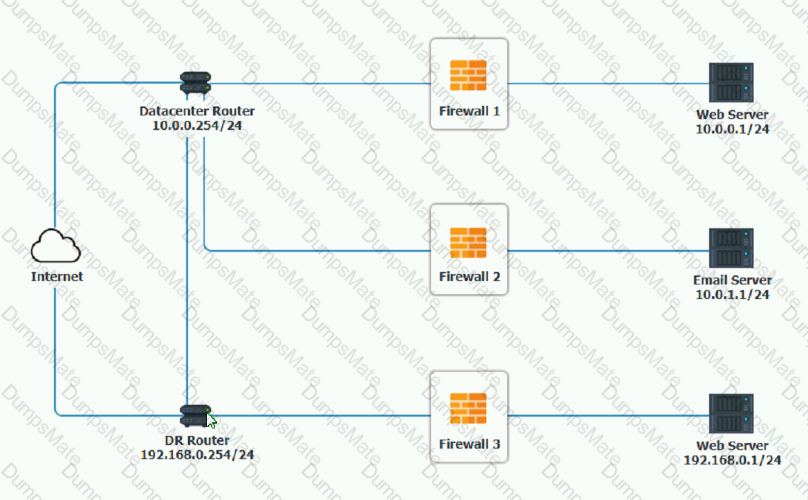
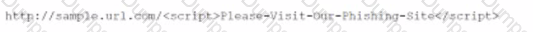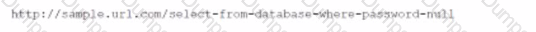Explanation: Directory traversal (also known as file path traversal) is a web security vulnerability that allows an attacker to read arbitrary files on the server that is running an application. This might include application code and data, credentials for back-end systems, and sensitive operating system files1. In some cases, an attacker might be able to write to arbitrary files on the server, allowing them to modify application data or behavior, and ultimately take full control of the server1.
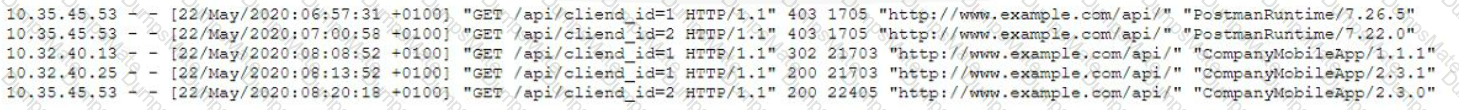
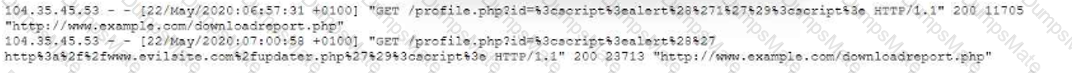
Directory traversal in its simplest form uses the …/ pattern, which means to step up one level in the directory structure. By repeating this pattern, an attacker can traverse to the root directory and then access any file or folder on the server. For example, the following request attempts to read the Unix password file /etc/passwd from the server:
http://company.com/get.php?f=/etc/passwd
Some web applications may implement some defenses against directory traversal attacks, such as filtering out …/ patterns or percent-decoding the user input before validating it. However, these defenses can often be bypassed by using variations or encoding techniques. For example, the following requests use different ways to represent …/ or / characters:
http://company.com/…%2F…%2F…%2Fetc%2Fpasswd
http://company.com/…/…/…/%2Fetc%2Fpasswd
http://company.com/%2E%2E/%2E%2E/%2E%2E/etc/passwd
These requests may still result in directory traversal attacks if the web application does not properly handle them12.
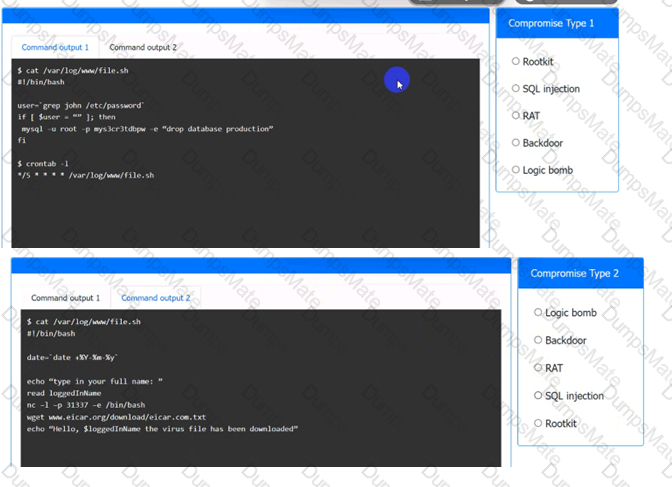
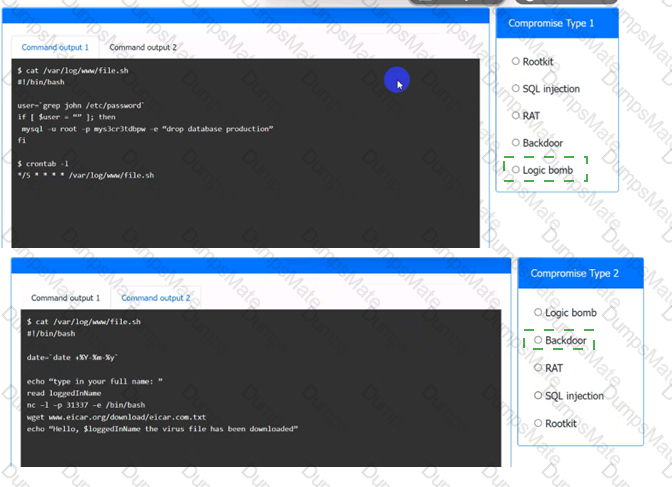
A. SQLi. This is not the correct answer, because SQLi stands for SQL Injection, which is an attack that exploits a vulnerability in a web application’s database layer, where malicious SQL statements are inserted into an entry field for execution3. The requests in the question do not contain any SQL statements or commands.
B. CSRF. This is not the correct answer, because CSRF stands for Cross-Site Request Forgery, which is an attack that exploits the trust a web server has in a user’s browser, where malicious requests are sent to the web server using the user’s credentials4. The requests in the question do not indicate that they are forged or sent by another website.
C. API attacks. This is not the correct answer, because API stands for Application Programming Interface, which is a set of rules and specifications that allow software components to communicate and exchange data. API attacks are attacks that target the vulnerabilities or weaknesses of APIs, such as authentication, authorization, encryption, rate limiting, or input validation5. The requests in the question do not target any specific API functionality or feature.
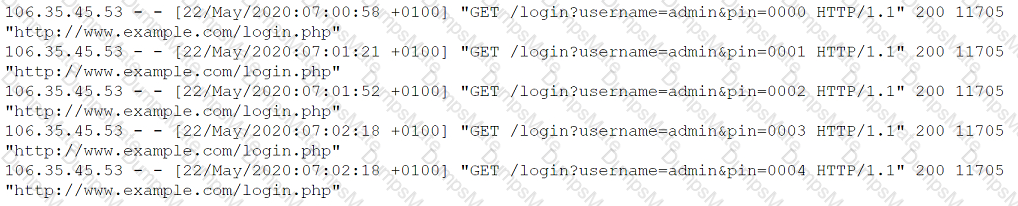
D. Directory traversal. This is the correct answer, because directory traversal is an attack that exploits insufficient security validation or sanitization of user-supplied file names, such that characters representing “traverse to parent directory” are passed through to the operating system’s file system API12. The requests in the question contain various patterns of …/ or / characters that attempt to access restricted files and directories on the server.



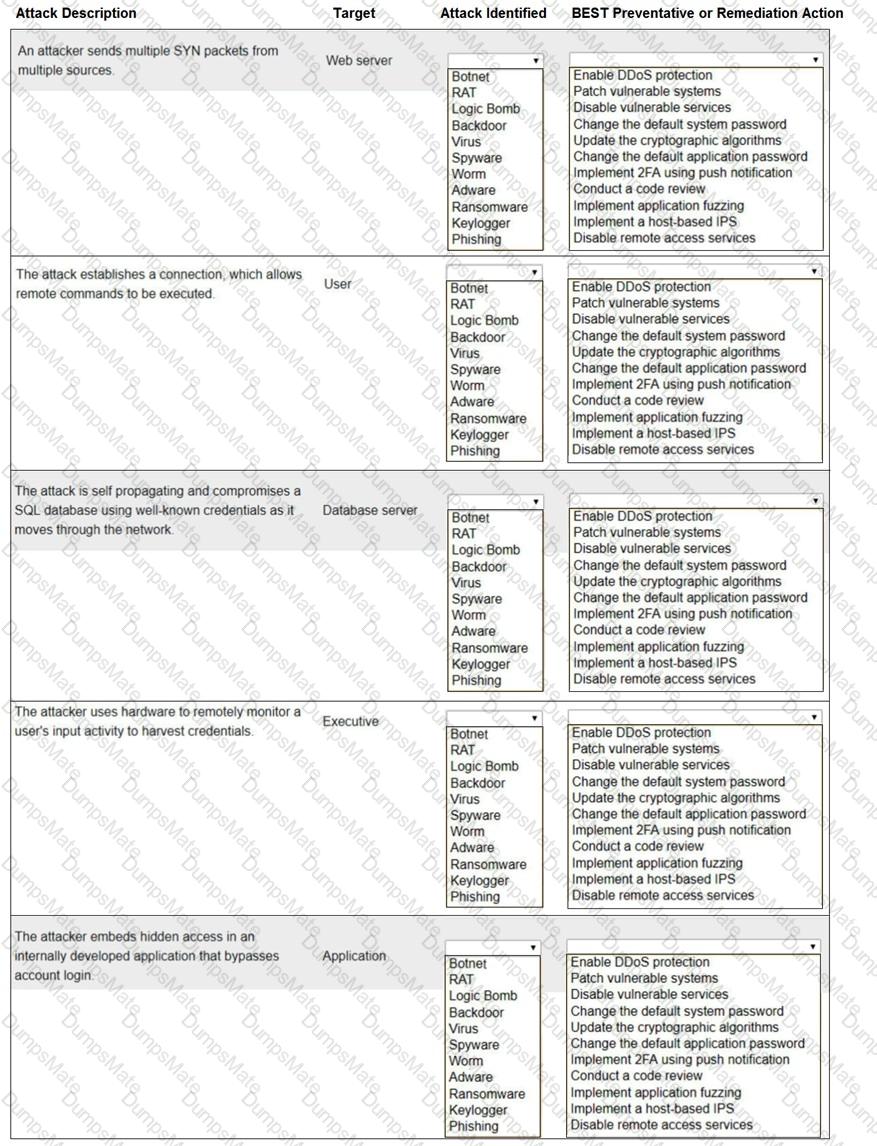
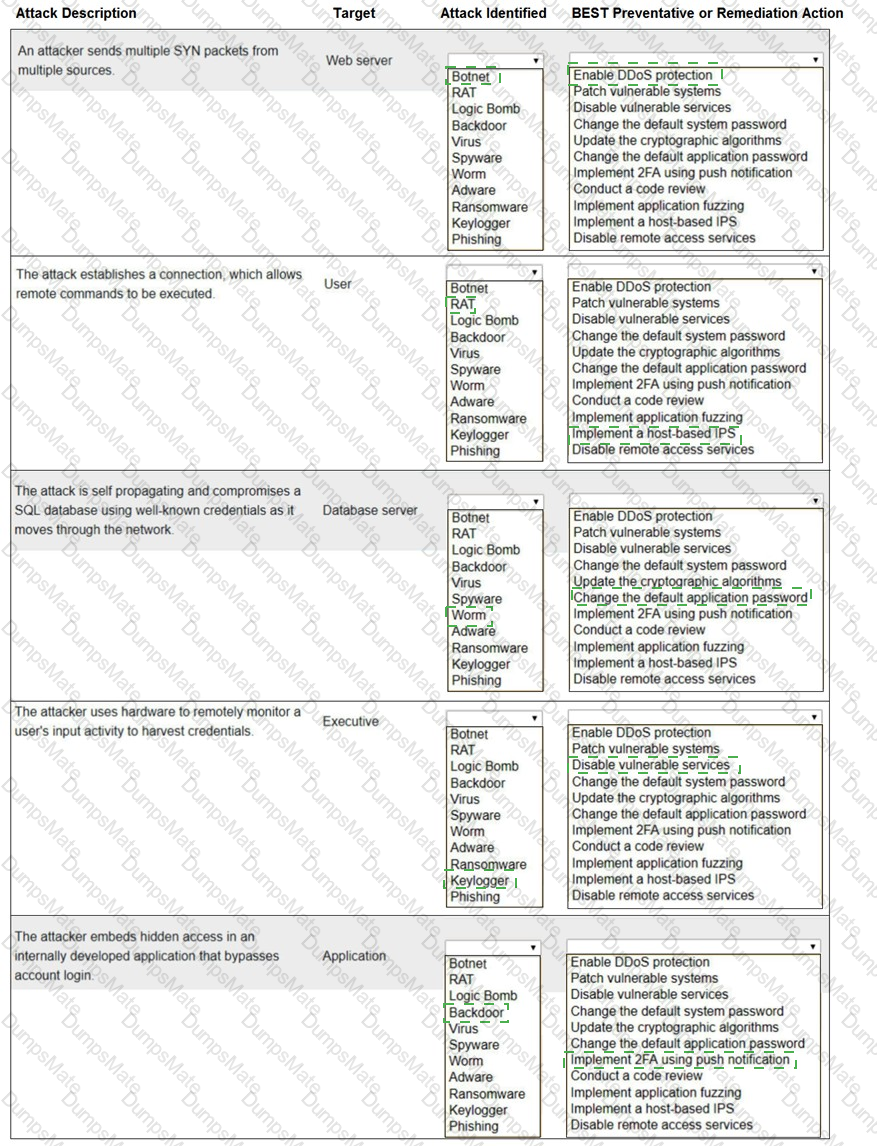
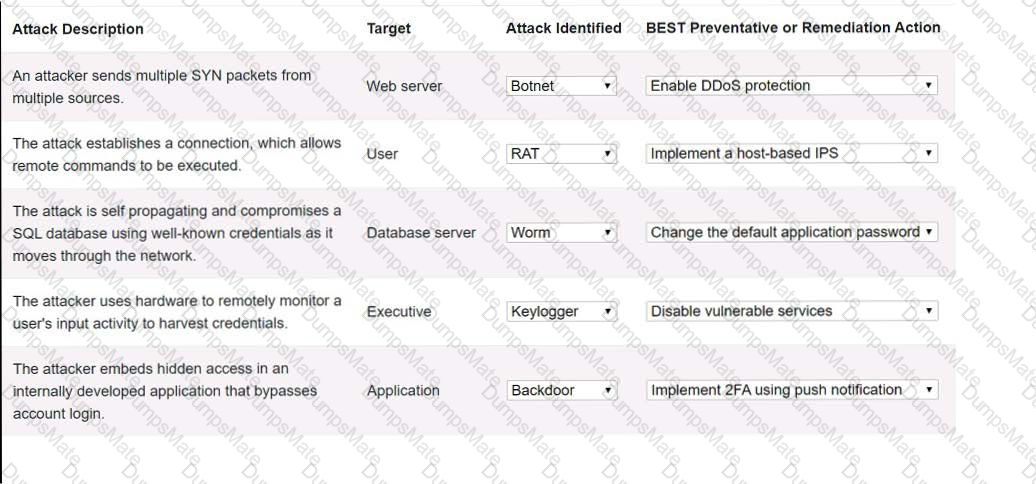 A screenshot of a computer program
Description automatically generated with low confidence
A screenshot of a computer program
Description automatically generated with low confidence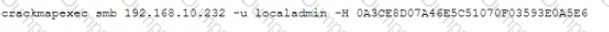

 Graphical user interface, application, website, Teams
Description automatically generated
Graphical user interface, application, website, Teams
Description automatically generated Graphical user interface, text, application
Description automatically generated
Graphical user interface, text, application
Description automatically generated