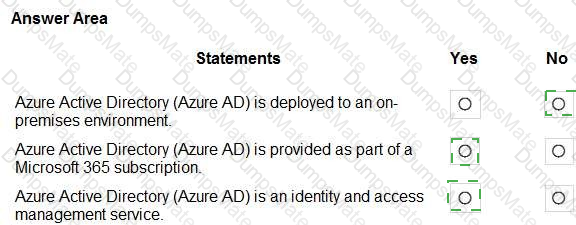
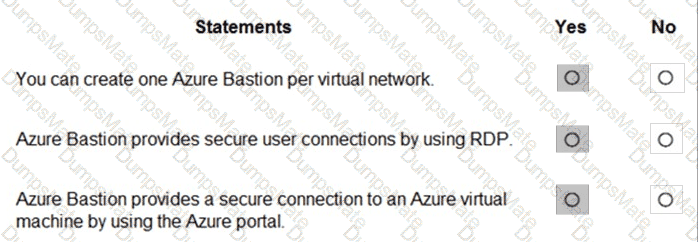
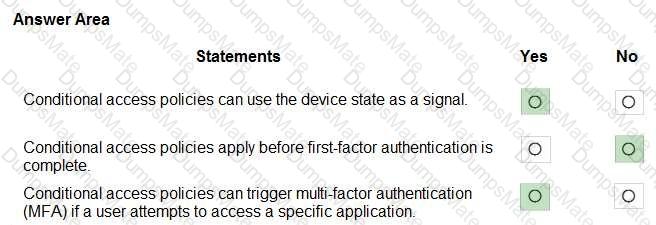
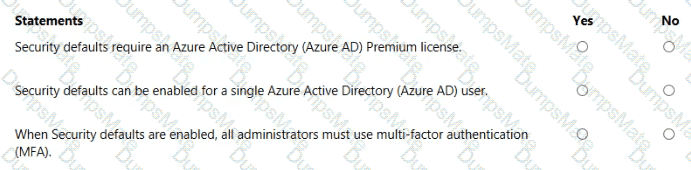
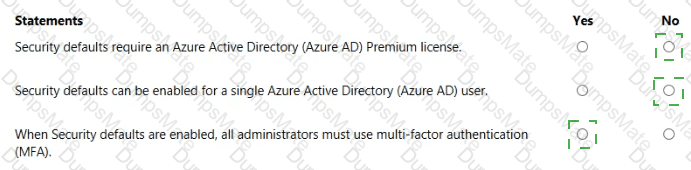
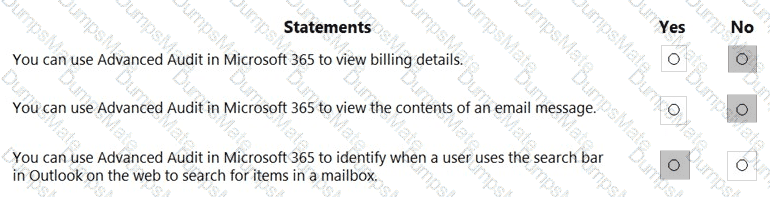
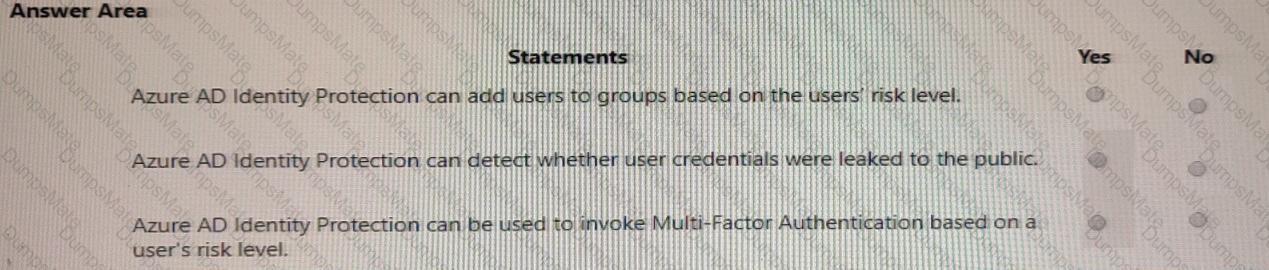
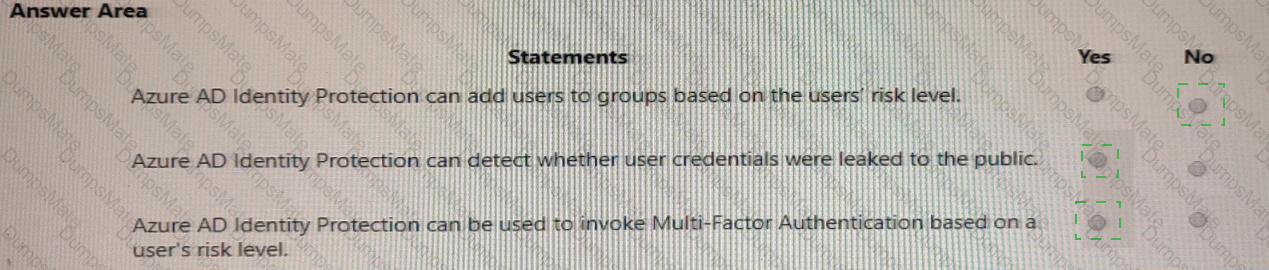
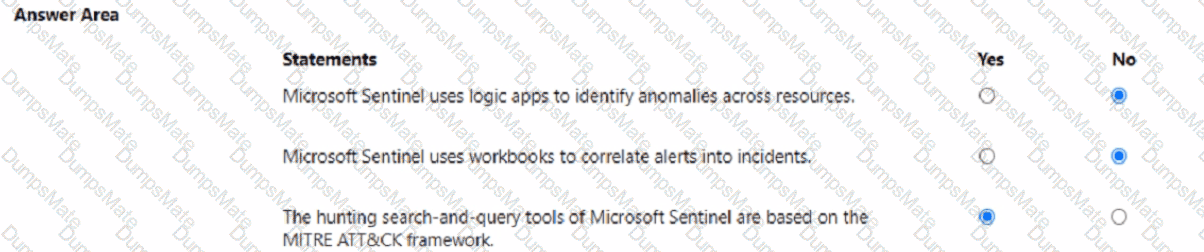
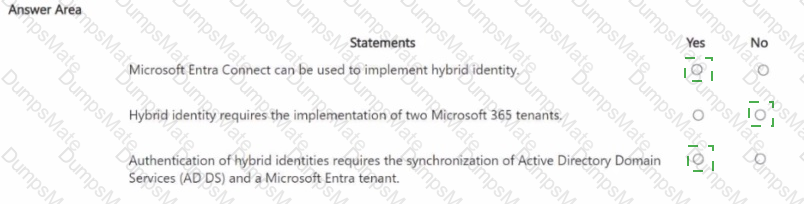
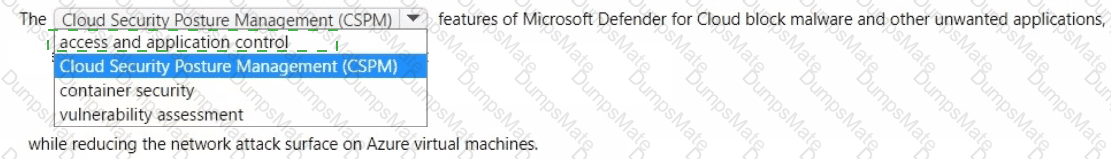
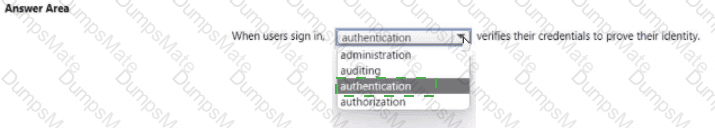
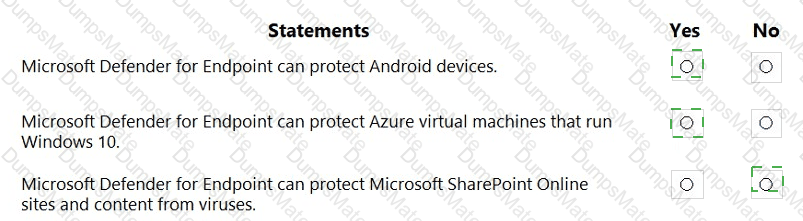
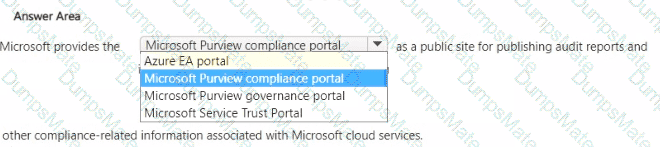
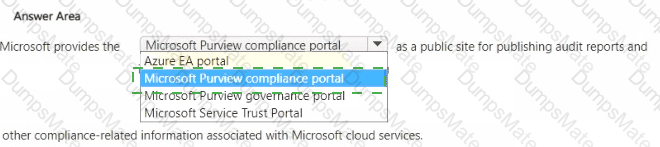
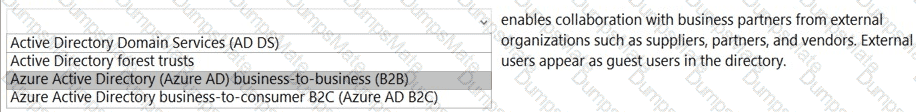
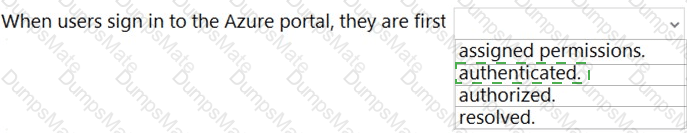
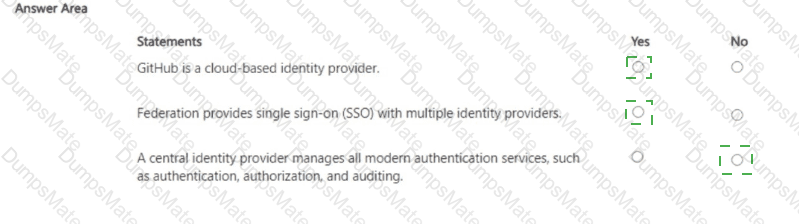
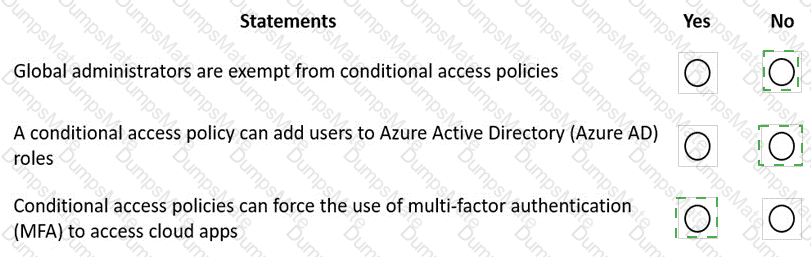
Microsoft’s shared-responsibility model states that the cloud provider secures the cloud, while the customer secures what they put in the cloud. The Azure Security documentation explains: “Regardless of the type of deployment, you always retain responsibility for your data, endpoints, accounts, and access management.” This applies to IaaS, PaaS, and SaaS, so statement 3 is Yes because the organization is always accountable for the security of information and data.
For SaaS, Microsoft describes that customers “don’t manage or control the underlying cloud infrastructure—including network, servers, operating systems, or even individual application capabilities” and that the provider handles service maintenance and updates. In SaaS, tasks like patching or applying service packs to the application code are owned by the service provider, while the customer focuses on data, identity, and access. Therefore, statement 1 is No.
For IaaS, Microsoft notes the provider manages the physical estate: “Microsoft is responsible for the physical hosts, network, and datacenter facilities,” while the customer configures and secures the guest OS, applications, and network controls within their subscription. Thus, managing the physical network is the cloud provider’s duty, making statement 2 Yes.
These SCI principles are foundational to Microsoft Learn/Docs guidance on Azure’s shared responsibility: provider—“security OF the cloud”; customer—“security IN the cloud,” with data protection always remaining the customer’s responsibility.