A Cortex XSIAM engineer is implementing role-based access control (RBAC) and scope-based access control (SBAC) for users accessing the Cortex XSIAM tenant with the following requirements:
Users managing machines in Europe should be able to manage and control all endpoints and installations, create profiles and policies, view alerts, and initiate Live Terminal, but only for endpoints in the Europe region.
Users managing machines in Europe should not be able to create, modify, or delete new or existing user roles.
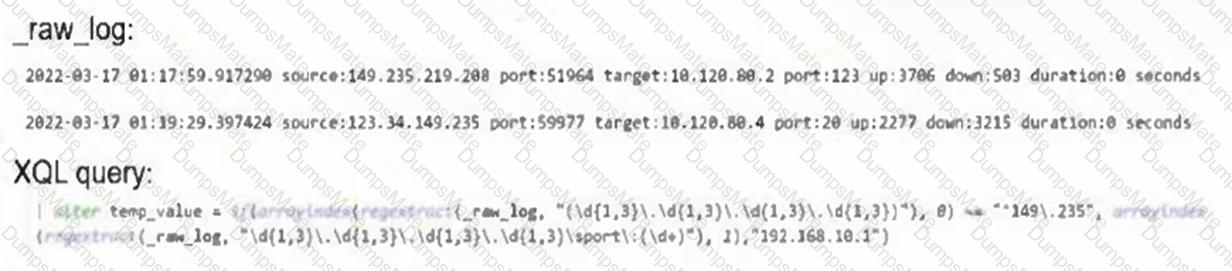
The Europe region endpoints are identified by both of the following:
Endpoint Tag = "Europe-Servers" and Endpoint Group = "Europe" for servers in Europe
Endpoint Group = "Europe" and Endpoint Tag = "Europe-Workstation" for workstations in Europe
Which two sets of implementation actions should the engineer take? (Choose two.)




 Time Schedule: Every 30 minutes
Time Schedule: Every 30 minutes Query Timeframe: 30 minutes
Query Timeframe: 30 minutes Action: Generate alert
Action: Generate alert Alert Name: No logs received from MainFW in the past 30 minutes
Alert Name: No logs received from MainFW in the past 30 minutes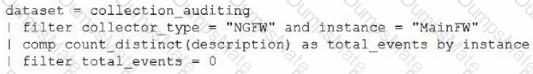

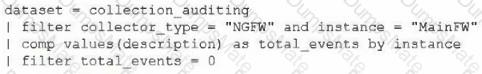

 x = X (second value of W,X,Y,Z)
x = X (second value of W,X,Y,Z) y = b (second value of a,b,c,d)
y = b (second value of a,b,c,d) z = 9 (constant for all iterations).
z = 9 (constant for all iterations).