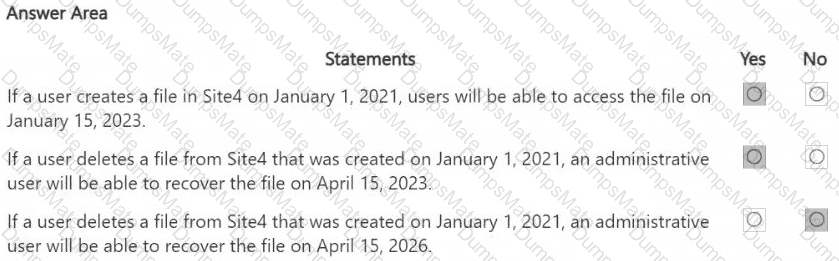
Step 1 – Scenario
You need to create a Microsoft Purview Insider Risk Management policy that detects data theft from SharePoint Online by users who have submitted their resignation or are close to termination.
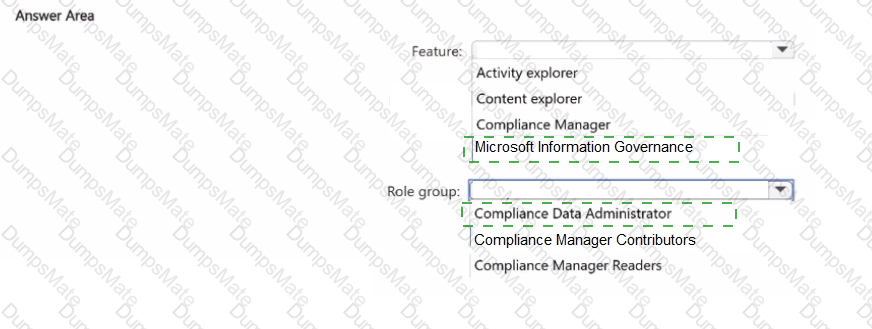
Step 2 – Understanding how insider risk management works
Insider Risk policies rely on signals that identify potential risk events. These signals include:
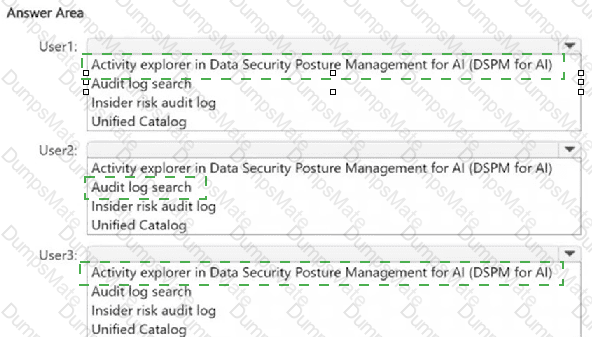
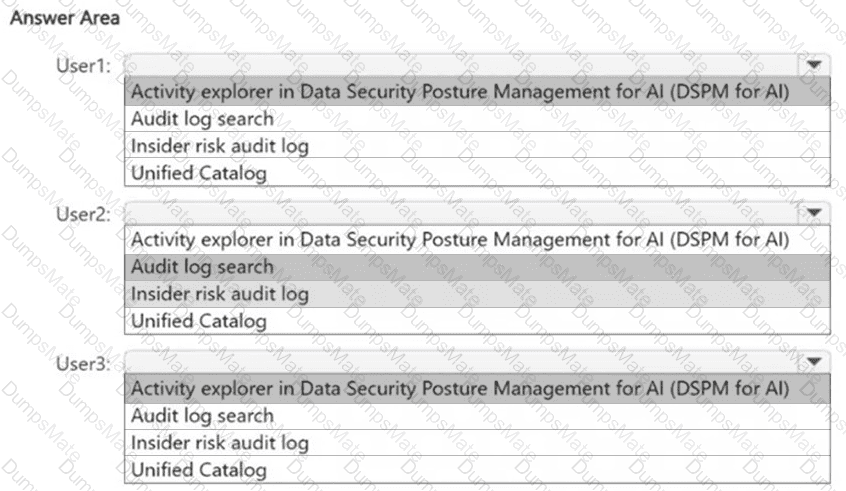
HR data (resignation dates, termination notices).
Office activity indicators (file downloads, sharing, printing).
Device indicators (file copy to USB, printing).
Physical access (badge-in/badge-out).
Step 3 – Why HR signals are required here
To detect resignation or termination risk events, Microsoft Purview must first know which users are flagged by HR.
This is done by configuring an HR data connector, which imports employee termination/resignation data from HR systems (Workday, SAP SuccessFactors, or CSV import).
Without this HR data connector, Purview has no knowledge of employees’ resignation or termination timelines, and the policy cannot function.
Step 4 – Why not the other options
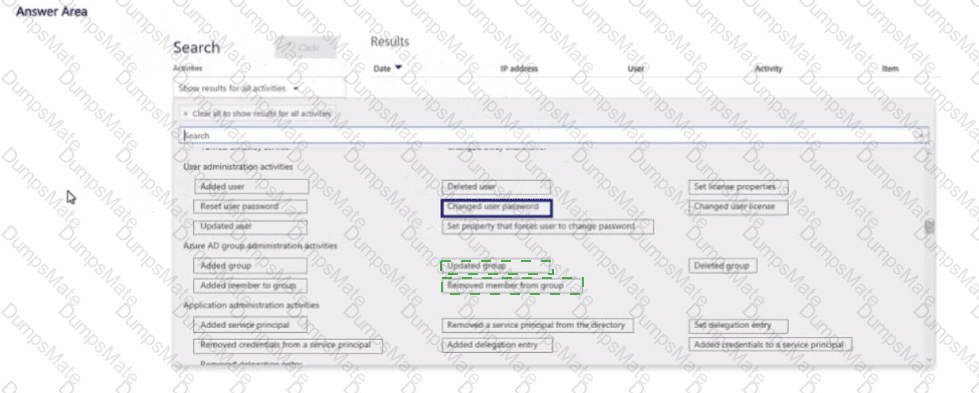
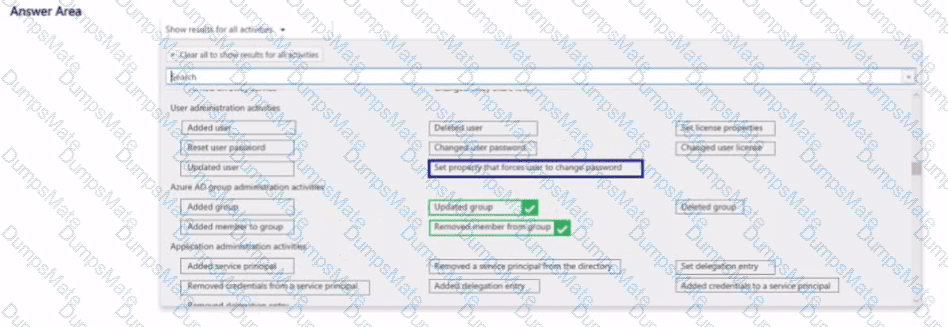
B. Configure Office indicators: These detect risky activity (downloads, sharing), but cannot determine resignation status. They are used after HR signals identify at-risk users.
C. Configure a Physical badging connector: Useful for detecting anomalous physical access, but irrelevant to resignation-based detection.
D. Onboard devices to Microsoft Defender for Endpoint: Required for device activity signals, not for HR resignation detection.
Step 5 – Microsoft Reference
Microsoft documentation states: “To use HR resignation/termination triggers, you must configure an HR connector to import resignation and termination data into insider risk management.”