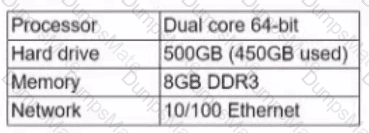
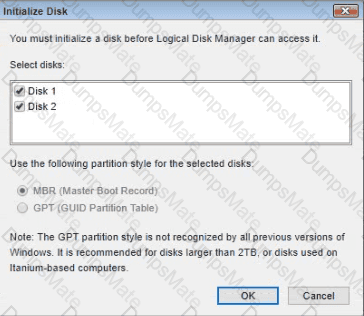
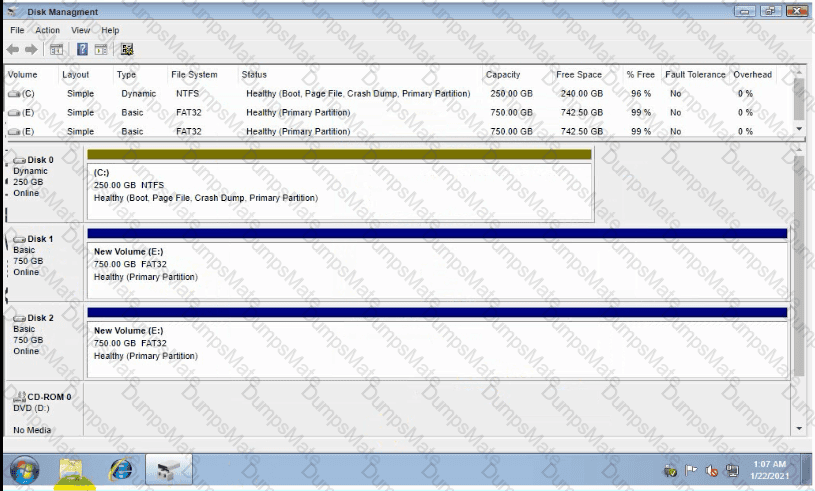
A technician has installed two new drives in a computer in the computer lab. Disk1 will be utilized for user and application data. > Disk2 has already been properly configured and has production data on it The technician has been unable to format the appropriate disk from the command prompt.
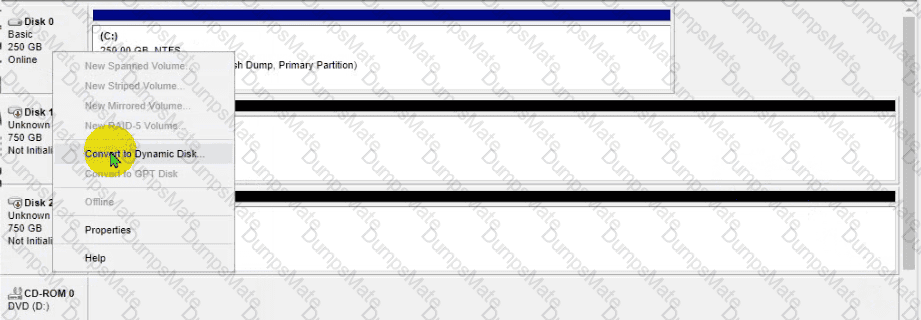
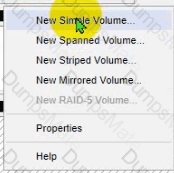
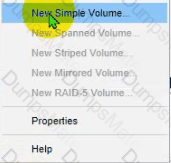
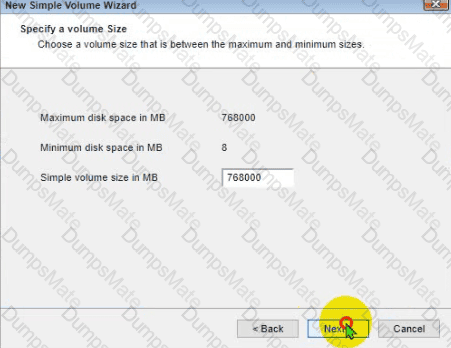
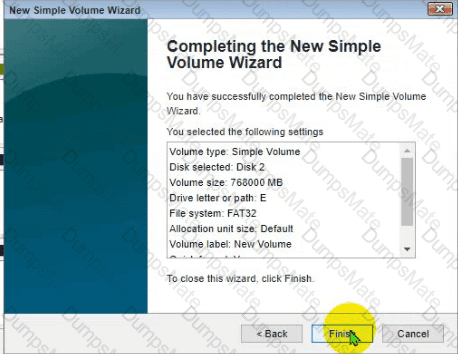
The lab requirements state that Disk1 should be a dynamic disk that contains two partitions. The first partition needs to be 256.000 MB and mapped to drive F. The , second partition needs to be 512.000 MB , and mapped to drive G.
The new partitions must be formatted to prevent each user's files from being accessed by other users, and the disk must be configured to account for future redundancy.
A consistent file system must be maintained on the machine.
INSTRUCTIONS
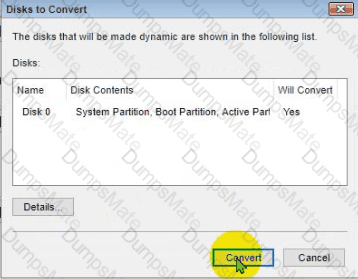
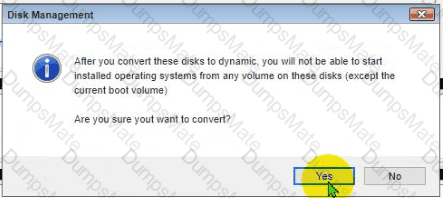
Conduct the necessary steps within the Disk Manager to accomplish these tasks
If at any time you would like to bring back the initial state of the simulation, please click the Reset Alt button